Strona blogu
Severe hypoglycemia can be life-threatening if a person does not receive treatment. Bottom line, the appropriate blood sugar level varies from person to person. If you are worried about what fluctuating levels can mean for your health, visit your doctor to discuss strategies for keeping your blood sugar at the appropriate level. What does a high blood sugar/glucose level mean? If insulin is prescribed, your doctor will show you how, when, and how much you would need if ever your blood sugar is high. Results showed that people with lower blood glucose levels were able to remember more words compared to people with high blood sugar. Sage leaves have long been used as a remedy against diabetes, with research suggesting they could help lower blood sugar levels. Diet is key when trying to lower blood sugar. A non-diabetic hypoglycemia diet can help keep blood sugar levels balanced. The liver then releases glucose back into the bloodstream to normalize blood sugar levels.
Insulin helps the body’s cells to absorb sugar from the bloodstream. If a person has a problem with their kidneys, medication can build up in their bloodstream. The kidneys help the body process medication and excrete waste. In people without diabetes, hypoglycemia can result from the body producing too much insulin after a meal, causing blood sugar levels to drop. Blood sugar levels below 70 mg/dl can indicate hypoglycemia. According to the American Diabetes Association, blood glucose levels below 70 mg/dl could lead to a condition known as hypoglycemia. A recent study published in the journal Neurology determined that lower blood sugar levels could prevent memory loss. People with lower blood sugar also displayed higher levels of activity in the hippocampus. After each participant’s blood glucose levels were monitored, participants were asked to complete a test by recalling a list of 15 words they had heard 30 minutes ago. If the doctor suspects hypoglycemia, they may perform a blood test.
You may have appointments with specialists (like a cardiologist) in addition to your primary care visits. That sounds like excellent starting advice. Shortness of breath, breath that smells like fruit, nausea, vomiting and dry mouth are symptoms of ketoacidosis. Hypoglycemia’s symptoms include nausea, anxiety, mood changes, fatigue, dizziness, trouble sleeping, and Stimula Blood Sugar Ingredients even seizures. This has resulted in astronomically better outcomes for people with diabetes, and closed-loop control is around the corner that will improve things even further.Diabetes is unique in the amount of measurement and control we have over the feedback loops at play, but it doesn’t have to be. Although Dr. Flöel and her colleagues are confident that lower blood sugar levels equate to better memory skills, keeping blood glucose levels at an even keel is still important to our health. When a person’s blood sugar levels are low, the pancreas releases a hormone called glucagon. When levels fall too low, the body does not have enough energy to function fully. For Gluco Maxum adults with long-standing type 2 diabetes who have or are at risk for cardiovascular disease, intensively lowering blood sugar to near-normal levels appears to be too risky. While it’s always important to maintain healthy blood sugar levels, new research shows that better control during the first year can reduce the future risk for complications, including kidney disease, eye disease, stroke, heart failure and poor circulation to the limbs.
The first year after diagnosis is a crucial time for patients with Type 2 diabetes. A new study, led by Neda Laiteerapong, MD, assistant professor of medicine at the University of Chicago, analyzed Health Charm Blood Sugar Review records of more than 34,000 patients to review their hemoglobin A1C (HbA1C) values in the years after their initial diagnosis. ’s lead author Agnes Flöel, M.D., of Charité University Medicine in Berlin, Germany. She is the creator of the cleanse, "S.O.U.P. - Superfoods. Organic. Uniquely designed. Prepared with Love." Goodman is also the author of Cancer Hacks, a best-selling story about her journey with cancer. Plus, fatty fish is an excellent source of protein that will help you feel full and Glyco Boost Supplement manage your weight with ease. The above mentioned herbal cure prepared from the extract of herbs and plant products could lower blood glucose effectively in people and hence, provides the most effective ways to people who want to know how to treat diabetes mellitus problem with ease. In people with diabetes, taking too much insulin can cause blood sugar levels to drop too low. Treatments focus on returning blood sugar to safe levels. This type of buildup can change blood sugar levels and lead to hypoglycemia.
