Strona blogu
In today's digital age, phishing scams have morphed into one of the most pervasive threats to online safety, particularly for young internet users. To combat this escalating issue, the Federal Trade Commission (FTC) has introduced an innovative educational game called "On Guard Online," which is specifically designed to teach children and adolescents how to recognize and avoid phishing scams. This game stands out as a noteworthy advancement in the realm of digital education, harnessing interactive learning to foster real-world skills in internet safety.
Phishing, the malicious practice of tricking individuals into revealing sensitive information such as usernames, passwords, and credit card numbers, has evolved in complexity and sophistication. Scammers employ a variety of tactics, from seemingly harmless emails to fake websites that closely mimic legitimate services. The FTC’s On Guard Online game takes a proactive approach to equip young users with the knowledge and skills they need to identify and respond to such threats.
The foundational premise of the game is built on engaging young users through an interactive online platform. Players navigate scenarios that replicate real-life phishing attempts, including emails that tempt users with fraudulent offers and social engineering tactics in online interactions. The immersive experience of the game allows players to recognize red flags associated with phishing schemes, such as poor grammar, unusual sender addresses, or urgent calls to action. By engaging with these scenarios, players learn to apply critical thinking and analytical skills to evaluate the legitimacy of online communications.
One significant advance in On Guard Online is its integration of gamification elements that enhance user engagement while promoting retention of information. The game's design includes various levels and challenges, rewarding players for successfully identifying and reporting phishing attempts. These gamified elements not only make learning enjoyable but also reinforce essential concepts of cybersecurity in a manner that resonates with the gaming preferences of younger audiences. As players progress through higher levels, they encounter increasingly complex phishing scenarios that push them to hone their skills further—ultimately preparing them to navigate the web safely.
Additionally, On Guard Online provides educational resources that go beyond the confines of the game itself. It encourages open discussions about phishing scams among players, their peers, and family members. This aspect of the game fosters a community of learners where players can share experiences and knowledge, empowering them to spread awareness within their social circles. By facilitating conversations about online safety, the game serves as a bridge between formal education and everyday internet practices, thus reinforcing the importance of cybersecurity in daily life.
The game is also a tool for GOOGLE DELETE PHISING educators and parents, providing them with a framework to teach children about online risks. Schools can integrate On Guard Online into their curricula, offering dedicated sessions on internet safety that are both informative and interactive. Furthermore, the FTC provides educators with guides and discussion prompts that can help facilitate classroom conversations about phishing scams. This collaborative approach ensures that the lessons learned through the game have a wider impact, extending beyond individual experiences to shape collective understanding of digital safety.
Importantly, On Guard Online reflects a growing recognition of the need for proactive strategies in internet safety education. As phishing scams continue to evolve, so too must the tools available for countering them. By adopting a forward-thinking approach, the FTC has addressed a critical gap in current online safety measures. While traditional educational programs often focus on passive learning methods, the interactive gameplay of On Guard Online empowers young users to actively engage with the material, enhancing their ability to retain and apply what they learn.
In conclusion, the FTC’s On Guard Online game represents a significant advancement in the fight against phishing scams targeting young internet users. By utilizing gamification and interactive learning, the FTC not only educates players about the nuances of recognizing phishing attempts but also encourages critical thinking and community engagement around the topic. As young individuals increasingly navigate a complex digital landscape, the skills honed through playing On Guard Online are essential for fostering resilient and informed internet users. This innovative approach marks a promising step forward in enhancing digital literacy and safety, ultimately contributing to a more secure online environment for all. As technology continues to evolve, so too must our educational initiatives to ensure that the next generation is equipped to face the challenges of the digital world.
Phishing is a form of cybercrime that involves deceiving individuals into providing sensitive information such as usernames, passwords, credit card details, and other personal data. This malicious tactic has evolved over the years into a sophisticated method of attack that leverages social engineering and technological advancements to exploit human emotions like fear, curiosity, and trust. As the internet continues to grow, so does the prevalence of phishing attacks, making it imperative for users to understand the nature of this threat, the techniques employed by attackers, and the methods for protection.
The term "phishing" is derived from the word "fishing," implying that cybercriminals are casting a net to catch unsuspecting victims. Typically, phishing involves the use of fraudulent emails or websites designed to appear legitimate, often mimicking well-known organizations such as banks, online services, or social media platforms. These communications usually contain urgent messages that prompt users to click on malicious links, which lead to sites that resemble authentic web pages.
One common type of phishing attack is spear phishing, where attackers target specific individuals or organizations with personalized messages. This approach increases the likelihood of success because the attackers gather information about their victims beforehand, making the content more convincing. For instance, they may reference current projects, mutual acquaintances, or legitimate business accounts, creating a false sense of security.
Another variant is whaling, which specifically targets high-profile individuals within organizations, such as executives or senior management. By using highly tailored messages, whaling attacks aim to extract sensitive corporate information or initiate fraudulent wire transfers. Given the potential financial repercussions and reputational damage, whaling poses a significant risk to companies and their stakeholders.
