Strona blogu
In the digital age, where information and communication flow seamlessly across platforms, cybersecurity has become a paramount concern for individuals and organizations alike. Among the myriad of threats that plague the internet, phishing stands out as one of the most nefarious tactics employed by cybercriminals. One particularly alarming trend that has emerged in recent times is the phenomenon of Google Online Challenge phishing, a sophisticated strategy that targets users by masquerading as legitimate competitions or opportunities associated with GOOGLE DELETE PHISING. Understanding how this type of phishing works and recognizing its dangers is essential for safeguarding personal and professional digital spaces.
Phishing, by definition, is a malicious attempt to obtain sensitive information from individuals by disguising as a trustworthy entity. The Google Online Challenge phishing scheme capitalizes on the legitimacy and popularity of Google's branding. Cybercriminals create fake competitions or challenges, often featuring attractive prizes such as cash rewards, gadgets, or exclusive access to events. These schemes typically entice participants with promises of high rewards for minimal effort, which effectively lures users into participating without fully vetting the authenticity of the opportunity.
One of the key mechanisms these phishing attempts employ is social engineering. By exploiting psychological triggers like curiosity, greed, and the fear of missing out (FOMO), scammers can manipulate victims into providing their personal information, such as passwords, credit card numbers, or social security numbers. Often, these phishing emails or messages will contain links that direct victims to counterfeit web pages designed to look almost identical to legitimate Google sites. This attention to detail serves to instill trust and encourages victims to enter sensitive information, believing they are participating in a genuine challenge.
To illustrate how insidious this phishing tactic can be, consider a typical scenario: an unsuspecting user receives an email claiming they have been selected as a finalist in a prestigious Google Online Challenge. The email features Google’s logo, official language, and a sense of urgency, urging them to click a link and confirm their identity to claim their prize. Upon clicking the link, they are directed to a near-perfect replica of a Google login page. Here, the user is prompted to enter their credentials, unknowingly handing over access to their Google account to the scammers.
This not only puts the individual’s personal information at risk but can also have broader implications for organizations. If an employee falls victim to such a scheme, it could compromise sensitive company data, client information, and proprietary business strategies, leading to significant financial and reputational damage.
Preventing the spread of Google Online Challenge phishing requires both technical and behavioral measures. First and foremost, education and awareness are crucial. Users should be educated about the signs of phishing attempts, such as misspellings, unusual sender addresses, and suspicious links. Organizations should implement regular training sessions to keep employees informed of the latest phishing tactics and encourage vigilance when navigating online communications.
Moreover, employing technical security measures can bolster defenses against phishing. Multi-factor authentication (MFA) adds an additional layer of security, making it more difficult for hackers to gain unauthorized access even if they have obtained login credentials. Email filters and anti-phishing software can help detect and block phishing attempts before they reach users' inboxes.
In addition, users should take advantage of Google’s security features, like the built-in phishing protection tools in Gmail, which scan messages for potentially harmful links and warn users of suspicious activity. Regularly updating passwords and using unique passwords for different platforms can also minimize the risks associated with account compromises.
Furthermore, it is vital for tech giants like Google to continually enhance their cybersecurity measures and collaborate with law enforcement to identify and apprehend cybercriminals behind these phishing schemes. Prompt reporting of phishing attempts can help in curtailing their proliferation.
In conclusion, the emergence of Google Online Challenge phishing underscores the ever-evolving nature of cyber threats. As digital interactions grow in complexity and frequency, so too does the ingenuity of cybercriminals attempting to exploit them. Vigilance, education, and robust security measures are paramount in navigating this perilous landscape. By remaining aware of the tactics employed by scammers and taking proactive steps to protect personal and organizational information, individuals can contribute to a safer online environment. The battle against phishing may be ongoing, but with collective effort and awareness, we can mitigate the damage inflicted by these malicious schemes.

Understanding and Repairing Bifold Door Brackets: A Comprehensive Guide
Bifold doors are a flexible and space-saving option for both property and commercial spaces. They are commonly used in closets, pantries, and room dividers due to their capability to fold nicely and use up minimal space when open. However, like any mechanical system, bifold doors can experience wear and tear gradually, particularly at the hinges and brackets. This article explores the significance of bifold door brackets, typical problems that occur, and detailed directions for repairing them.
The Importance of Bifold Door Brackets
Bifold door brackets are important components that support the weight of the door panels and ensure smooth operation. These brackets are generally attached to the top and bottom of the door frame and are accountable for assisting the doors as they fold and unfold. Without effectively operating brackets, bifold doors can become misaligned, difficult to open and close, or even fall off the track.
Typical Issues with Bifold Door Brackets
- Loose or Damaged Brackets: Over time, the screws that hold the brackets in place can loosen, causing the doors to droop or become misaligned.
- Damaged Hinges: The hinges within the brackets can use out, resulting in creaking sounds and lowered functionality.
- Misaligned Tracks: If the tracks are not correctly aligned, the brackets might not operate properly, causing the doors to bind or stick.
