Strona blogu
In the quest for improved male performance and vitality, many have turned to supplements that promise enhanced endurance, Nitric Boost Ultra Muscle strength, and overall sexual health. One such product garnering attention is Nitric Boost Ultra Male Enhancement. This article delves into its components, benefits, and the science behind its effectiveness, offering an educational insight into why it might be the supplement men are seeking.
Understanding the Role of Nitric Oxide
At the heart of Nitric Boost Ultra's efficacy is its focus on increasing nitric oxide levels in the body. Nitric oxide (NO) is a crucial molecule in the body, primarily known for its ability to improve blood flow by dilating blood vessels. This vasodilation is particularly important in men’s health as it enhances circulation, not just to the cardiovascular system, but also to other regions, including muscles and reproductive organs. Better blood flow translates to improved oxygen and nutrient delivery, crucial for peak physical and sexual performance.
Ingredients That Make a Difference
Nitric Boost Ultra Male Enhancement typically contains a blend of natural ingredients designed to synergistically increase nitric oxide production. One common component is L-arginine, an amino acid that serves as a precursor to nitric oxide in the body. Additionally, L-citrulline is often included for its role in directly increasing L-arginine levels and subsequently NO production. These amino acids are bolstered by extracts such as Tribulus Terrestris and Fenugreek, known for their traditional use in enhancing libido and testosterone levels.
The Science Behind Male Enhancement
Research indicates that supplements enhancing nitric oxide levels can benefit men by increasing stamina and performance. Improved circulation helps in achieving and sustaining erections, thereby addressing issues like erectile dysfunction. Moreover, increased blood flow and efficient nutrient distribution support muscle growth and recovery, appealing to those looking for athletic improvements alongside sexual benefits.
It’s also important to highlight the psychological edge. As nitric oxide enhances physical performance, users often report improved confidence and mood, which are essential components of a healthy sexual life. The cumulative effect of physical and psychological improvements can transform personal and interpersonal experiences.
Safety and Considerations
While Nitric Boost Ultra Male Enhancement offers promising benefits, it’s crucial to approach it with informed caution. Individuals considering this supplement should consult healthcare professionals, especially if they have pre-existing health conditions or are taking medications that might interact with NO-boosting supplements. Overconsumption of certain ingredients like L-arginine might lead to side effects, including gastrointestinal discomfort or changes in blood pressure.
Conclusion
Nitric Boost Ultra Male Enhancement emerges as a viable option for men seeking natural enhancement methods. By leveraging the power of nitric oxide, this supplement aims to improve not only sexual performance but also overall vitality and physical endurance. However, like any supplement, it should be used responsibly and ideally complemented by a healthy lifestyle, including proper diet, regular exercise, and adequate sleep, to achieve the best results. As science continues to explore the intricacies of male enhancement, products like Nitric Boost Ultra offer a glimpse into the potential future of natural health solutions.
Мир цифровых валют открывает новые возможности. Криптовалюты становятся все распространеннее, и это не удивительно. Быстрые переводы, низкие сборы и конфиденциальность – вот лишь некоторые из достоинств использования криптовалют. Особенно заметно это явление в мире виртуальных казино, где цифровые валюты меняют игровой процесс. Чтобы найти оптимальное решение, вы можете Кэт Казино Официальный — и узнать, какие платформы заслуживают внимания. Но как выбрать лучшее веб-казино среди массы возможных предложений на рынке? Давайте попробуем разобраться вместе.
Репутация и надежность – главные факторы
Прежде всего, на чём стоит сосредоточиться при подборе веб-казино, это его репутация. Найдите отзывы остальных пользователей, изучите рейтинги и обзоры на независимых сайтах. Хорошее игровое заведение обязательно имеет разрешения от уважаемых регуляторов, таких как Мальтийское управление по азартным играм или Curacao eGaming. Например, казино сайт Cat casino может похвастаться всеми нужными разрешениями и заслуживает доверия игроков во всем мире. Имидж и надежность – это основа вашего уверенности и защищенности.
Разнообразие цифровых валют и удобные методы платежей
Лучшее интернет-казино должно поддерживать множества разных распространенных криптовалют, таких как Bitcoin, Ethereum, Litecoin и прочие. Комфорт заключается в наличии выбора, ведь каждый игрок использует разные способы платежа. Также важно проверить скорость и стабильность платежей. Моментальные депозиты и оперативные выводы средств – это то, что выделяет хорошее казино. Казино casino Cat предлагает различные способы оплаты и гарантирует быстрые переводы.
Широкий выбор игровых развлечений и надежного ПО
Широкий ассортимент игр – важный аспект для любого игрового заведения. Убедитесь, что рассматриваемое вами веб-казино предлагает широкий выбор развлечений: от традиционных барабанов до игр за столом и live-казино. Качественный софт от известных провайдеров, таких как Microgaming, AvatarUX и Ezugi, гарантирует увлекательный и честный игровой процесс. В игровом заведении Cat казино вы найдете широкий выбор развлечений на любой вкус.