In today's digital age, online shopping has become a routine for millions, with Walmart being one of the largest retailers globally. However, the convenience of online shopping also comes with significant risks, particularly from phishing scams that target unsuspecting users. Phishing involves tricking individuals into providing personal information or login credentials to malicious websites posing as authentic ones. As such, GOOGLE DELETE PHISING it’s crucial to adopt strategies to ensure safe online shopping experiences, particularly on sites like Walmart.
1. Recognize Phishing Tactics
First and foremost, awareness is key. Phishing scams can take many forms, including emails, text messages, or even calls purportedly from Walmart. Some common tactics include:
- Spoofed Emails: These appear to be from Walmart but contain malicious links. They often create a sense of urgency or a compelling reason to click through.
2. Utilize Browser Security Features
Modern web browsers offer a range of security features that can help prevent phishing attacks. These include:
- Phishing Protection: Most browsers have options you can enable to warn you about potentially harmful sites.
3. Adjust Account Security Settings
Strengthening your Walmart account’s security settings can significantly reduce phishing risks. Consider the following:
- Set Up Two-Factor Authentication (2FA): Utilize 2FA if available. This adds an additional layer where a second confirmation (like a text message or email) is required before accessing your account.
4. Monitor Your Activity
Regularly monitoring your account activity can uncover unauthorized transactions early. Set aside time each week to:
- Review Your Orders: Check your recent purchases to ensure all transactions are legitimate.
5. Educate Yourself and Others
Sharing knowledge about the various phishing schemes prevalent today can help safeguard your friends and family. Conduct discussions or share articles about:
- Recognizing Phishing Emails: Teach them what email headers could indicate a scam.
6. Use Security Software
Invest in reputable security software that includes features for phishing protection. These tools can:
- Identify Threats: Flag suspicious websites before you interact with them.
7. Report Suspicious Activity
If you encounter a phishing attempt, report it immediately. Walmart has channels for reporting scams, and you can also report phishing emails to your email provider. Reporting these instances can help improve overall internet safety for everyone.
In conclusion, while Walmart remains a convenient shopping option, users must take proactive steps to protect themselves against phishing scams. By recognizing phishing attempts, using web browser security features, enhancing account security, monitoring account activity, educating others, employing security software, and reporting suspicious activity, shoppers can significantly mitigate the risks of phishing when navigating the online shopping landscape.
Understanding the Appeal of Bunk Beds for Sale: A Comprehensive Guide
uk bunk beds beds have actually long been a staple of youth and household living spaces, using a smart option to the seasonal problem of optimizing space. Whether for a shared space or a visitor space, the versatility of bunk beds can accommodate different requirements, making them an excellent option for families, hostels, or momentary accommodations. This short article explores the appeal of bunk beds for sale, factors to consider to keep in mind when purchasing, and responses to some often asked concerns.
Why Choose Bunk Beds?
bunk bed near me beds stay popular for lots of engaging reasons:
Space Efficiency: Bunk beds allow 2 or more individuals to sleep in the footprint of a single bed. This is especially advantageous in small bed rooms where space is restricted.
Cost-Effective: By integrating sleeping arrangements, bunk beds can save money on buying 2 different beds, making them a cost-effective option for households or budget-conscious individuals.
Fun Design: Bunk beds are frequently developed with kids in mind. They use an aspect of fun and experience, turning bedtime into a delightful experience.
Adaptability: Many bunk beds are created to convert into different beds. This feature permits versatility as kids grow or as family dynamics alter.
Storage Solutions: Many modern-day bunk beds include built-in storage solutions like drawers and racks, decreasing clutter and taking full advantage of energy.
Table: Types of Bunk Beds for Sale
| Kind Of Bunk Bed | Description | Suitable Use Case |
|---|---|---|
| Standard bunk beds near me Bed | 2 beds stacked on top of each other. | Shared kids's room, visitor spaces. |
| L-Shaped Bunk Bed | Bunks arranged in an L-shape, typically with a lower desk or play area. | Corner spaces, children requiring extra play area. |
| Loft Bed | A single bed lifted with space beneath for a desk, sofa, or storage. | Small bedrooms requiring work area, college dormitories. |
| Triple Bunk Bed | Three beds stacked vertically. | Large families, pajama parties, or shared areas. |
| Bunk Bed with Slide | Consists of a slide for fun while climbing up down. | Children's spaces, especially fit for adventurous kids. |
What to Consider When Buying a Bunk Bed
Before choosing a bunk bed, possible buyers ought to think about several elements:
Safety Standards: Ensure that the bunk bed satisfies safety guidelines. Look for safety functions such as guardrails and safe ladders.