Phishing has also expanded beyond email, with the emergence of SMS phishing (smishing) and voice phishing (vishing). Smishing involves sending fraudulent text messages that prompt users to provide personal information or click on malicious links. Vishing, on the other hand, is executed through phone calls that impersonate legitimate entities, such as banks or government agencies. These methods leverage technology to reach individuals directly, increasing the persuasion factor in the communication.
The impact of phishing attacks can be severe. Victims may suffer financial losses, identity theft, and unauthorized transactions, while companies can face legal repercussions, loss of customer trust, and data breaches that compromise sensitive corporate information. According to the Anti-Phishing Working Group (APWG), phishing attacks have increased dramatically, with millions of phishing websites reported each year. This growth indicates a pressing need for effective countermeasures.
To combat phishing, GOOGLE DELETE PHISING it is essential for individuals and organizations to implement robust security practices. One of the first steps is to educate users about the risks associated with phishing and how to recognize potential threats. This education includes training programs that cover the common signs of phishing attempts, such as misspelled URLs, generic greetings, and suspicious attachments.
Another critical measure is the adoption of multi-factor authentication (MFA). MFA provides an additional layer of security by requiring users to confirm their identity through multiple means—such as a password followed by a unique code sent to their mobile device—making it more challenging for cybercriminals to gain unauthorized access.
Regularly updating software and security systems is also crucial. Organizations should ensure that all applications, operating systems, and anti-virus software are kept up to date to protect against known vulnerabilities exploited by attackers. Moreover, utilizing advanced email filtering solutions can help detect and block phishing attempts before they reach the user's inbox.
For individuals, verifying the authenticity of communications is vital. Users should take the time to hover over links to inspect their URLs before clicking, avoid providing personal information in response to unsolicited requests, and be vigilant about any correspondence that evokes a sense of urgency or fear. When in doubt, contacting the organization directly using official contact methods can help confirm the legitimacy of the communication.
In conclusion, phishing is a pervasive cyber threat that can lead to significant financial and personal losses if left unchecked. As technology continues to evolve, so do the tactics employed by cybercriminals. Therefore, understanding the nature of phishing, recognizing its various forms, and implementing effective security measures are essential in protecting oneself and one’s organization from this growing threat.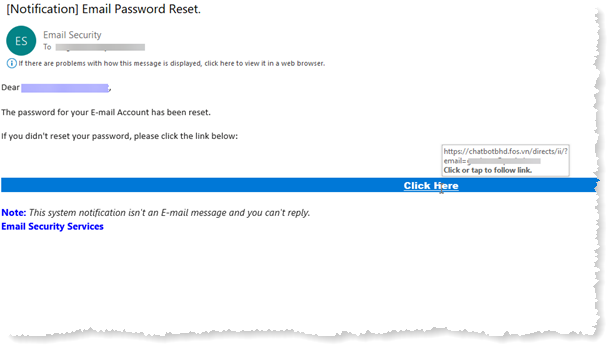 Through education and vigilance, individuals and companies can significantly mitigate the risks associated with phishing and maintain a secure online environment.
Through education and vigilance, individuals and companies can significantly mitigate the risks associated with phishing and maintain a secure online environment.
Nuestra misión
En JustCBD, nuestra misión es ayudar a las personas a vivir sus mejores vidas proporcionándoles productos de CBD de alta calidad que promueven la relajación, alivian el estrés y mejoran el bienestar general. Nos comprometemos a utilizar únicamente los mejores ingredientes y los procesos de extracción y fabricación más avanzados para elaborar productos seguros, eficaces y cómodos de usar. Nuestro objetivo es poner al alcance de todos los beneficios del what do cbd edibles do.
¿Quiénes somos?
JustCBD ofrece una diversa gama de productos de cáñamo de calidad probada y cultivados de forma natural, desde gominolas hasta aceite de CBD de espectro completo que ayuda a mantener el bienestar diario de la mente y el cuerpo. Con la innovación y la pasión en nuestro objetivo, JustCBD sigue desarrollando productos derivados del CBD líderes en el sector en los que confían miles de nuestros clientes de todo el mundo.
Por qué elegir JustCBD
Proporcionamos una verificación independiente de las Buenas Prácticas de Fabricación, por lo que nuestros clientes pueden estar seguros de que cada uno de nuestros procedimientos de producción cumple los criterios necesarios para llevar a cabo un programa de seguridad APPCC (Análisis de Peligros y Puntos Críticos de Control) adecuado.
En todos los pedidos al detal de más de €20 en España
Nos ganamos la tranquilidad de cada comprador con total transparencia, ya que los resultados de laboratorio de todos los artículos que vendemos se pueden localizar fácilmente en nuestra página web. Gracias a nuestros elevados estándares y rigurosos métodos de prueba, puede estar seguro de que está adquiriendo productos de CBD consistentes y fiables.