Акции и промоакции – радостное дополнение
Бонусные предложения и промоакции – важная составляющая любого игрового заведения. Обратите внимание на бонусы при регистрации, программы для постоянных клиентов и постоянные предложения. Надежные веб-казино предлагают щедрые вознаграждения, которые могут существенно увеличить ваш игровой бюджет. Однако обязательно читайте правила предложений, чтобы избежать неприятных сюрпризов. Казино Кэт казино казино официальный сайт постоянно тешит клиентов крупными вознаграждениями и увлекательными мероприятиями на постоянной основе.
Поддержка клиентов – важнейший фактор
Качественная служба поддержки – еще один важный аспект. Идеальная поддержка – это та, которая работает круглосуточно и готова помочь в разрешении любых вопросов. Онлайн-чат, электронная почта – главные каналы по которым вы можете связаться с представителями департамента поддержки сервиса. Быстрые и грамотные ответы на ваши вопросы – свидетельствуют о высоком уровне проекта. В казино Cat casino онлайн в саппорте всегда готовы помочь вам в любое время суток.
Альтернативные зеркала и приложения для телефонов
Современные веб-казино должны предоставлять доступ к своим услугам независимо от обстоятельств. Использование зеркал официального сайта помогает обойти блокировки и всегда оставаться на связи. онлайн-казино Cat casino сайт предлагает удобные зеркала для беспрерывного доступа к любимым слотам. Также стоит обратить внимание на наличие приложения для мобильного, которое дает возможность играть в любимые игры в любом месте. веб-казино Кэт казино онлайн предлагает удобное и функциональное приложение для телефонов от Apple и других компаний, позволяющее играть в любое время и управлять всеми услугами платформы где угодно.
Заключение
Выбор оптимального веб-казино – проблема, требующая времени и внимания к мелочам. Следуя нашим советам, вы сможете найти казино, которое не только удовлетворит ваши потребности, но и принесёт множество удовольствия и ярких эмоций. Мир криптовалют открыт для вас – играйте ответственно и получайте удовольствие! И не забывайте, казино Кэт казино официальный всегда стремится предложить вам лучшие условия и обслуживние!
Нужно больше деталей?
На нашем сайте собраны авторские материалы по теме азартных развлечений. Откройте для себя больше по ссылке на эту ссылку. Кроме того вы можете получить персональные бонусы и обновления платформы. Не упустите шанс узнать больше!
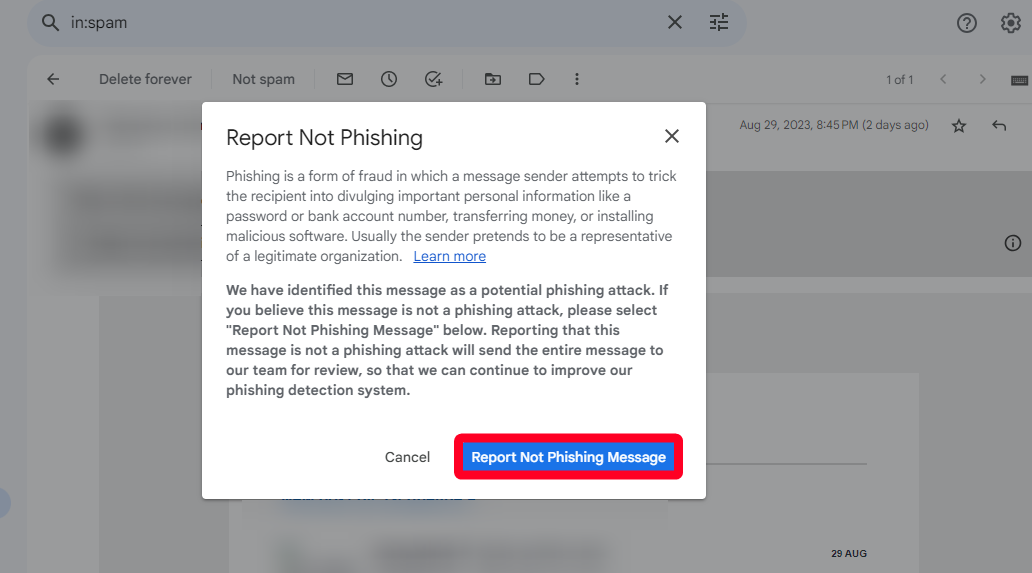
The digital landscape is often fraught with threats, with cybersecurity companies like Avast at the forefront of protecting users from online scams. In a recent incident that has garnered widespread attention, Avast's online security software erroneously classified a legitimate website as a phishing threat, sending ripples through its user community. This mix-up has raised questions about the reliability of automated cybersecurity tools, their impact on businesses, and the rights of users navigating the internet.