Material: Bunk beds are generally made from metal, wood, or a combination. Choose a material that suits the wanted visual and toughness requirements.
Weight Capacity: Check the optimum weight limit for the bed, guaranteeing it can effectively support the users.
Height of the Room: Measure the height of the room to guarantee that there suffices space in between the leading bunk and the ceiling for safety and comfort.
Style and Style: Consider how the bed will fit into the existing decoration. Choices range from timeless wooden surfaces to modern-day metal styles.
Assembly Requirements: Some bunk beds may require substantial assembly or professional help to set up. Assess your convenience level with furnishings assembly.
Benefits of Buying Bunk Beds Online
With the increase of e-commerce, acquiring bunk beds online has actually ended up being increasingly popular. Amongst the factors for this shift are:
Wider Selection: Online markets frequently provide a broader variety of choices in regards to size, style, color, and material.
Competitive Pricing: Online merchants often offer discount rates, sales, and advertising deals, making it easier to discover economical options.
Convenience: Shopping for bunk beds online permits purchasers to search products at their convenience, read reviews, and compare rates without the pressure of in-person sales methods.
Home Delivery: Many online sellers offer delivery alternatives, making sure the bunk bed gets here straight at your door, saving time and effort.
Regularly Asked Questions (FAQs)
1. What age is appropriate for oversleeping a bunk bed?Many makers
advise that kids over the age of 6 ought to use the leading bunk for safety factors. 2. Is a bunk bed suitable for adults?Yes, many bunk beds are developed to support
adult weight. Constantly inspect the producer's specifications for weight limits. 3. How do I preserve my bunk bed for sale bed?Regularly inspect the bed for loose screws
or bolts, tidy it regularly, and
prevent overloading it with extreme weight. 4. Are there warranty choices readily available for bunk beds?Many sellers provide guarantees on their bunk beds, which can cover problems in products and craftsmanship. Always ask about guarantee alternatives when acquiring. 5. Can bunk beds fit in any room?While bunk beds are versatile, they may not appropriate for really little rooms. Measure your room and think about layout before purchasing.

In summary, bunk beds for sale provide a practical, space-saving service that accommodates various requirements, from children's shared rooms to momentary visitor lodgings. By thinking about safety, design,
and purchaser benefit, customers can make educated choices to discover the perfect bunk bed for their living environment. Whether you select a standard design, a modern-day loft, or a fun bunk bed with slides, there is ensured to be an option to match any choice and space requirement. With a careful assessment of the options offered and by utilizing the advantages that online shopping supplies, purchasers can quickly discover a bunk bed that satisfies their requirements and likewise includes a dash of enjoyment to any room.
The digital landscape is often fraught with threats, with cybersecurity companies like Avast at the forefront of protecting users from online scams. In a recent incident that has garnered widespread attention, Avast's online security software erroneously classified a legitimate website as a phishing threat, sending ripples through its user community. This mix-up has raised questions about the reliability of automated cybersecurity tools, their impact on businesses, and the rights of users navigating the internet.
The incident occurred on April 15, when users reported that Avast had blocked access to the website belonging to Legit Web, a popular platform known for its user-friendly interface and commitment to customer service. Upon trying to access the site, users were met with a stark warning from Avast, which stated that the page was a potential phishing site designed to steal personal information. This alarmed many, particularly small business owners and freelancers who relied heavily on the platform for their operations.
Following the block, a wave of complaints flooded social media as users expressed outrage. Many users stated that they felt disheartened and frustrated by the incident, emphasizing the potential loss of revenue and trust in Legit Web. "Our whole business runs on that platform, and now we have to look for alternatives," shared Maria Lopez, a graphic designer whose clientele is largely based on projects from Legit Web. "It’s not just an inconvenience; it’s detrimental to our livelihood."
In response to the rising uproar, Avast released a statement acknowledging the error. The company explained that its automated security systems rely on databases and algorithms to evaluate the safety of websites. Unfortunately, the algorithm had mistakenly flagged Legit Web due to a combination of factors, including recent changes to its URL structure and an uptick in negative reports that, upon analysis, were unfounded. The statement reassured users that the incident was being investigated and that efforts were underway to prevent such occurrences in the future.