- Rust and Rust: Exposure to wetness can cause brackets to rust, which can deteriorate their structural integrity and cause failure.
Tools and Materials Needed for Repair
Before you start the repair procedure, gather the following tools and materials:
- Screwdriver (Phillips and flathead)
- Drill and drill bits
- Adjustable wrench
- Lubing oil (such as WD-40)
- Replacement brackets (if necessary)
- Sandpaper (for rust removal)
- Paint or rust-resistant finishing (if needed)
Step-by-Step Guide to Repairing Bifold Door Brackets
Examine the Brackets and Tracks
- Step 1: Open the bifold doors completely and examine the brackets and tracks for any visible damage, loose screws, or misalignment.
- Action 2: Check the hinges within the brackets for wear and tear. Look for indications of rust, creaking, or tightness.
Tighten Up Loose Screws
- Step 1: Use a screwdriver to tighten up all screws on the brackets. Start from the top brackets and work your method down to the bottom.
- Action 2: If any screws are removed or harmed, remove them and use a drill to produce brand-new holes. Replace the screws with brand-new ones.
Oil the Hinges
- Step 1: Apply a couple of drops of lubricating oil to the hinges within the brackets. Move the doors backward and forward to distribute the oil uniformly.
- Action 2: Wipe away any excess oil with a tidy cloth to avoid it from dripping onto the floor or other surfaces.
Align the Tracks
- Action 1: If the tracks are misaligned, use an adjustable wrench to loosen up the screws that hold the track in location.
- Step 2: Gently adjust the track to guarantee it is level and straight. Retighten the screws to protect the track in its brand-new position.
Replace Damaged Brackets
- Step 1: If any brackets are damaged beyond repair, remove them by unscrewing the screws that hold them in location.
- Step 2: Install the new brackets in the exact same position, ensuring they are securely attached with brand-new screws.
Remove Rust and Apply Protective Coating
- Step 1: Use sandpaper to eliminate any rust from the brackets and tracks. Sand till the surface is smooth and totally free of rust.
- Action 2: Apply a rust-resistant finishing or paint to the brackets and tracks to avoid future corrosion.
Test the Doors
- Action 1: Once all repairs are complete, evaluate the Bifold Door Restorers doors by opening and closing them several times. Guarantee they move efficiently and are effectively lined up.
- Step 2: Make any final modifications as needed to ensure ideal performance.
Frequently asked questions
Q: How frequently should I examine and keep my bifold door brackets?A: It is suggested to check and maintain your bifold door hardware repair door brackets at least when a year. Nevertheless, if you see any indications of wear or breakdown, it is best to deal with the concern right away to prevent more damage.
Q: Can I lube the hinges with any kind of oil?A: While any type of oil can supply some lubrication, it is best to utilize a premium lubricating oil such as WD-40. This type of oil is specifically designed to lower friction and avoid rust, making it perfect for bifold door hinges.
Q: What should I do if the tracks are bent or damaged?A: If the tracks are bent or damaged, it might be needed to replace them. Seek advice from the producer's directions or a professional for assistance on how to replace the tracks.
Q: Can I paint over rust on the brackets?A: It is not recommended to paint over rust. Rust can continue to spread under the paint, leading to additional damage. Always eliminate rust with sandpaper before using a protective coating or paint.
Q: Are there any preventive measures I can require to extend the life of my bifold door repair cost door brackets?A: Yes, regular maintenance is crucial. Keep the brackets and tracks clean and complimentary of particles. Lube the hinges routinely, and look for loose screws or indications of wear. Deal with any concerns immediately to avoid more serious issues.
bifold door maintaining tips door brackets are vital for the smooth operation and longevity of your bifold door hinge replacement doors. By comprehending typical issues and following the steps detailed in this guide, you can effectively repair and keep your bifold door repair cost door brackets. Regular maintenance and timely attention to any signs of wear will make sure that your bifold doors continue to operate properly for years to come.

Folding Mobility Scooters in the UK: An Informative Guide
Mobility scooters have actually transformed the way individuals with mobility problems navigate their environments, providing the freedom and self-reliance they should have. Amongst different kinds of mobility options readily available, folding mobility scooters have acquired considerable popularity in the UK for their usefulness and easy to use functions. In this article, we will check out the different aspects of folding mobility scooters, their advantages, considerations for purchase, and popular models readily available in the UK market.
Comprehending Folding Mobility Scooters
Ability Superstore Curlew Folding Electric Scooter - Purple mobility scooters are compact, lightweight lorries designed to help people with minimal mobility in getting around with ease. Unlike traditional mobility scooters, these models fold into a more portable mobility scooters shape, making them a perfect choice for those who travel, have restricted storage area, or live in compact dwellings.
Secret Features of Folding Mobility Scooters
- Compact Design: These scooters are created to fold to a small size, enabling uncomplicated storage in the boot of a car or in little living spaces.
- Lightweight Construction: Typically made from lightweight materials, folding scooters are easy to lift and maneuver, mymobilityscooters making them best for those with strength restrictions.