This mix-up has raised questions about the reliability of automated cybersecurity tools, their impact on businesses, and the rights of users navigating the internet.
The incident occurred on April 15, when users reported that Avast had blocked access to the website belonging to Legit Web, a popular platform known for its user-friendly interface and commitment to customer service. Upon trying to access the site, users were met with a stark warning from Avast, which stated that the page was a potential phishing site designed to steal personal information. This alarmed many, particularly small business owners and freelancers who relied heavily on the platform for their operations.
Following the block, a wave of complaints flooded social media as users expressed outrage. Many users stated that they felt disheartened and frustrated by the incident, emphasizing the potential loss of revenue and trust in Legit Web. "Our whole business runs on that platform, and now we have to look for alternatives," shared Maria Lopez, a graphic designer whose clientele is largely based on projects from Legit Web. "It’s not just an inconvenience; it’s detrimental to our livelihood."
In response to the rising uproar, Avast released a statement acknowledging the error. The company explained that its automated security systems rely on databases and algorithms to evaluate the safety of websites. Unfortunately, the algorithm had mistakenly flagged Legit Web due to a combination of factors, including recent changes to its URL structure and an uptick in negative reports that, upon analysis, were unfounded. The statement reassured users that the incident was being investigated and that efforts were underway to prevent such occurrences in the future.
Phishing attacks continue to be a significant concern in the cybersecurity field, with hackers constantly devising new tactics to lure unsuspecting individuals into revealing sensitive information. Consequently, security software is critical in providing users with warnings about potentially dangerous sites. However, this reliance on automated systems has a flip side, as seen in this scenario where a legitimate website is misidentified as a threat.
Experts in the field suggest that such incidents bring to light the challenges inherent in automated flagging systems. "While automated systems can process vast amounts of data quickly, there's always a margin of error," stated Dr. Michael Roberts, a cybersecurity analyst. "When these systems are mistaken, the fallout can be significant, especially for businesses that depend on their online presence. It underscores the need for a hybrid system where automated tools are supported by human oversight."
The unintended consequences of this misclassification extended beyond individual users. Legit Web's representatives reported a substantial increase in customer service inquiries, as many users were panicked by the warning and sought clarification on whether their data had been compromised. The site’s creators swiftly initiated communication with Avast to resolve the issue and ensure that users were informed about the real situation.
Online businesses thrive on trust, and an automated phishing flag can damage that trust quickly. Some business owners expressed concerns that their reputation might suffer irreparable harm due to this incident. "We’ve spent years building our brand and reputation, and now we risk losing that due to a software blunder," said Tom Harris, the CEO of Legit Web. "We hope Avast rectifies this issue quickly and reinstates our site to avoid more unnecessary damage."
In the wake of the incident, it has become increasingly essential for users to remain vigilant, understanding that while cybersecurity tools are designed to protect them, they are not infallible. VPNs, firewalls, and antivirus software provide layers of security, but the onus is also on individuals and businesses to verify the legitimacy of sites before inputting sensitive information.
Cybersecurity companies must take these missteps seriously and GOOGLE DELETE PHISING work towards systems that reduce the chances of wrongful blocks in the future. As Avast works to rectify the situation and the dust settles, users are left navigating the complexities of online threats with a newfound understanding: the fight against cybersecurity risks is a continuous battle filled with uncertainties, even from those entrusted to safeguard us.
As the story develops, users and businesses alike will be watching closely how Avast handles its response and what measures it adopts to reassure its community that they are safe in their online endeavors.
In today's digital age, phishing scams have morphed into one of the most pervasive threats to online safety, particularly for young internet users. To combat this escalating issue, the Federal Trade Commission (FTC) has introduced an innovative educational game called "On Guard Online," which is specifically designed to teach children and adolescents how to recognize and avoid phishing scams. This game stands out as a noteworthy advancement in the realm of digital education, harnessing interactive learning to foster real-world skills in internet safety.
Phishing, the malicious practice of tricking individuals into revealing sensitive information such as usernames, passwords, and credit card numbers, has evolved in complexity and sophistication. Scammers employ a variety of tactics, from seemingly harmless emails to fake websites that closely mimic legitimate services. The FTC’s On Guard Online game takes a proactive approach to equip young users with the knowledge and skills they need to identify and respond to such threats.
The foundational premise of the game is built on engaging young users through an interactive online platform. Players navigate scenarios that replicate real-life phishing attempts, including emails that tempt users with fraudulent offers and social engineering tactics in online interactions. The immersive experience of the game allows players to recognize red flags associated with phishing schemes, such as poor grammar, unusual sender addresses, or urgent calls to action. By engaging with these scenarios, players learn to apply critical thinking and analytical skills to evaluate the legitimacy of online communications.