Phishing attacks continue to be a significant concern in the cybersecurity field, with hackers constantly devising new tactics to lure unsuspecting individuals into revealing sensitive information. Consequently, security software is critical in providing users with warnings about potentially dangerous sites. However, this reliance on automated systems has a flip side, as seen in this scenario where a legitimate website is misidentified as a threat.
Experts in the field suggest that such incidents bring to light the challenges inherent in automated flagging systems. "While automated systems can process vast amounts of data quickly, there's always a margin of error," stated Dr. Michael Roberts, a cybersecurity analyst. "When these systems are mistaken, the fallout can be significant, especially for businesses that depend on their online presence. It underscores the need for a hybrid system where automated tools are supported by human oversight."
The unintended consequences of this misclassification extended beyond individual users. Legit Web's representatives reported a substantial increase in customer service inquiries, as many users were panicked by the warning and sought clarification on whether their data had been compromised. The site’s creators swiftly initiated communication with Avast to resolve the issue and ensure that users were informed about the real situation.
Online businesses thrive on trust, and an automated phishing flag can damage that trust quickly. Some business owners expressed concerns that their reputation might suffer irreparable harm due to this incident. "We’ve spent years building our brand and reputation, and now we risk losing that due to a software blunder," said Tom Harris, the CEO of Legit Web. "We hope Avast rectifies this issue quickly and reinstates our site to avoid more unnecessary damage."
In the wake of the incident, it has become increasingly essential for users to remain vigilant, understanding that while cybersecurity tools are designed to protect them, they are not infallible. VPNs, firewalls, and antivirus software provide layers of security, but the onus is also on individuals and businesses to verify the legitimacy of sites before inputting sensitive information.
Cybersecurity companies must take these missteps seriously and work towards systems that reduce the chances of wrongful blocks in the future. As Avast works to rectify the situation and the dust settles, users are left navigating the complexities of online threats with a newfound understanding: GOOGLE DELETE PHISING the fight against cybersecurity risks is a continuous battle filled with uncertainties, even from those entrusted to safeguard us.
As the story develops, users and businesses alike will be watching closely how Avast handles its response and what measures it adopts to reassure its community that they are safe in their online endeavors.
In today's digital age, phishing scams have morphed into one of the most pervasive threats to online safety, particularly for young internet users.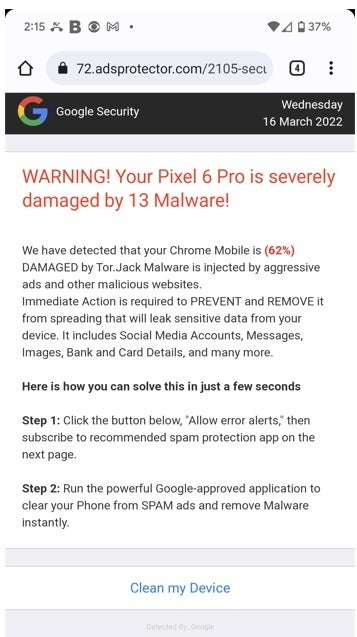 To combat this escalating issue, the Federal Trade Commission (FTC) has introduced an innovative educational game called "On Guard Online," which is specifically designed to teach children and adolescents how to recognize and avoid phishing scams. This game stands out as a noteworthy advancement in the realm of digital education, harnessing interactive learning to foster real-world skills in internet safety.
To combat this escalating issue, the Federal Trade Commission (FTC) has introduced an innovative educational game called "On Guard Online," which is specifically designed to teach children and adolescents how to recognize and avoid phishing scams. This game stands out as a noteworthy advancement in the realm of digital education, harnessing interactive learning to foster real-world skills in internet safety.
Phishing, the malicious practice of tricking individuals into revealing sensitive information such as usernames, passwords, and credit card numbers, has evolved in complexity and sophistication. Scammers employ a variety of tactics, from seemingly harmless emails to fake websites that closely mimic legitimate services. The FTC’s On Guard Online game takes a proactive approach to equip young users with the knowledge and skills they need to identify and respond to such threats.