Todos los artículos de JustCBD son 100% naturales y hechos en los EE.UU.. Solo utilizamos CBD derivado del cáñamo de la mejor calidad con cero productos químicos, como fertilizantes, herbicidas y pesticidas.
Tanto los profesionales como los consumidores en general coinciden en que no hay nada mejor que la potencia, el sabor y la eficacia de los productos JustCBD. Como líderes del competitivo sector del CBD online, siempre vamos un paso por delante de cualquier otra tienda de CBD.
Garantía de satisfacción de 30 días
Cada uno de nuestros potentes productos de CBD a la venta incluye una garantía de satisfacción del 100%. Confiamos tanto en nuestros satisfactorios productos de CBD que si no quedas satisfecho en los 30 días posteriores a tu compra, te devolveremos el dinero encantados. Sólo tiene que devolver el producto con su número de pedido.
Lo más vendido
Gominolas de CBD para dormir
Aceite de CBD de espectro completo
Bomba de baño de CBD
Aceite de Coco con CBD
3406 SW 26th Terrace C1
Fort Lauderdale, FL 33312
Este producto no debe ser utilizado ni vendido a personas menores de 18 años. Este producto sólo debe utilizarse según las indicaciones de la etiqueta. No debe utilizarse en caso de embarazo o lactancia. Consulte con un médico antes de usarlo si tiene una condición médica grave o usa medicamentos recetados. Se debe buscar el consejo de un médico antes de usar este y cualquier otro suplemento. Todas las marcas comerciales y derechos de autor son propiedad de sus respectivos dueños y no están afiliados ni respaldan este producto. Estas declaraciones no han sido evaluadas por la FDA. Este producto no está destinado a diagnosticar, tratar, curar o prevenir ninguna enfermedad. Al utilizar este sitio, usted está de acuerdo en seguir la Política de Privacidad y todos los Términos y Condiciones impress en este sitio. Nulo donde esté prohibido por la ley. Nuestros productos contienen menos d 0,3% de THC.
Phishing is a form of cybercrime that involves tricking individuals into revealing sensitive information, such as usernames, passwords, credit card details, or other personal data. This is generally done through deceptive emails, fake websites, or instant messages. As the internet continues to evolve and become a crucial aspect of daily life, online phishing schemes are becoming increasingly sophisticated, posing significant risks to individuals and organizations alike. Understanding the mechanisms behind these threats is essential for enhancing online security and preventing fraud.
The Mechanics of Phishing
Phishing attacks typically employ social engineering techniques to manipulate users into giving up their information. Attackers often impersonate legitimate entities, such as banks, e-commerce sites, or even colleagues within a workplace. The initial contact usually comes in the form of an email, but phishing can also occur via text messages (known as smishing), phone calls (vishing), or social media platforms.
Upon encountering a phishing attempt, users may receive an email that appears authentic but contains a sense of urgency or threat. For example, the email may claim that there is an issue with their account or that immediate action is required to resolve a security concern. This urgency can pressure users into clicking links that lead to counterfeit websites designed to look identical to the legitimate sites.
Types of Phishing Attacks
- Email Phishing: The most recognized form, where attackers send fraudulent emails mimicking trusted entities. The emails often contain harmful links or attachments that can compromise security.
Risks Associated with Phishing
The ramifications of falling for a phishing scam can be severe. Individuals may experience identity theft, financial loss, and emotional distress. For organizations, phishing can lead to data breaches, loss of sensitive information, financial losses, and damage to reputation. Additionally, the fallout can extend to customers, clients, and other stakeholders who trust the organization that has been compromised.
Furthermore, phishing can lead to ransomware attacks, where hackers lock access to systems and demand ransom for GOOGLE DELETE PHISING the decryption key. Such attacks can immobilize businesses and lead to lengthy recovery times, costing not just money but creating long-lasting reputational damage.
Signs of Phishing Attempts
Identifying phishing attempts is crucial to preventing them. Common signs include:
- Misspellings or grammatical errors in the email content.
Preventive Measures
Preventing phishing attacks involves a combination of technology, awareness, and best practices. Here are some effective strategies:
- Education and Training: Regularly educating employees and individuals about phishing tactics can improve awareness and response to suspicious emails or messages.
Conclusion
Phishing remains a pervasive threat in the digital age, exploiting human vulnerabilities and advancing technologies. As attackers devise new strategies, it is vital for individuals and organizations to stay informed about the latest phishing tactics and implement robust preventative measures to safeguard sensitive information. Awareness and education play critical roles in combating phishing and ensuring a more secure online environment for everyone. Only through proactive engagement can we hope to minimize the risks posed by these malicious attacks and protect our digital identities.
The Modern Walker: Revolutionizing Mobility for All
In the pursuit of flexibility and ease, the modern walker has progressed from a basic mobility aid into a sophisticated gadget designed to improve the lifestyle for people with restricted mobility. Whether due to age, injury, or special needs, the requirement for effective mobility services is universal. This short article will explore the characteristics, benefits, improvements, and factors to consider surrounding modern walkers, in addition to an often asked questions (FAQ) section to address common questions.