One significant advance in On Guard Online is its integration of gamification elements that enhance user engagement while promoting retention of information. The game's design includes various levels and challenges, rewarding players for successfully identifying and reporting phishing attempts. These gamified elements not only make learning enjoyable but also reinforce essential concepts of cybersecurity in a manner that resonates with the gaming preferences of younger audiences. As players progress through higher levels, they encounter increasingly complex phishing scenarios that push them to hone their skills further—ultimately preparing them to navigate the web safely.
Additionally, On Guard Online provides educational resources that go beyond the confines of the game itself. It encourages open discussions about phishing scams among players, their peers, and family members. This aspect of the game fosters a community of learners where players can share experiences and knowledge, GOOGLE DELETE PHISING empowering them to spread awareness within their social circles. By facilitating conversations about online safety, the game serves as a bridge between formal education and everyday internet practices, thus reinforcing the importance of cybersecurity in daily life.
The game is also a tool for educators and parents, providing them with a framework to teach children about online risks. Schools can integrate On Guard Online into their curricula, offering dedicated sessions on internet safety that are both informative and interactive. Furthermore, the FTC provides educators with guides and discussion prompts that can help facilitate classroom conversations about phishing scams. This collaborative approach ensures that the lessons learned through the game have a wider impact, extending beyond individual experiences to shape collective understanding of digital safety.
Importantly, On Guard Online reflects a growing recognition of the need for proactive strategies in internet safety education. As phishing scams continue to evolve, so too must the tools available for countering them. By adopting a forward-thinking approach, the FTC has addressed a critical gap in current online safety measures. While traditional educational programs often focus on passive learning methods, the interactive gameplay of On Guard Online empowers young users to actively engage with the material, enhancing their ability to retain and apply what they learn.
In conclusion, the FTC’s On Guard Online game represents a significant advancement in the fight against phishing scams targeting young internet users. By utilizing gamification and interactive learning, the FTC not only educates players about the nuances of recognizing phishing attempts but also encourages critical thinking and community engagement around the topic. As young individuals increasingly navigate a complex digital landscape, the skills honed through playing On Guard Online are essential for fostering resilient and informed internet users. This innovative approach marks a promising step forward in enhancing digital literacy and safety, ultimately contributing to a more secure online environment for all. As technology continues to evolve, so too must our educational initiatives to ensure that the next generation is equipped to face the challenges of the digital world.
In the digital age, where information and communication flow seamlessly across platforms, cybersecurity has become a paramount concern for individuals and organizations alike. Among the myriad of threats that plague the internet, phishing stands out as one of the most nefarious tactics employed by cybercriminals. One particularly alarming trend that has emerged in recent times is the phenomenon of Google Online Challenge phishing, a sophisticated strategy that targets users by masquerading as legitimate competitions or opportunities associated with Google. Understanding how this type of phishing works and recognizing its dangers is essential for safeguarding personal and professional digital spaces.
Phishing, by definition, is a malicious attempt to obtain sensitive information from individuals by disguising as a trustworthy entity. The Google Online Challenge phishing scheme capitalizes on the legitimacy and popularity of Google's branding. Cybercriminals create fake competitions or challenges, often featuring attractive prizes such as cash rewards, gadgets, or exclusive access to events. These schemes typically entice participants with promises of high rewards for minimal effort, which effectively lures users into participating without fully vetting the authenticity of the opportunity.
One of the key mechanisms these phishing attempts employ is social engineering. By exploiting psychological triggers like curiosity, greed, and the fear of missing out (FOMO), scammers can manipulate victims into providing their personal information, such as passwords, credit card numbers, or social security numbers. Often, these phishing emails or messages will contain links that direct victims to counterfeit web pages designed to look almost identical to legitimate Google sites. This attention to detail serves to instill trust and encourages victims to enter sensitive information, believing they are participating in a genuine challenge.
To illustrate how insidious this phishing tactic can be, consider a typical scenario: an unsuspecting user receives an email claiming they have been selected as a finalist in a prestigious Google Online Challenge. The email features Google’s logo, official language, and a sense of urgency, urging them to click a link and confirm their identity to claim their prize. Upon clicking the link, they are directed to a near-perfect replica of a Google login page. Here, the user is prompted to enter their credentials, unknowingly handing over access to their Google account to the scammers.
This not only puts the individual’s personal information at risk but can also have broader implications for organizations. If an employee falls victim to such a scheme, it could compromise sensitive company data, client information, and proprietary business strategies, leading to significant financial and reputational damage.
Preventing the spread of Google Online Challenge phishing requires both technical and behavioral measures. First and foremost, education and awareness are crucial. Users should be educated about the signs of phishing attempts, such as misspellings, unusual sender addresses, and suspicious links. Organizations should implement regular training sessions to keep employees informed of the latest phishing tactics and encourage vigilance when navigating online communications.