The foundational premise of the game is built on engaging young users through an interactive online platform. Players navigate scenarios that replicate real-life phishing attempts, including emails that tempt users with fraudulent offers and social engineering tactics in online interactions. The immersive experience of the game allows players to recognize red flags associated with phishing schemes, such as poor grammar, unusual sender addresses, or urgent calls to action. By engaging with these scenarios, players learn to apply critical thinking and analytical skills to evaluate the legitimacy of online communications.
One significant advance in On Guard Online is its integration of gamification elements that enhance user engagement while promoting retention of information. The game's design includes various levels and challenges, rewarding players for successfully identifying and reporting phishing attempts. These gamified elements not only make learning enjoyable but also reinforce essential concepts of cybersecurity in a manner that resonates with the gaming preferences of younger audiences. As players progress through higher levels, they encounter increasingly complex phishing scenarios that push them to hone their skills further—ultimately preparing them to navigate the web safely.
Additionally, On Guard Online provides educational resources that go beyond the confines of the game itself. It encourages open discussions about phishing scams among players, their peers, and family members. This aspect of the game fosters a community of learners where players can share experiences and knowledge, empowering them to spread awareness within their social circles. By facilitating conversations about online safety, the game serves as a bridge between formal education and everyday internet practices, thus reinforcing the importance of cybersecurity in daily life.
The game is also a tool for educators and parents, providing them with a framework to teach children about online risks. Schools can integrate On Guard Online into their curricula, offering dedicated sessions on internet safety that are both informative and interactive. Furthermore, the FTC provides educators with guides and discussion prompts that can help facilitate classroom conversations about phishing scams. This collaborative approach ensures that the lessons learned through the game have a wider impact, extending beyond individual experiences to shape collective understanding of digital safety.
Importantly, On Guard Online reflects a growing recognition of the need for proactive strategies in internet safety education. As phishing scams continue to evolve, so too must the tools available for countering them. By adopting a forward-thinking approach, the FTC has addressed a critical gap in current online safety measures. While traditional educational programs often focus on passive learning methods, the interactive gameplay of On Guard Online empowers young users to actively engage with the material, enhancing their ability to retain and apply what they learn.
In conclusion, GOOGLE DELETE PHISING the FTC’s On Guard Online game represents a significant advancement in the fight against phishing scams targeting young internet users. By utilizing gamification and interactive learning, the FTC not only educates players about the nuances of recognizing phishing attempts but also encourages critical thinking and community engagement around the topic. As young individuals increasingly navigate a complex digital landscape, the skills honed through playing On Guard Online are essential for fostering resilient and informed internet users. This innovative approach marks a promising step forward in enhancing digital literacy and safety, ultimately contributing to a more secure online environment for all. As technology continues to evolve, so too must our educational initiatives to ensure that the next generation is equipped to face the challenges of the digital world.
 Mosquito Bite Prevention within the United States (PDF): A CDC two-page resource offering common info on how to prevent sleep without mosquito bites bites. Spider bites from spiders native to the UK are uncommon. Grasshoppers are related to crickets and have been around for more than 250 million years. This hybrid comes from Brazil and while its sting is not any extra poisonous than one in every of a honeybee, the massive numbers of killer bees that assault collectively can show fatal to animals and folks. Using many lights as an alternative of one highly effective gentle doesn't must be more expensive. Most persons are additionally familiar with the Newton experiment which consists of using a prism to decompose white mild right into a rainbow of colours (figure 1b). This experiment shows that white light is fabricated from all of the seen colors from the seen gentle spectrum, mixed in some proportions. If you're also using sunscreen, put it on first, about 20 minutes earlier than making use of the repellent. They reside in colonies in nests that they make using their saliva and Buzz BugBuster Bug Zapper X Pro Reviews chewed plant matter. Scale bugs are plant parasites.