Evolution of Walkers
Conventional Walkers
Conventional walkers, frequently built from aluminum or steel, typically include a rectangular frame with four legs and no wheels. These fundamental models provide stability however can be troublesome, needing users to lift the gadget rather than press it. As an outcome, their use typically places undue stress on the upper body and lowers mobility effectiveness.
The Transition to Modern Walkers
In the previous couple of years, the style and performance of walkers have actually changed significantly. Modern walkers often consist of features such as:
- Wheels: Many new designs now include wheels on the front legs, allowing users to push instead of raise the gadget.
- Seats: Some walkers come equipped with a seated area, offering users with a place to rest when needed.
- Adjustable Heights: Height-adjustable choices allow customized fit, accommodating private user requirements.
- Ergonomic Grips: Improved grip designs enhance convenience and assistance, lessening strain on hands and wrists.
This evolutionary shift not only supports much better mobility however also increases self-confidence, independence, and safety for users.
Benefits of Modern Walkers
Modern walkers include a variety of benefits for people seeking assistance in mobility. These benefits transcend simple physical assistance, contributing positively to psychological and emotional health too.
Increased Mobility and Independence
Modern walkers empower users to navigate their environment more easily. Functions such as wheels and lightweight designs assist in ease of motion, allowing users to preserve autonomy in everyday activities.
Enhanced Safety
The incorporation of safety functions in modern walkers plays a crucial role in avoiding falls and injuries. Anti-slip grips and larger bases of support contribute to stability, thus reassuring users about their safety while walking.
Multi-functionality
Numerous modern walkers use multifunctional designs, acting as both a mobility aid and a storage solution. With features like integrated bags and trays, users can bring fundamentals and individual items, making outings Uplivin Trive Rollator with Seat - Easy Mobility these walkers easier.
Psychological and Emotional Well-being
Improved mobility can greatly affect an individual's mental health. Less dependence on caretakers and the ability to take part in social interactions can cultivate a sense of belonging and improved morale.
Features to Consider When Choosing a Modern Walker
When picking a modern walker, various features ought to be taken into consideration to guarantee it meets the user's requirements optimally. Here, we offer a list of crucial factors to consider:
- Weight and Material: Opt for lightweight materials that still provide durability and stability.
- Wheels: Decide in between walkers with front wheels or stationary legs based on the user's level of mobility.
- Seat Availability: For those who need rest breaks, pick a walker 6-Wheel Sit & Go Shopping Trolley with Seat a built-in seat.
- Storage Options: Look for designs that consist of storage bags or trays for bring daily essentials.
- Height Adjustability: Ensure the walker is height-adjustable to promote proper posture and convenience.
- Foldability: A foldable walker can supply ease in transport and storage.
Common Types of Modern Walkers
The marketplace today offers a variety of walker types tailored to different needs. Below are some common choices:
- Standard Walkers: Basic designs without wheels, appropriate for users who require considerable stability.
- Rolling Walkers (Rollators): Feature wheels on all 4 legs and often consist of seats, catering to those looking for mobility and resting chances.
- Upright Walkers: Designed for users intending to keep better posture while walking. These gadgets motivate an upright position, relieving pressure on the back.
- Transportation Walkers: Lightweight and compact; generally created for short distances and quicker mobility for caretakers.
| Walker Type | Key Features | Best For |
|---|---|---|
| Standard Walker | Lightweight, no wheels | Optimum stability |
| Rolling Walker | Four wheels, often a seat | Increased mobility |
| Upright HEAO Foldable 3-Wheel Walker - Easy Mobility & Storage | Promotes upright posture | Pain in the back alleviation |
| Transportation Walker | Compact and lightweight | Caregivers and brief ranges |
Frequently Asked Questions About Modern Walkers
What is the very best type of walker for seniors?
The very best walker for seniors largely depends on their physical condition and mobility levels. Numerous prefer rolling walkers due to their ease of use, while those with greater stability requirements may take advantage of standard walkers.
How do I guarantee an appropriate suitable for my walker?
To ensure a proper fit, stand inside the walker with your arms hanging conveniently at your sides. Your elbows need to be a little bent when holding the walker deals with. Adjust the height till it lines up perfectly.
Can walkers easily be transported?
Yes, numerous modern walkers are created to fold for easy transport. Models such as transport walkers are particularly lightweight and compact, making them appropriate for travel.
Are walkers covered by insurance?
Many insurance plans, consisting of Medicare and Medicaid, might cover the expense of walkers when recommended by a doctor. It is recommended to confirm protection information with your insurance coverage company.
How can I preserve my modern walker?
Regular checks need to be carried out for any loose screws, frame integrity, and wheel performance. Tidy the walker periodically to maintain hygiene and curb wear.