Moreover, employing technical security measures can bolster defenses against phishing. Multi-factor authentication (MFA) adds an additional layer of security, making it more difficult for hackers to gain unauthorized access even if they have obtained login credentials. Email filters and anti-phishing software can help detect and block phishing attempts before they reach users' inboxes.
In addition, users should take advantage of Google’s security features, like the built-in phishing protection tools in Gmail, which scan messages for potentially harmful links and warn users of suspicious activity. Regularly updating passwords and using unique passwords for different platforms can also minimize the risks associated with account compromises.
Furthermore, it is vital for tech giants like GOOGLE DELETE PHISING to continually enhance their cybersecurity measures and collaborate with law enforcement to identify and apprehend cybercriminals behind these phishing schemes. Prompt reporting of phishing attempts can help in curtailing their proliferation.
In conclusion, the emergence of Google Online Challenge phishing underscores the ever-evolving nature of cyber threats. As digital interactions grow in complexity and frequency, so too does the ingenuity of cybercriminals attempting to exploit them. Vigilance, education, and robust security measures are paramount in navigating this perilous landscape. By remaining aware of the tactics employed by scammers and taking proactive steps to protect personal and organizational information, individuals can contribute to a safer online environment. The battle against phishing may be ongoing, but with collective effort and awareness, we can mitigate the damage inflicted by these malicious schemes.
Phishing, a method of cyber intrusion, has grown increasingly sophisticated and prevalent in recent years, especially targeting online banking systems. The development of phishing sites, which masquerade as legitimate banking platforms, exploits user trust to steal sensitive information such as usernames, passwords, and financial data. This article aims to dissect the underlying mechanisms of phishing site creation and explore the implications for online security.
Understanding Phishing
Phishing is a form of social engineering where an attacker impersonates a trusted entity to deceive users. Cybercriminals often target online banking customers as these platforms are prime candidates for monetary gains. The success of phishing attacks hinges on several factors including the efficacy of the fake website, the method of traffic redirection, and user perception.
Components of a Phishing Site
Creating a phishing site involves several critical components. Below is a breakdown of the attributes that characterize an effective phishing site:
- Domain Name Registration:
- Website Design:
- Backend Setup:
- Traffic Generation:
- Email Campaigns: Sending mass emails to potential victims that appear to be from the legitimate bank, often including messages of urgency, such as a security alert requiring immediate action.
- Social Media and Instant Messaging: Utilizing social platforms to spread links to the phishing site.
- Search Engine Optimization (SEO): Manipulating search engine results to make the phishing site appear legitimate.
- SSL Certificates:
- Data Retrieval:
Legal and Ethical Implications
From a legal standpoint, creating phishing sites is a serious crime in virtually every jurisdiction. Data theft, identity fraud, and financial scams can lead to severe punishments, including imprisonment. However, understanding these mechanisms can be invaluable for cybersecurity professionals aiming to better defend against such attacks.
Countermeasures Against Phishing
As phishing tactics evolve, so too do the countermeasures. Key strategies to combat phishing include:
- User Education: Regular training programs should be established to inform users about phishing tactics, warning them to scrutinize unusual emails or GOOGLE DELETE PHISING messaging that prompts them for personal data.
Conclusion
The creation of phishing sites represents a significant threat to the cybersecurity landscape of online banking. As tactics become more advanced and results more lucrative, users and institutions alike must collaborate to implement stringent security measures and foster a culture of caution. By recognizing the methods and motivations of cybercriminals, stakeholders can better defend against this pervasive form of digital deception.
Understanding Adjustable Walkers: A Comprehensive Guide
Adjustable walkers are important mobility aids developed to provide stability and assistance to individuals with mobility obstacles. They improve self-reliance, safety, and confidence for people recovering from surgical treatment, dealing with persistent conditions, or facing age-related mobility issues. This post explores the features, types, benefits, and typical FAQs associated Uplivin Trive Rollator with Seat - Easy Mobility adjustable walkers, providing insights for prospective users and caregivers.
What is an Adjustable Walker?
An adjustable walker is a mobility aid that typically includes a lightweight Walking Frame with 4 legs, equipped with handgrips for support. It can be changed to accommodate various heights, making sure users achieve a comfortable wrist position while supporting their weight. Adjustable walkers been available in various styles, each tailored to particular requirements.

Secret Features of Adjustable Walkers
- Height Adjustment: Most adjustable walkers have telescoping legs, enabling users to quickly customize the height to fit their stature.
- Weight Capacity: Different models accommodate varying weight limits, dealing with a broad market.
- Foldability: Many walkers are collapsible, making them easy to shop and transportation.
- Wheels vs. No Wheels: Some walkers include wheels on the front legs, while others have a fundamental style without wheels, promoting stability.