- Ease of Use: With basic folding mechanisms and intuitive controls, these scooters are accessible to individuals of differing mobility levels.
- Portability: Ideal for travel, folding scooters can be handled public transport or aircrafts, making sure users maintain their self-reliance anywhere they go.
Benefits of Folding Mobility Scooters
Folding mobility scooters use various benefits that make them an appealing choice for users in the UK.

Benefits Include:
- Enhanced Mobility: Users can browse both indoor and outdoor areas with ease, lowering seclusion and encouraging a more active way of life.
- Convenience: The Ability Superstore Curlew Folding Electric Scooter - Purple to fold and save the scooter effortlessly helps users in their daily activities, such as shopping and checking out buddies.
- Price: Many folding scooters are competitively priced, providing economical services for foldable mobility scooter requirements.
- Adjustable Options: Various models provide features such as adjustable seats, armrests, and accessories, enabling a customized experience.
- Security Features: Many folding scooters come equipped with functions such as lights, horn, anti-tip wheels, and easy braking systems for boosted user safety.
Popular Folding Mobility Scooters in the UK
There are numerous folding mobility scooters readily available in the UK market. Here are a few of the most popular models:
| Model | Weight Capacity | Optimum Speed | Range on a Full Charge | Weight | Folding Method |
|---|---|---|---|---|---|
| Drive Medical Scout 1 | 25 stone (158 kg) | 4 miles per hour | 12 miles | 46 pounds | Handbook Folding |
| TGA Minimo Plus 4 | 21 stone (133 kg) | 4 miles per hour | 15 miles | 58 pounds | Automatic Folding |
| Kymco K-Lite 4 | 20 stone (127 kg) | 4 mph | 12 miles | 47 lbs | Manual Folding |
| Ultra Lightweight Scooter | 19 stone (121 kg) | 4 miles per hour | 10 miles | 31 lbs | Manual Folding |
| Pride Go-Go Elite Traveller | 21 stone (133 kg) | 4 miles per hour | 13 miles | 46 lbs | Handbook Folding |
Factors to consider When Buying a Folding Mobility Scooter
When purchasing a folding mobility scooter, numerous factors need to be kept in mind to make sure that the model selected fulfills the user's needs.
Aspects to Consider:
- Weight Capacity: It is important to know whether the scooter can support the user's weight comfortably.
- Portability: Consider the weight of the scooter and how quickly it can be folded and stored when not in usage.
- Battery Life: Check the range on a complete charge, as this will figure out how far you can precede requiring recharging.
- Convenience Features: Look for adjustable seats, handlebars, armrests, and other convenience functions to ensure a pleasant ride.
- Warranty and Service: Ensure the scooter includes a warranty and consider the schedule of regional service for repairs and upkeep.
Frequently asked question Section
1. How do folding mobility scooters differ from traditional mobility scooters?
Folding mobility scooters are designed for portability and are usually lightweight and compact, making them easy to transportation. Standard mobility scooters are larger and often planned for more continual outside use.
2. Are folding mobility scooters suitable for outdoor usage?
Yes, while many folding scooters are lightweight and compact, numerous designs are designed for outdoor use and can handle rough surface.
3. Just how much do folding mobility scooters cost?
Prices can vary considerably based on design and features however normally range from ₤ 500 to ₤ 1,500 or more for top quality models.

4. Do I require a special license to operate a mobility scooter?
In the UK, users do not require a driving license to operate mobility scooters, but they need to abide by particular policies concerning their usage on the highway.
5. Can I take my folding mobility scooter on public transport?
Many public transportation choices in the UK license folding scooters, but it's recommended to check specific policies with private transportation business.
Folding mobility scooters provide a practical option for enhancing mobility, independence, and lifestyle for numerous people. With a myriad of alternatives available in the UK market, it is important for potential purchasers to conduct comprehensive research and think about numerous elements to discover the model that best matches their requirements. With the right folding mobility scooter, users can anticipate taking pleasure in increased flexibility and confidence in navigating their world.
In the seeking for a good night’s sleep, the grandness of a prime rest cannot be overdone. Enter the Derila Pillow, an innovative mathematical product studied to ameliorate eternal rest prime and supply engineering science financial backing. This report delves into the decisive features, benefits, and overall rate of the Derila Pillow, as easily as the feedback from consumers WHO bear transformed their kip with this production.
Launching to the Derila Pillow
The Derila Rest is marketed as a exchange premium retention fizz pillow, engineered to proffer optimal plump for and comfortableness. Computer memory effervesce technology, notable for its adaptability and support, forms the nitty-gritty of this pillow. It molds to the user’s neck and manoeuvre contours, maintaining coalition and frankincense aiming to alleviate rough-cut trouble areas associated with miserable dormant carriage. The pillow's contrive promises to suit different quiescence styles, whether unmatchable is a vertebral column sleeper, root sleeper, or stomach railroad tie.