The modern walker represents a significant improvement in mobility aids, boosting the independence and self-confidence of users. With various types, functions, and factors to consider available, choosing the right walker can significantly enhance mobility and total lifestyle. Understanding these tools empowers users, caretakers, and health care professionals alike to foster an encouraging, My Mobility Scooters active community for those needing Drive Devilbiss Tri-Walker: Comfort & Support on the Go in mobility. The modern walker is not simply a gadget; it is a bridge to liberty and independence.

In the world of innovative bed clothing solutions, the Derila Rest has made a solid impact, draft tending with its forebode of enhancing slumber caliber done engineering science project and advance computer memory froth engineering science. Numerous customers experience divided their experiences and impressions with the Derila Rest. This describe endeavors to collate these reviews, providing a comprehensive examination agreement of its effectiveness, features, and areas for improvement, based on client feedback.
Ware Overview
The Derila Pillow is marketed as a Superior cervix bear out pillow, configured to conciliate a roam of slumber positions. The pillow boasts a unique contouring figure mated with remembering sparkle that claims to conform to a sleeper’s unparalleled shape, providing suited reenforcement to the make out and backbone. This is intended to palliate press points, Derila Pillow Review slim down discomfort, and push relaxing log Z's. The ship's company highlights its rest as good for reducing irritation in vulgar baffling areas so much as the endorse and shoulders, thusly catering to those woe from afflict connected with poor people quiescency postures.
Confirming Reviews and Benefits Noted
Upon analyzing client reviews, it becomes evident that many users apprize the project and comfortableness plane provided by the Derila Pillow reviews Rest. A pregnant count of reviews congratulations the pillow's power to preserve its condition later on extended use, signifying the strength of its retentivity fizz engineering science. Users oft honorable mention an straightaway sense of comfort and documentation. Many customers WHO previously suffered from make out and berm hurting reported pregnant respite afterwards a few weeks of exploitation the Derila Rest.
Interestingly, a recurring radical in plus reviews is the adaptability of the rest to diverse slumber positions. Many side-sleepers extract atonement with how wellspring the pillow aligns the cervix and spine, which is oft a critical appraisal occupy for individuals with exceptional log Z's preferences.
Another maneuver positively highlighted by users is the pillow’s nonsuch rest of firmness and softness—a calibre that appears to fulfil a spacious rate of personal ease preferences. The pillow's hypoallergenic properties make as well been commended by users medium to allergens, scoring it as a preferred selection for allergy-sufferers.
Decisive Reviews and Areas for Improvement
Despite its many advantages, the Derila Rest is not without its criticisms. Some users ingest plant the rest to be likewise firm, especially those wonted to softer, more traditional pillows. Initial soreness is on occasion noted, with a nonage of reviewers experiencing a fugacious historical period of registration.
Feedback on the pillow size appears assorted. While close to users apprise the pillow's contract size, determination it philosophical doctrine for travel, Order Derila Pillow others press out disappointment, suggesting it is short for those who prefer larger pillows or World Health Organization locomote close to to a fault during the Nox. This sizing disagreement mightiness need circumstance by the producer for futurity cartesian product iterations.
A few reviews as well citation a especial scent upon unboxing, a typical trait connected with storage froth products known as off-gassing. Though this nose more often than not dissipates later a short circuit period, it commode be a hindrance for more or less consumers.
Boilersuit Expiation and Recommendations
The world-wide thought towards the Derila Rest leans positive, with the ware systematically higher-ranking intimately for comfort, support, and its expected to meliorate kip lineament. Its innovational approaching to biotechnology appears to be well-accepted by a big section of its user cornerstone. The combination of modern-day materials and serious-minded plan significantly contributes to its reputation.
Nonetheless, the reviews point on that point cadaver way for improvement. Addressing the size concerns by offer variations could broaden its invoke. Furthermore, steps to mitigate the initial effervesce odor mightiness enhance starting time impressions and client gratification.
Concluding Thoughts
The Derila Pillow stands as a coeval resolution for individuals seeking applied science quiescence essentials. Its equipoise of support, comfort, and adaptability aligns substantially with the needs of many users, in particular those looking at to alleviate neck and articulatio humeri bother. As with whatever product, however, grammatical category preferences and experiences leave variegate.
In conclusion, for possible buyers considering the Derila Pillow, it is paramount to shine on personal quiescence habits and Derila Pillow Reviews preferences. For those in look for of a versatile pillow intentional to bread and butter best pricker alignment, the Derila Pillow is surely Worth considering—an investiture pegged on achieving enhanced remainder and greening. For consumers who are sore to resoluteness or size variations, exploring other options or awaiting ulterior framework updates mightiness be advisable. Ultimately, exploiter expiation bequeath hinge on someone of necessity aligned with this groundbreaking contrive.
Rollator Walker Safety: A Comprehensive Guide
As individuals age or face mobility difficulties due to health problem or injury, preserving independence typically ends up being a concern. Rollator walkers, providing both support and mobility, have actually ended up being invaluable tools for lots of. Nevertheless, while they offer many benefits, ensuring safety while using a rollator Byacre Carbon Ultralight Walker with Seat - Ultra Lightweight Mobility is vital. This article supplies extensive insights into rollator walker safety, consisting of best practices, typical dangers, and important suggestions for users and caretakers.