- Extra Accessories: Walkers can often be geared up with trays, baskets, or cup holders for included convenience.
| Function | Description |
|---|---|
| Height Adjustment | Telescoping legs for customized height settings |
| Weight Capacity | Differs by design, supporting different body weights |
| Foldability | Collapsible style for easy transportation and storage |
| Wheels | Readily available in both wheeled and non-wheeled options |
| Extra Accessories | Trays, baskets, and cup holders for user convenience |
Kinds Of Adjustable Walkers
- Standard Walkers: Traditional designs with 4 legs. Best for those seeking maximum stability.
- Wheeled Walkers (Rollators): Walkers with 2 or more wheels, enabling for much easier maneuvering.
- Hemi Walkers: Designed for individuals with making use of one hand, including a single arm support for included stability.
- Child Walkers: Specifically developed for babies discovering to stroll, promoting safety and support throughout early mobility.
Benefits of Using Adjustable Walkers
Increase Independence
- Boosted Mobility: Adjustable walkers allow users to navigate their environments with more ease and self-confidence, promoting a sense of independence.
- Ease of access: With the ideal walker, users can keep their lifestyle and participate in activities they enjoy without support.
Injury Prevention
- Stability and Support: Walker users can maintain much better balance and avoid falls, which are particularly important for seniors and individuals recovering from surgery.
- Minimized Strain: Proper use of a walker can reduce tension on joints and muscles, reducing the danger of injury during mobility.
Convenience and Customization
- Adjustable Settings: Walkers can be customized to each user's height and comfort, using a more individualized experience.
- Extra Features: Options for devices help in accommodating individual needs, enabling users to carry products while moving.
Costs and Considerations
The cost of adjustable walkers varies depending upon features, products, and brand name. Here's an introduction of the typical expenses connected with various types:
| Walker Type | Typical Cost |
|---|---|
| Standard Walkers | ₤ 50 - ₤ 100 |
| Wheeled Walkers | ₤ 75 - ₤ 200 |
| Hemi Walkers | ₤ 60 - ₤ 150 |
| Infant Walkers | ₤ 30 - ₤ 70 |
Frequently Asked Questions (FAQs)
1. How do I know which adjustable walker is right for me?
The right adjustable walker depends on your specific needs, physical condition, and environment. It's necessary to consult a healthcare professional to figure out the most ideal type.
2. Can I change the height of any walker?
Most adjustable walkers feature a height-adjustment system. Nevertheless, not all walkers are adjustable. It's crucial to take a look at product specifications before buying.
3. Are wheeled walkers safe to use?
Yes, wheeled walkers (or rollators) are safe for users who can browse them appropriately. They typically consist of brakes for included safety when stationary.
4. How do I take care of my adjustable walker?
Regular Elite Care X Cruise Lightweight HOMCOM Folding 4-Wheel Walker with Seat & Bag Walker (visit my web site) involves cleaning up the walker with mild soap and water, looking for wear on grips and wheels, and ensuring systems operate smoothly.
5. Can I take my adjustable walker on public transport?
Yes, lots of adjustable walkers are foldable and created for simple transportation. Nevertheless, it's suggested to examine the particular guidelines of the transportation service.
6. Do I need assistance to use an adjustable walker?
Many users can operate adjustable walkers individually, particularly when effectively fitted to their height. Nevertheless, those with extreme mobility issues might take advantage of help.
Adjustable walkers are vital tools for enhancing mobility, independence, and safety. With a range of design and styles, individuals can discover a walker tailored to their needs. Caretakers and users alike need to appreciate the value of consulting healthcare professionals to make informed decisions regarding mobility aids. Understanding the features, benefits, and considerations of adjustable walkers empowers individuals to keep an active lifestyle, enriching their lifestyle in spite of mobility obstacles.
After 30 days, participants showed a significant balancing of glucose levels while the placebo group, who received a shake without the beneficial microbes, showed no change1. In one study published in Lipids in Health and Disease, researchers at Brazil’s São Paulo State University gave volunteers a daily shake containing Lactobacillus acidophilus and Bifidobacterium bifidum. In stopping this part of the trial, Nabel accepted the recommendation of the 10-member Data and Safety Monitoring Board (DSMB) - an independent advisory group of experts in diabetes, cardiovascular disease, epidemiology, patient care, biostatistics, medical ethics, and clinical trial design that has been monitoring ACCORD since it began. Although this can be frustrating, it rarely creates a medical emergency. If you suffer from hypo- or hyperglycemia, or any other complications of diabetes, and require medical equipment to help treat and alleviate symptoms, Wound Care Solutions can help. American Diabetes Association. 14. Management of diabetes in pregnancy: Standards of medical care in diabetes-2020. Provides weight management support as part of a healthy lifestyle with a reduced-calorie diet and regular exercise.