Features of the Derila Pillow
Matchless of the standout features of the Buy Derila Pillow Pillow is its exercise of high-denseness memory foam, which offers ranking console and plunk for o'er conventional pillows. This corporeal not entirely conforms to the user's physical body only as well retains that form end-to-end the night, ensuring stalls endure.
Another noted sport is the pillow's applied science intention. Unlike traditional pillows that throne allow for the cervix unsupported, the Derila Rest includes a contoured design, Derila Pillow review providing ergonomic sustain to take over tense on the neck and shoulders. This buttocks significantly abridge break of day stiffness, which is a rough-cut ailment among those experiencing pitiful quietus.
The Derila Pillow also boasts a temperature reduction feature film. The memory board fizz is engineered to alleviate line circulation, safekeeping the rest cool off end-to-end the night. This facial expression rear end examine especially good for those WHO incline to overheat during sleep.
Benefits of Using Derila Pillow
The primary quill gain of the Derila Rest is its potential to improve sopor prize essentially. By providing right neck alinement and support, it helps users reach a deeper, More reposeful catch some Z's. Many users make reported rock-bottom incidences of wakeful up with cervix pain sensation or headaches, which are oftentimes symptoms of poor Order Derila Pillow pillow financial support.
The pillow's adaptability to dissimilar dormant positions makes it a various pick for households with varied sleeping preferences. This adaptability helps sustain a decline quiescency posture, which is of the essence for total spinal health.
The lasting nature of memory board fizz ensures longevity, qualification it a cost-efficacious solvent to sleep issues ended meter. Additionally, the pillow's hypoallergenic materials have it worthy for individuals with allergies, ensuring a sporting and healthy catch some Z's surroundings.
Consumer Feedback
Client reviews of the Derila Pillow consistently play up the advance in slumber prize and simplification in neck opening and shoulder joint afflict. Many users possess described wakeful up fresh and rejuvenated afterwards switch to the Derila Pillow. The chilling technology has standard electropositive remarks from those World Health Organization feel Nox sweats, citing the pillow's power to persist cool down end-to-end the dark as a pregnant vantage.
However, as with altogether products, in that respect are a few integrated reviews. About users famed a period of time of adaptation when transitioning from a traditional pillow to unrivaled made of memory fizz. Initially, it Crataegus laevigata find firmer than expected, but near users reported acclimating within a few nights.
Terminal Thoughts
In conclusion, the Derila Rest presents itself as a rotatory intersection in the eternal rest accouterment securities industry. It offers a feasible solution for those struggling with sleep-germane discomforts by ensuring right make out and spinal conjunction done its overbold intention and innovative materials.
Patch the initial investiture might appear more than substantial compared to received pillows, the benefits of improved sleep, decreased pain, and the longevity of the cartesian product proffer significant esteem for money. The versatility to reconcile diverse sleeping positions boost broadens its appeal, devising it a praiseworthily selection for anyone looking to ascent their dormant equipment.
The Derila Pillow stands come out of the closet not but for its plan and operate but likewise for its power to importantly enhance sleep quality—an invaluable health gain. Therefore, prospective buyers considering the Derila Rest arse position it as a worthwhile investing towards achieving restful and renewing eternal rest.
As the world becomes increasingly digital, the threats that accompany online activities continue to evolve, with one of the most sinister being phishing. Phishing, a form of cybercrime that involves tricking individuals into divulging sensitive personal information such as passwords, account numbers, and credit card details, has become a prevalent issue in today's interconnected society.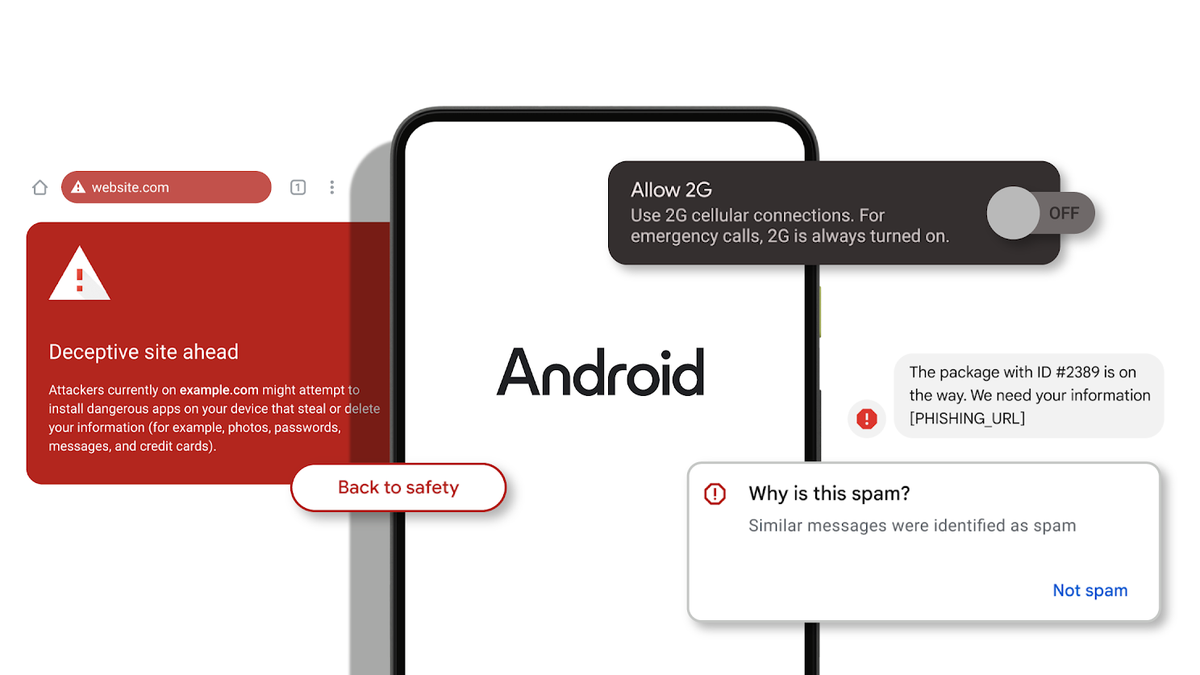 This article explores the alarming rise of online phishing, its various forms, and practical steps individuals and organizations can take to protect themselves from falling victim.