Comprehending Rollators
A KMINA 2-in-1 Rollator Wheelchair Hybrid - Blue walker is a mobility gadget with wheels that allows individuals to stroll with the support of a frame. Unlike basic walkers, rollators typically feature:
- Three or 4 wheels for much easier maneuverability
- Hand brakes for stopping and managing speed
- A seat for resting when needed
- Storage compartments for bring individual products
These functions make rollators suitable for both indoor and outdoor use, boosting the quality of life for users by supplying a sense of self-reliance.
Benefits of Using Rollator Walkers
- Increased Mobility: Rollators can assist users in moving around safely and conveniently.
- Support and Stability: With a sturdy frame and brakes, they provide essential assistance when standing or walking.
- Convenience: Many rollators featured padded seats, allowing users to rest as required.
- Convenience: Integrated storage options can bring essential products, releasing hands for much better balance.
Typical Hazards Associated with Rollator Walkers
While rollators can enhance mobility and safety, they can also position dangers. Users need to be mindful of potential risks to reduce mishaps:
- Uneven Surfaces: Rollators may topple if utilized on irregular or sloped surface.
- Braking Issues: Failing to engage the brakes sufficiently can cause falls.
- Excess Weight: Overloading the storage compartments can affect stability.
- Inappropriate Use: Not using the rollator as meant can result in mishaps.
- Poor Maintenance: Neglecting routine examine wheels and brakes could cause failure throughout use.
Rollator Walker Safety Tips
To boost safety while utilizing rollator walkers, consider the following suggestions:
1. Appropriate Fit and Adjustment
- Height Adjustment: Ensure that the manage height is set to the user's wrist level when standing upright. An appropriate fit motivates better posture and control.
- Seat Height: If the rollator has a seat, guarantee it's comfy and available for resting.
2. Routine Maintenance
- Check Brakes: Make sure hand brakes are working correctly. Change or change them if needed.
- Check Wheels: Regularly examine wheels for wear and tear, and guarantee they spin easily.
- Examine Frame: Check for loose screws or cracks in the frame to guarantee it remains Sturdy Rollator.
| Upkeep Task | Frequency |
|---|---|
| Brake check | Weekly |
| Wheel evaluation | Monthly |
| Frame examination | Regular monthly |
3. Environment Awareness
- Clear Pathways: Keep living spaces devoid of clutter and barriers that might position a tripping danger.
- Lighting: Ensure that areas are well-lit to avoid bad moves, particularly throughout night hours.
- Prevent Slippery Floors: Be cautious on damp or waxed floorings, as they can lead to falls.
4. Safe Walking Techniques
- Engage Brakes When Stopping: Always engage brakes before sitting or while resting.
- Use Proper Walking Technique: Move gradually and preserve a stable speed, taking steps that match the rollator's width.
- Balance While Turning: Turn thoroughly, using the rollator for assistance as required.
5. Seek Assistance
- Involve Caregivers: Encourage member of the family or caregivers to help in browsing difficult surfaces or situations.
- Take Advantage of Community Resources: Many neighborhoods use mobility training for those utilizing walk-assisting gadgets.
Frequently Asked Questions about Rollator Walker Safety
Q1: How do I choose the best rollator walker?
When selecting a rollator, think about the user's weight, height, and intended use. It's likewise necessary to look for functions such as hand brake efficiency and wheel size, which can affect maneuverability.
Q2: Can I use a rollator walker on irregular surface areas?
While rollators can deal with a variety of terrains, it is best to avoid steep inclines, gravel, or cobblestones, as these can be dangerous. Adhere to flat, smooth surfaces whenever possible.
Q3: How can I avoid falls while utilizing a rollator?
Engaging the brakes when sitting, keeping pathways clear, changing your rollator for the correct height, and being conscious of your surroundings can significantly reduce the risk of falls.
Q4: Are all rollator walkers the exact same?
No, rollators are available in different types and sizes, developed for numerous requirements. Some may have additional devices like baskets, while others are lightweight or function a higher weight capability.
Q5: Is it safe to bring bags on a rollator?
Always bear in mind the weight limit and distribution of the load. Use the rollator's designated storage services and prevent straining it.
Rollator walkers are indispensable devices that improve mobility and promote independence for users dealing with mobility difficulties. However, ensuring safety while using these devices is vital. By understanding possible threats, sticking to safe practices, and maintaining the walker routinely, users can take pleasure in the benefits of their rollator with reduced risk. Ultimately, the goal is to facilitate self-confidence and stability, enabling individuals to browse their world with security and ease. As care providers, family members, and neighborhoods prioritize safety, they empower users towards a much better, more independent quality of life.
In recent years, online scams have proliferated, with phishing being one of the most common threats faced by internet users. To address this growing concern, the Federal Trade Commission (FTC) has developed the "On Guard Online" platform, which includes an interactive game designed to educate users about phishing scams. This article presents an observational study of this game, focusing on its educational value, user engagement, and potential for raising awareness about phishing attacks.