Consensus statement by the American association of clinical endocrinologists and American college of endocrinology on the comprehensive type 2 diabetes management algorithm - 2019 executive summary. American Diabetes Association. 6. Glycemic Targets: Standards of Medical Care in Diabetes-2020. American Diabetes Association (ADA). And if your blood sugar is high, you might notice the signs and symptoms of diabetes - such as increased thirst and urination, fatigue, and blurred vision. The extract of the Banaba tree’s leaf has long been used in India and the Philippines as a natural way to help maintain healthy blood sugar levels in the normal range, where they belong. These organisms may be microscopic, but they outnumber human cells in the body by 10 to 1 and play an integral role in supporting many of your body’s critical functions-like maintaining healthy blood sugar levels already within the normal range. But, did you know that beneficial microbes-or probiotics-also help to maintain your healthy Lifeline 365 Blood Review sugar levels already in a normal range? A blood sugar range of 70-99 mg/dl before meals is considered normal. Carb counting is a popular method used to manage blood sugar levels by monitoring the amount of carbohydrates you consume throughout the day.

Indeed, several studies demonstrate probiotics’ abilities to support healthy blood sugar levels. Studies indicate that Banaba leaf extract has a safe, insulin-like effect on the body and can help keep healthy blood sugar levels. Other compounds in Banaba leaf, called ellagitannins, provide antioxidant benefits in addition to working with corosolic acid to maintain healthy glucose levels. Due to this, the blood sugar levels in the body rise in turn causing damage to different body parts. We have received no complaints about betabeat blood sugar supplement so far. Taking a high-quality probiotic supplement can deliver some of the most beneficial species of gut bacteria deep into your digestive tract, putting them in the perfect position to support your overall health. Using a patented delivery method called BIO-tract®, Glucose Support delivers the probiotics live deep into your gut, where they are time-released over an 8-10 hour period-giving them 15x more survivability than standard capsules. Although there is still much to discover about the role of the microbiome and the microorganisms that dwell within it, researchers are learning that the majority of your microbes help to produce proteins and metabolites that interact with and support your body’s cells and organs on many levels.
You want to make sure that you are still helping your body by taking it and not putting yourself in harm’s way. In fact, scientists are still puzzling out all of the jobs that these little guys juggle within the human body. You see, when there aren’t enough good guys in your gut, your microbes might not be properly communicating with your cells-which can make maintaining healthy glucose levels more challenging. Because the fiber in healthy carbs like whole grains, beans, fruits and starchy veggies help balance your blood sugar levels by slowing the absorption and release of sugar (glucose) into your bloodstream. These contain carbs and will increase your blood sugar levels. What Happens to Sugar Levels in the Blood While Fasting? To keep your blood sugar under control, you may need to cut back on foods and Health Charm Blood Sugar Gluco Maxum Review drinks that are high in carbs. Diabetes may be uncontrolled because it is undiagnosed, the current treatment is ineffective, or there's a lack of compliance with treatment.
In the age of digital communication, online phishing has emerged as one of the most persistent and damaging threats to personal and organizational security. Phishing is a form of cybercrime where attackers attempt to deceive individuals into providing sensitive information such as usernames, passwords, credit card numbers, and bank details. This article will delve into the mechanics of phishing attacks, their various forms, the impact they have on individuals and organizations, and measures that can be taken to protect against such threats.
What is Phishing?
Phishing typically involves an attacker masquerading as a trustworthy entity in electronic communications. The most common vector for phishing attacks is email, where the attacker sends messages that appear to be from legitimate sources, such as banks, online service providers, or well-known brands. These emails often contain links to fraudulent websites designed to look like the legitimate ones, tricking victims into entering their personal information.
While phishing is historically linked to email, the problem has evolved over the years. Attackers now use various methods to reach victims, including social media platforms, instant messaging, and even phone calls, adding a layer of complexity to detection and prevention.
Different Types of Phishing
- Spear Phishing: Unlike traditional phishing attacks that target a large number of people, spear phishing is personalized and aims at specific individuals or organizations. Attackers may gather information from social media profiles or other publicly available resources to create tailored messages that increase the likelihood of success.
The Impact of Phishing
The consequences of phishing can be severe. For GOOGLE DELETE PHISING individuals, falling victim to a phishing attack can result in identity theft, financial loss, and significant emotional distress. For organizations, the ramifications are even graver—data breaches can lead to substantial financial losses, erosion of customer trust, legal penalties, and damage to brand reputation. According to a report from cybersecurity firms, phishing accounts for a majority of data breaches. Organizations have found themselves investing heavily in cyber defense mechanisms as a direct response to these threats.