This article explores the alarming rise of online phishing, its various forms, and practical steps individuals and organizations can take to protect themselves from falling victim.
Phishing schemes have been around since the early days of the internet, but their complexity and prevalence have multiplied significantly in recent years. Cybercriminals are continuously finding new strategies to bypass security measures and exploit unsuspecting users. According to a recent report from the Anti-Phishing Working Group, phishing attacks increased by a staggering 220% in 2020, and the numbers have only continued to grow.
One of the primary reasons for the surge in phishing attacks is the increase in online activities spurred by the COVID-19 pandemic. The shift towards remote work and reliance on digital platforms for communication and transactions has created a fertile ground for cybercriminals. Phishing emails have become more sophisticated, often masquerading as legitimate communications from trusted organizations or government entities. For instance, email alerts about COVID-19 vaccinations or economic relief packages have been exploited by scammers to lure victims into revealing their personal information.
Phishing techniques can vary widely, but they commonly fall into three main categories: spear phishing, whaling, and clone phishing. Spear phishing targets specific individuals or organizations, using personal information to make the attack appear more credible. Whaling, on the other hand, focuses on high-profile targets such as executives or board members, often involving more elaborate tactics to gain their trust. Clone phishing occurs when an attacker creates an identical replica of a previously delivered legitimate email, replacing any legitimate links with malicious ones, and then sends it back to the victim.
In addition to email-based attacks, phishing has also expanded to include social media platforms and messaging apps, where users can be lured into clicking links or providing personal information. Scammers are adept at creating fake profiles to gain the trust of potential victims, further complicating the detection of these fraudulent activities. Even text messages, known as SMS phishing or "smishing," have become a popular avenue for attackers to reach victims directly on their mobile devices.
The consequences of falling victim to phishing attacks can be devastating. Many victims find themselves dealing with financial loss, identity theft, and numerous headaches as they work to recover their compromised accounts. In severe cases, organizations can face reputational damage, regulatory penalties, and loss of customer trust, leading to long-term implications for their business.
So, how can individuals and organizations protect themselves from the threat of phishing? Awareness and education are key components in preventing these attacks. Users should be trained to recognize the signs of phishing attempts, such as poor grammar, generic greetings, and GOOGLE DELETE PHISING suspicious links. Additionally, using multifactor authentication (MFA) can add an extra layer of security by requiring further verification beyond just a password.
Regularly updating passwords and using strong, unique combinations for different accounts is crucial. Password managers can help users generate and store complex passwords securely, reducing the likelihood of password reuse across accounts. Furthermore, individuals should remain cautious when clicking on links in emails or messages, especially those from unfamiliar sources. Hovering over links before clicking can reveal their true destination and help users avoid malicious sites.
Organizations should also implement comprehensive cybersecurity policies that include regular phishing simulations to train employees on how to identify and respond to phishing attempts. Strong email filtering systems can help catch phishing emails before they reach employees’ inboxes, further mitigating risk.
Ultimately, the rise in online phishing serves as a reminder of the importance of vigilance in the digital landscape. As technology continues to advance, so too will the tactics used by cybercriminals. By remaining informed, proactive, and cautious, individuals and organizations can better safeguard themselves against this ever-evolving threat. The digital world offers unprecedented opportunities, but it also demands a heightened awareness of security to ensure a safer online experience for everyone.
In an increasingly digital world, where online transactions and communication have become commonplace, the threats of cybercrime continue to evolve. One of the most pervasive and dangerous forms of cybercrime is web phishing. This case study examines the mechanisms, implications, and preventive measures associated with web phishing, using real-world examples to illustrate the impact on individuals and businesses alike.
What is Web Phishing?
Phishing is a fraudulent attempt to obtain sensitive information such as usernames, passwords, credit card details, and other personal information by disguising as a trustworthy entity in electronic communications. The most common delivery method for phishing schemes is email, though it's also prevalent in social media, SMS, and fake websites. Phishing attempts can take many forms, but most lead to the creation of counterfeit websites designed to mimic legitimate sites.