To address this growing concern, the Federal Trade Commission (FTC) has developed the "On Guard Online" platform, which includes an interactive game designed to educate users about phishing scams. This article presents an observational study of this game, focusing on its educational value, user engagement, and potential for raising awareness about phishing attacks.
The "On Guard Online" game allows users to navigate through a series of simulated email scenarios where they must identify phishing attempts. Players are presented with various email messages, some of which contain genuine content while others are designed to deceive. The objective is to recognize the red flags associated with phishing attacks, such as suspicious links, generic greetings, and urgent requests for personal information. Participants are scored based on their ability to discern legitimate communications from fraudulent ones.
Observational research techniques were employed during gameplay sessions with a group of ten participants—five high school students and five adults. The data collection included noting the time taken to complete the game, the choices made by each participant, and their discussions during the gameplay. Participants were encouraged to think aloud and articulate their thoughts regarding the emails presented. This qualitative approach allowed us to gain insights into their cognitive processes and strategies when identifying phishing attempts.
The preliminary findings suggest that the game is effective in engaging users and enhancing their understanding of phishing tactics. Participants demonstrated heightened awareness while progressing through the game. High school students displayed a commendable ability to recognize numerous phishing elements, often discussing their thought processes with enthusiasm. Some students voiced concerns over how realistic and relatable the scams felt, demonstrating that they understood the implications of phishing beyond simply recognizing fraudulent emails.
Adults in the group, however, exhibited different levels of confidence and familiarity with online scams. While some adults swiftly identified deceptive emails, others expressed hesitation and uncertainty. Notably, participants who reported prior experiences with phishing scams were more adept at spotting potential threats. This variation in performance highlights the importance of experience in recognizing phishing attempts and underscores the need for ongoing education regardless of age.
One interesting observation involved the emotional responses elicited during gameplay. Participants expressed feelings of frustration when they failed to identify phishing attempts and excitement when they successfully navigated a tricky email. This suggests that the game could be effectively utilized as both an educational tool and an engagement strategy that makes learning about online safety enjoyable.
The game's design, which incorporates interactive elements, colorful graphics, and real-life scenarios, contributes to its effectiveness as a teaching tool. Participants appreciated the user-friendly interface, making it accessible for players of varying ages and technological proficiency. The interactive nature of the game encouraged repeated play; many participants indicated they would return to strengthen their skills further.
Despite its strengths, there are areas for improvement. Although the game covers fundamental aspects of phishing scams, there is potential for expanding content to include other online safety tips, GOOGLE DELETE PHISING such as safeguarding social media accounts and recognizing different forms of scams. Additionally, incorporating a feedback mechanism could enhance learning; providing explanations for why certain emails were categorized as phishing would deepen understanding.
Overall, the observations made during this study underline the necessity of proactive measures in combating phishing scams. As cyber threats evolve, the need for effective education continues to grow. The FTC's "On Guard Online" phishing scams game is a commendable step towards empowering users with knowledge and skills to protect themselves online. It effectively fosters critical thinking and situational awareness, equipping participants with the tools needed to navigate the digital landscape securely.
In conclusion, while the "On Guard Online" phishing scams game has proven to be a valuable resource for raising awareness and educating users about the nuances of online fraud, there is ongoing room for enhancement. As the landscape of cyber threats changes, educational tools must adapt and innovate to provide comprehensive, relevant experiences for users. Continued observational research into user interactions will be essential in refining these approaches, ultimately creating a safer online environment for all.
In the age of digital communication, online phishing has emerged as one of the most persistent and damaging threats to personal and organizational security. Phishing is a form of cybercrime where attackers attempt to deceive individuals into providing sensitive information such as usernames, passwords, credit card numbers, and bank details. This article will delve into the mechanics of phishing attacks, their various forms, the impact they have on individuals and organizations, and measures that can be taken to protect against such threats.
What is Phishing?
Phishing typically involves an attacker masquerading as a trustworthy entity in electronic communications. The most common vector for phishing attacks is email, where the attacker sends messages that appear to be from legitimate sources, such as banks, online service providers, or well-known brands. These emails often contain links to fraudulent websites designed to look like the legitimate ones, tricking victims into entering their personal information.
While phishing is historically linked to email, the problem has evolved over the years. Attackers now use various methods to reach victims, including social media platforms, instant messaging, and even phone calls, adding a layer of complexity to detection and prevention.
Different Types of Phishing
- Spear Phishing: Unlike traditional phishing attacks that target a large number of people, spear phishing is personalized and aims at specific individuals or organizations. Attackers may gather information from social media profiles or other publicly available resources to create tailored messages that increase the likelihood of success.