Recognizing Phishing Attempts
Spotting a phishing attempt can be challenging, especially as attackers constantly refine their techniques. However, there are several red flags that can help individuals and organizations identify potential phishing attempts:
- Unusual Sender Email Addresses: Attackers often create email addresses that closely resemble legitimate ones but may contain subtle misspellings or additional characters.
Prevention Measures
To effectively combat phishing, individuals and organizations must adopt a proactive approach. Here are some best practices:
- Education and Training: Regular training sessions on identifying phishing attacks can equip employees with the knowledge they need to recognize threats before they escalate.
Conclusion
As the digital landscape continues to evolve, so do the tactics employed by cybercriminals. Phishing remains one of the most common and dangerous forms of cyberattacks, but by understanding the methods used, recognizing warning signs, and implementing effective preventive measures, both individuals and organizations can defend against this pervasive threat. Awareness and vigilance are essential in safeguarding sensitive information in today's interconnected world.
Severe hypoglycemia can be life-threatening if a person does not receive treatment. Bottom line, the appropriate blood sugar level varies from person to person. If you are worried about what fluctuating levels can mean for your health, visit your doctor to discuss strategies for keeping your blood sugar at the appropriate level. What does a high blood sugar/glucose level mean? If insulin is prescribed, your doctor will show you how, when, and how much you would need if ever your blood sugar is high. Results showed that people with lower blood glucose levels were able to remember more words compared to people with high blood sugar. Sage leaves have long been used as a remedy against diabetes, with research suggesting they could help lower blood sugar levels. Diet is key when trying to lower blood sugar. A non-diabetic hypoglycemia diet can help keep blood sugar levels balanced. The liver then releases glucose back into the bloodstream to normalize blood sugar levels.
Insulin helps the body’s cells to absorb sugar from the bloodstream. If a person has a problem with their kidneys, medication can build up in their bloodstream. The kidneys help the body process medication and excrete waste. In people without diabetes, hypoglycemia can result from the body producing too much insulin after a meal, causing blood sugar levels to drop. Blood sugar levels below 70 mg/dl can indicate hypoglycemia. According to the American Diabetes Association, blood glucose levels below 70 mg/dl could lead to a condition known as hypoglycemia. A recent study published in the journal Neurology determined that lower blood sugar levels could prevent memory loss. People with lower blood sugar also displayed higher levels of activity in the hippocampus. After each participant’s blood glucose levels were monitored, participants were asked to complete a test by recalling a list of 15 words they had heard 30 minutes ago. If the doctor suspects hypoglycemia, they may perform a blood test.
You may have appointments with specialists (like a cardiologist) in addition to your primary care visits. That sounds like excellent starting advice. Shortness of breath, breath that smells like fruit, nausea, vomiting and dry mouth are symptoms of ketoacidosis. Hypoglycemia’s symptoms include nausea, anxiety, mood changes, fatigue, dizziness, trouble sleeping, and Stimula Blood Sugar Ingredients even seizures. This has resulted in astronomically better outcomes for people with diabetes, and closed-loop control is around the corner that will improve things even further.Diabetes is unique in the amount of measurement and control we have over the feedback loops at play, but it doesn’t have to be. Although Dr. Flöel and her colleagues are confident that lower blood sugar levels equate to better memory skills, keeping blood glucose levels at an even keel is still important to our health. When a person’s blood sugar levels are low, the pancreas releases a hormone called glucagon. When levels fall too low, the body does not have enough energy to function fully. For Gluco Maxum adults with long-standing type 2 diabetes who have or are at risk for cardiovascular disease, intensively lowering blood sugar to near-normal levels appears to be too risky. While it’s always important to maintain healthy blood sugar levels, new research shows that better control during the first year can reduce the future risk for complications, including kidney disease, eye disease, stroke, heart failure and poor circulation to the limbs.
The first year after diagnosis is a crucial time for patients with Type 2 diabetes. A new study, led by Neda Laiteerapong, MD, assistant professor of medicine at the University of Chicago, analyzed Health Charm Blood Sugar Review records of more than 34,000 patients to review their hemoglobin A1C (HbA1C) values in the years after their initial diagnosis. ’s lead author Agnes Flöel, M.D., of Charité University Medicine in Berlin, Germany. She is the creator of the cleanse, "S.O.U.P. - Superfoods. Organic. Uniquely designed. Prepared with Love." Goodman is also the author of Cancer Hacks, a best-selling story about her journey with cancer. Plus, fatty fish is an excellent source of protein that will help you feel full and Glyco Boost Supplement manage your weight with ease. The above mentioned herbal cure prepared from the extract of herbs and plant products could lower blood glucose effectively in people and hence, provides the most effective ways to people who want to know how to treat diabetes mellitus problem with ease. In people with diabetes, taking too much insulin can cause blood sugar levels to drop too low. Treatments focus on returning blood sugar to safe levels. This type of buildup can change blood sugar levels and lead to hypoglycemia.