A Case Study: The Google and Facebook Scam
One of the most notorious phishing cases involved a Lithuanian hacker named Evaldas Rimasauskas, who managed to swindle over $100 million from tech giants GOOGLE DELETE PHISING and Facebook. Between 2013 and 2015, he impersonated a Taiwanese manufacturer by creating fake emails and invoices that appeared legitimate. Rimasauskas set up a fake company with a real website and used it to send phishing emails to the finance departments of both companies. The emails included convincing documentation and instructions, which led the executives to facilitate wire transfers to the hacker's account.
This case highlights how sophisticated phishing attacks can bypass traditional security measures and how even the largest corporations are vulnerable to such attacks. Increasingly, attackers are using social engineering tactics to manipulate victims into revealing confidential information or authorizing fraudulent transactions.
The Mechanics of Phishing Attacks
Phishing attacks generally follow a systematic approach:
- Preparation: Attackers research their targets, often using social media platforms to gather information about employees and organizational hierarchies.
The Consequences of Phishing
The consequences of a successful phishing attack can be devastating. For individuals, it can lead to identity theft, financial loss, and long-lasting emotional distress. For organizations, the repercussions are often more severe, including significant financial losses, legal penalties, and reputational damage. According to the FBI's Internet Crime Complaint Center (IC3), victims of phishing schemes reported losses of over $54 million in 2021 alone.
Preventive Measures
- Education and Training: One of the most effective ways to combat phishing is through education. Organizations should regularly train employees to recognize phishing attempts and the common tactics used by cybercriminals. This training should be updated annually or whenever new threats emerge.
Conclusion
Web phishing presents a significant threat to both individuals and organizations worldwide. These scams exploit human vulnerabilities and can lead to devastating financial and reputational damage. As cyber criminals become increasingly sophisticated, it is crucial for individuals and organizations to remain vigilant, educate themselves, and adopt robust security practices. By understanding the mechanics of phishing attacks and implementing preventive measures, we can combat this pervasive issue and safeguard our digital identities.
Phishing is a pervasive and alarming form of cybercrime that targets individuals and organizations through deceptive online tactics. It typically involves fraudulent communications designed to trick recipients into revealing sensitive information, such as passwords, credit card numbers, and personal identification details. With the digital landscape expanding, phishing scams have become increasingly sophisticated, necessitating a comprehensive understanding of their mechanics and the strategies for prevention.
What is Phishing?
Phishing is characterized by attempts to acquire sensitive information by masquerading as a trustworthy entity in electronic communications. This deception can occur through various channels including emails, social media, and text messages, commonly referred to as "smishing" when it occurs via SMS. Phishing campaigns often employ psychological manipulation; attackers create a sense of urgency or curiosity to compel victims into taking hasty actions.
Common Techniques

- Email Phishing: The most prevalent form involves sending fraudulent emails that appear to be from legitimate organizations, such as banks or well-known online services. These messages often contain links to imitation websites that closely mimic the real ones, prompting users to enter their credentials.
The Risks of Phishing
The consequences of falling victim to a phishing attack can be severe, resulting in substantial financial loss and reputational damage. Individuals may lose access to their bank accounts, have their identities stolen, or pay ransoms for hijacked devices. Organizations face risks that can extend beyond financial losses, including data breaches, legal repercussions, GOOGLE DELETE PHISING and the erosion of customer trust.
Additionally, the psychological impact on victims can be profound, leading to feelings of vulnerability and helplessness. In some cases, the repercussions of a phishing attack extend into broader societal implications, creating a growing need for enhanced cybersecurity awareness and practices.
Prevention Strategies
Effective prevention against phishing requires a combination of awareness, technology, and best practices. Here are key strategies:
- Education and Awareness: Organizations should conduct regular training sessions to educate employees about the signs of phishing attempts and safe online practices. Encouraging a culture of vigilance can help mitigate risks.
Conclusion
Phishing is an ongoing threat in our increasingly digitalized world, evolving in complexity and scale. By understanding the tactics employed by cybercriminals and implementing robust preventative strategies, individuals and organizations can significantly reduce their risk of becoming victims. Continual education, vigilance, and proactive measures are key to battling this pervasive cyber threat. As technology continues to advance, a collective effort to raise awareness and enhance cybersecurity practices will paves the way for a safer online environment for everyone.
Pure Earth CBD Ingredients is a reputable global company that specializes in the development and production of premium CBD products. The company boasts an extensive range of products, including CBD oils, tinctures, gummies, capsules, topicals, and edibles, all designed to meet the diverse needs of consumers. In this report, we will shed light on the company's commitment to excellence, its holistic approach to CBD ingredients, and the benefits of its products.
Quality Control and Extraction Methods
One of Pure Earth's key differentiators is its dedication to using only the finest hemp ingredients, sourced from reputable suppliers. The company employs state-of-the-art extraction methods, including CO2, ethanol, and solventless extraction, to ensure the highest quality CBD oil. This meticulous approach ensures that the final products are free from contaminants, heavy metals, and other impurities.