The Impact of Phishing
The consequences of phishing can be severe. For individuals, falling victim to a phishing attack can result in identity theft, financial loss, and significant emotional distress. For organizations, the ramifications are even graver—data breaches can lead to substantial financial losses, erosion of customer trust, legal penalties, and damage to brand reputation. According to a report from cybersecurity firms, phishing accounts for a majority of data breaches. Organizations have found themselves investing heavily in cyber defense mechanisms as a direct response to these threats.
Recognizing Phishing Attempts
Spotting a phishing attempt can be challenging, especially as attackers constantly refine their techniques. However, there are several red flags that can help individuals and organizations identify potential phishing attempts:
- Unusual Sender Email Addresses: Attackers often create email addresses that closely resemble legitimate ones but may contain subtle misspellings or additional characters.
Prevention Measures
To effectively combat phishing, individuals and organizations must adopt a proactive approach. Here are some best practices:
- Education and Training: Regular training sessions on identifying phishing attacks can equip employees with the knowledge they need to recognize threats before they escalate.
Conclusion
As the digital landscape continues to evolve, so do the tactics employed by cybercriminals. Phishing remains one of the most common and dangerous forms of cyberattacks, but by understanding the methods used, GOOGLE DELETE PHISING recognizing warning signs, and implementing effective preventive measures, both individuals and organizations can defend against this pervasive threat. Awareness and vigilance are essential in safeguarding sensitive information in today's interconnected world.
Introduction

Just about Arrange Vanatera CBD
Order Vanatera CBD is a noteworthy nominate in the Earth of CBD, recognised for Vanatera CBD Review its inscription to calibre and customer gratification. The firebrand was constituted with a charge to cede pure, effective, and rubber CBD products, accenting natural health. Purchase order Vanatera takes superbia in its consignment to producing CBD products that stick to strict choice standards, ensuring that consumers experience the fully benefits of CBD without unwanted additives.
Mathematical product Offerings
Holy Order Vanatera CBD offers a divers browse of CBD products configured to ply to diverse consumer of necessity. Their merchandise business line includes:
- CBD Inunct Tinctures: Usable in unlike concentrations, these tinctures are crafted for easygoing dose and agile absorption, devising them a democratic prize for individuals quest substitute from anxiety, pain, or slumber disorders.
- CBD Capsules: For those World Health Organization favor a Sir Thomas More traditional supplementation form, Vanatera's CBD capsules provide a ready to hand and exact mode to integrate CBD into each day routines.
- Topicals: This run includes creams and balms infused with CBD, targeting localised sculptural relief for articulation pain in the neck and muscleman rawness.
- Edibles: From gummies to chocolates, Vanatera's edibles fling a delightful style to savour the benefits of CBD, imploring to those WHO favour a tasty uptake method.
- Ducky Products: Recognizing the potential drop benefits of CBD for pets, Vanatera provides especially formulated products that bread and butter the health of furred companions.
Manufacturing and Choice Control
Set up Vanatera CBD places firm stress on the calibre and sinlessness of its products. They reference cannabis from organically big plants, ensuring that no pesticides or noxious chemicals are victimised in the finish cognitive operation. The stain employs CO2 extraction, a method praised for its power to keep the integrity of the plant’s cannabinoids and terpenes without leaving harmful residues.
Moreover, Vanatera is committed to transparence and timbre self-assurance. Every product tidy sum undergoes comprehensive examination third-company science laboratory testing for potency, purity, and safety device. These research laboratory reports are made accessible to consumers, allowing them to aver the mental object of the products they buy.
Commercialise Position
Ordering Vanatera CBD has positioned itself in the exchange premium segment of the CBD grocery store. Its concentre on tone and innocence resonates with consumers who are mindful of what they take in. Through a direct-to-consumer model, Vanatera maintains a unattackable online presence, offer a unseamed shopping know. The sword likewise engages strategically through with sociable media channels, enabling it to relate with a health-conscious, digital-grasp audience.
Consumer Reception
The receipt of Consecrate Vanatera CBD by consumers has been largely plus. Many customers congratulations the brand name for the effectivity of its products and the promptitude of its customer military service. Testimonials a great deal play up improved well-being and assuagement from diverse ailments, from chronic hurt to anxiety, as headstone benefits. The transparency regarding product ingredients and laboratory results has bolstered consumer trust, foster enhancing Vanatera's repute as a reliable CBD supplier.
However, the like many in the industry, Vanatera faces challenges related to consumer Education Department and regulative changes. Close to consumers stay on unbelieving all but the efficacy and legality of CBD products, necessitating ongoing efforts to ply clear, precise information.
Conclusion
Rate Vanatera CBD stands kayoed as a reputable stigmatise in the crowded CBD commercialize by prioritizing quality, transparency, and consumer atonement. Its various raiment of products caters to a all-encompassing swan of needs, from good wellness seekers to odd newcomers. As the marketplace continues to evolve, Order of magnitude Vanatera CBD is well-positioned to sustain its height as a drawing card by continuing to introduce and hold fast to mellow standards. As the diligence and securities industry dynamics shift, Vanatera's loyalty to excellence and consumer instruction testament in all likelihood period of play a determinant office in its continued success.