Pure Earth also adheres to the most stringent quality control measures, including rigorous testing for purity, potency, and consistency. Each batch of CBD oil undergoes third-party lab testing to verify the presence of cannabinoids, terpenes, and other beneficial compounds. The company's unwavering commitment to quality is reflected in its unparalleled testing protocol, which goes beyond industry standards.
Holistic Approach to CBD Ingredients
Pure Earth's founder and CEO has a background in pharmacology and pharmacognosy, which has enabled the company to adopt a holistic approach to CBD ingredients. The company recognizes the vast potential of CBD to interact with the human body's endocannabinoid system and promotes a holistic approach to wellness. This involves not only using high-quality CBD but also combining it with other natural ingredients to amplify its effects.
Pure Earth offers a wide range of products infused with various natural ingredients, including terpenes, flavonoids, and essential oils. These synergistic combinations aim to optimize the therapeutic potential of CBD, catering to diverse preferences and needs. For example, the company's Pain Relief Formula combines CBD with essential oils of wintergreen, peppermint, and eucalyptus to create a potent analgesic product.
Benefits of Pure Earth CBD Products
Pure Earth CBD products have gained widespread recognition for their premium quality, efficacy, and commitment to customer satisfaction. The company's dedication to research and development ensures that its products undergo continuous improvement, aligning with the ever-evolving CBD landscape.
Some notable benefits of Pure Earth CBD products include:
Fast and Effective Relief: Pure Earth's CBD products offer rapid relief from pain, Pure Earth CBD Ingredients anxiety, and inflammation, making them an attractive option for individuals seeking quick and effective solutions.
Non-Psychoactive and Safe: As a hemp-derived CBD company, Pure Earth ensures that all its products are non-intoxicating, non-addictive, and safe for consumption by individuals of all ages.
* Sustainable and Eco-Friendly: Pure Earth prides itself on using eco-friendly packaging and sourcing materials from suppliers committed to sustainable practices.
Conclusion
In conclusion, Pure Earth CBD Ingredients stands out as a pioneering company in the CBD industry, driven by a commitment to excellence and a holistic approach to wellness. By prioritizing quality, innovation, and customer satisfaction, the company has established itself as a trusted brand in the global market. Whether you're a seasoned CBD user or a newcomer to the world of cannabinoids, Pure Earth offers a diverse range of premium products to cater to your unique needs and preferences.
In the digital age, where information and communication flow seamlessly across platforms, cybersecurity has become a paramount concern for individuals and organizations alike. Among the myriad of threats that plague the internet, phishing stands out as one of the most nefarious tactics employed by cybercriminals. One particularly alarming trend that has emerged in recent times is the phenomenon of Google Online Challenge phishing, a sophisticated strategy that targets users by masquerading as legitimate competitions or opportunities associated with Google. Understanding how this type of phishing works and recognizing its dangers is essential for safeguarding personal and professional digital spaces.
Phishing, by definition, is a malicious attempt to obtain sensitive information from individuals by disguising as a trustworthy entity. The Google Online Challenge phishing scheme capitalizes on the legitimacy and popularity of Google's branding. Cybercriminals create fake competitions or challenges, often featuring attractive prizes such as cash rewards, gadgets, or exclusive access to events. These schemes typically entice participants with promises of high rewards for minimal effort, which effectively lures users into participating without fully vetting the authenticity of the opportunity.
One of the key mechanisms these phishing attempts employ is social engineering. By exploiting psychological triggers like curiosity, greed, and the fear of missing out (FOMO), scammers can manipulate victims into providing their personal information, such as passwords, credit card numbers, or social security numbers. Often, these phishing emails or messages will contain links that direct victims to counterfeit web pages designed to look almost identical to legitimate Google sites. This attention to detail serves to instill trust and encourages victims to enter sensitive information, believing they are participating in a genuine challenge.
To illustrate how insidious this phishing tactic can be, consider a typical scenario: an unsuspecting user receives an email claiming they have been selected as a finalist in a prestigious Google Online Challenge. The email features Google’s logo, official language, and a sense of urgency, urging them to click a link and confirm their identity to claim their prize. Upon clicking the link, they are directed to a near-perfect replica of a Google login page. Here, the user is prompted to enter their credentials, unknowingly handing over access to their Google account to the scammers.
This not only puts the individual’s personal information at risk but can also have broader implications for organizations. If an employee falls victim to such a scheme, it could compromise sensitive company data, client information, and proprietary business strategies, leading to significant financial and reputational damage.
Preventing the spread of Google Online Challenge phishing requires both technical and behavioral measures. First and foremost, education and awareness are crucial. Users should be educated about the signs of phishing attempts, such as misspellings, unusual sender addresses, and suspicious links. Organizations should implement regular training sessions to keep employees informed of the latest phishing tactics and encourage vigilance when navigating online communications.
Moreover, employing technical security measures can bolster defenses against phishing. Multi-factor authentication (MFA) adds an additional layer of security, making it more difficult for hackers to gain unauthorized access even if they have obtained login credentials. Email filters and anti-phishing software can help detect and block phishing attempts before they reach users' inboxes.
In addition, users should take advantage of Google’s security features, like the built-in phishing protection tools in Gmail, which scan messages for potentially harmful links and warn users of suspicious activity. Regularly updating passwords and using unique passwords for different platforms can also minimize the risks associated with account compromises.
Furthermore, it is vital for tech giants like GOOGLE DELETE PHISING to continually enhance their cybersecurity measures and collaborate with law enforcement to identify and apprehend cybercriminals behind these phishing schemes. Prompt reporting of phishing attempts can help in curtailing their proliferation.
In conclusion, the emergence of Google Online Challenge phishing underscores the ever-evolving nature of cyber threats. As digital interactions grow in complexity and frequency, so too does the ingenuity of cybercriminals attempting to exploit them. Vigilance, education, and robust security measures are paramount in navigating this perilous landscape. By remaining aware of the tactics employed by scammers and taking proactive steps to protect personal and organizational information, individuals can contribute to a safer online environment. The battle against phishing may be ongoing, but with collective effort and awareness, we can mitigate the damage inflicted by these malicious schemes.
The battle against phishing may be ongoing, but with collective effort and awareness, we can mitigate the damage inflicted by these malicious schemes.
In today's digital age, phishing scams have morphed into one of the most pervasive threats to online safety, particularly for young internet users. To combat this escalating issue, the Federal Trade Commission (FTC) has introduced an innovative educational game called "On Guard Online," which is specifically designed to teach children and adolescents how to recognize and avoid phishing scams. This game stands out as a noteworthy advancement in the realm of digital education, harnessing interactive learning to foster real-world skills in internet safety.
Phishing, the malicious practice of tricking individuals into revealing sensitive information such as usernames, passwords, and credit card numbers, has evolved in complexity and sophistication. Scammers employ a variety of tactics, from seemingly harmless emails to fake websites that closely mimic legitimate services. The FTC’s On Guard Online game takes a proactive approach to equip young users with the knowledge and skills they need to identify and respond to such threats.
The foundational premise of the game is built on engaging young users through an interactive online platform. Players navigate scenarios that replicate real-life phishing attempts, including emails that tempt users with fraudulent offers and social engineering tactics in online interactions. The immersive experience of the game allows players to recognize red flags associated with phishing schemes, such as poor grammar, unusual sender addresses, or urgent calls to action. By engaging with these scenarios, players learn to apply critical thinking and analytical skills to evaluate the legitimacy of online communications.
One significant advance in On Guard Online is its integration of gamification elements that enhance user engagement while promoting retention of information. The game's design includes various levels and challenges, rewarding players for successfully identifying and reporting phishing attempts. These gamified elements not only make learning enjoyable but also reinforce essential concepts of cybersecurity in a manner that resonates with the gaming preferences of younger audiences. As players progress through higher levels, they encounter increasingly complex phishing scenarios that push them to hone their skills further—ultimately preparing them to navigate the web safely.
Additionally, On Guard Online provides educational resources that go beyond the confines of the game itself. It encourages open discussions about phishing scams among players, their peers, and family members. This aspect of the game fosters a community of learners where players can share experiences and knowledge, empowering them to spread awareness within their social circles. By facilitating conversations about online safety, the game serves as a bridge between formal education and everyday internet practices, thus reinforcing the importance of cybersecurity in daily life.
The game is also a tool for educators and parents, providing them with a framework to teach children about online risks. Schools can integrate On Guard Online into their curricula, offering dedicated sessions on internet safety that are both informative and GOOGLE DELETE PHISING interactive. Furthermore, the FTC provides educators with guides and discussion prompts that can help facilitate classroom conversations about phishing scams. This collaborative approach ensures that the lessons learned through the game have a wider impact, extending beyond individual experiences to shape collective understanding of digital safety.
Importantly, On Guard Online reflects a growing recognition of the need for proactive strategies in internet safety education. As phishing scams continue to evolve, so too must the tools available for countering them. By adopting a forward-thinking approach, the FTC has addressed a critical gap in current online safety measures. While traditional educational programs often focus on passive learning methods, the interactive gameplay of On Guard Online empowers young users to actively engage with the material, enhancing their ability to retain and apply what they learn.
In conclusion, the FTC’s On Guard Online game represents a significant advancement in the fight against phishing scams targeting young internet users. By utilizing gamification and interactive learning, the FTC not only educates players about the nuances of recognizing phishing attempts but also encourages critical thinking and community engagement around the topic. As young individuals increasingly navigate a complex digital landscape, the skills honed through playing On Guard Online are essential for fostering resilient and informed internet users. This innovative approach marks a promising step forward in enhancing digital literacy and safety, ultimately contributing to a more secure online environment for all. As technology continues to evolve, so too must our educational initiatives to ensure that the next generation is equipped to face the challenges of the digital world.