Mosquito Bite Prevention within the United States (PDF): A CDC two-page resource offering common info on how to prevent sleep without mosquito bites bites. Spider bites from spiders native to the UK are uncommon. Grasshoppers are related to crickets and have been around for more than 250 million years. This hybrid comes from Brazil and while its sting is not any extra poisonous than one in every of a honeybee, the massive numbers of killer bees that assault collectively can show fatal to animals and folks. Using many lights as an alternative of one highly effective gentle doesn't must be more expensive. Most persons are additionally familiar with the Newton experiment which consists of using a prism to decompose white mild right into a rainbow of colours (figure 1b). This experiment shows that white light is fabricated from all of the seen colors from the seen gentle spectrum, mixed in some proportions. If you're also using sunscreen, put it on first, about 20 minutes earlier than making use of the repellent. They reside in colonies in nests that they make using their saliva and Buzz BugBuster Bug Zapper X Pro Reviews chewed plant matter. Scale bugs are plant parasites.
Legends of the Desert ends with a particular be aware of intrigue in Mario Lalli und Matthias Schneeberger‘s "Spector," which at 4:17 brings collectively the clear collaborative parts of the former’s guitar and the latter’s keys, however there are also drums and BlitzyBug bass concerned and I’m not sure who handled them. It might sound like a mystery, however there are the explanation why mosquitoes like some folks than others. Already established in forty seven states, there are enormous numbers in Texas, Florida, Georgia and North Carolina. The robotic ought to simply run straight in the route of the lamp and cease there. Cockroaches are thought of a pest in the home, but we suppose that nearly any ZapNado Bug Zapper Reviews could possibly be considered a pest if there were sufficient of them. Interestingly, termites are associated to cockroaches. Termites feed on wood, which implies your home is at risk. Adult beetles lay eggs on the bark of ash bushes and their larvae feed on the nutrition transportation tissues that the tree needs to outlive.
 Fleas, like mosquitoes, feed on the blood of mammals. A complete blood rely was carried out with no notable abnormalities. Although it’s not all the time doable to know which bug is to blame for your newest chunk (or bites), you possibly can usually get a fairly good concept based mostly in your skin, the location of the sting, and a few different clues. Talks about newest developments in corporations and in FreeBSD will present insights into future instructions. Running from floor to tree branch, Norway Rats (also known as Brown Rats and Sewer Rats) will eat every thing from eggs in nests to young chickens, rubbish and even wood! And the brown tree snake in now discovering lizards as a tasty substitute. Brown Marmorated Stink Bugs were present in 1998 in Allentown, Pennsylvania. Stink bugs destroy fruits and vegetables and were just lately detected in South Carolina, Georgia and Florida.S. They are on the verge of reaching into southern Georgia with no known predators in sight.
Fleas, like mosquitoes, feed on the blood of mammals. A complete blood rely was carried out with no notable abnormalities. Although it’s not all the time doable to know which bug is to blame for your newest chunk (or bites), you possibly can usually get a fairly good concept based mostly in your skin, the location of the sting, and a few different clues. Talks about newest developments in corporations and in FreeBSD will present insights into future instructions. Running from floor to tree branch, Norway Rats (also known as Brown Rats and Sewer Rats) will eat every thing from eggs in nests to young chickens, rubbish and even wood! And the brown tree snake in now discovering lizards as a tasty substitute. Brown Marmorated Stink Bugs were present in 1998 in Allentown, Pennsylvania. Stink bugs destroy fruits and vegetables and were just lately detected in South Carolina, Georgia and Florida.S. They are on the verge of reaching into southern Georgia with no known predators in sight.
Wasps are known as angry, stinging insects. Spiders are arachnids, which is perhaps bugs, but they aren't technically insects. The lacewing has wings which might be lacy and resemble nets. Ranson says. The group started testing the nets in 40 clusters of villages in Burkina Faso in 2014; results of the trial ought to be identified in a few weeks. That’s the equivalent of walking into the garage and seeing a couple of planks of wooden, grabbing a saw, and beginning to chop some components for the first design that popped into my head. Shoppers on a tighter finances ought to consider the Tysonir Portable Bug Zapper Reviews zapper, a lightweight and efficient zapper that’s secure for people and pets. Some individuals keep them as pets as a result of they are thought-about so cute. "This is one thing we are engaged on - the quantity and type of body odor that an individual gives off might be the rationale," Vosshall mentioned by way of e mail. "Think of it like a big protein shake," Vosshall mentioned.
The need to store or release glucose is primarily signaled by the hormones insulin and glucagon. Recent research by Science Direct suggests that more studies need to be conducted to determine the exact glycemic indexes of sweet potatoes and the impacts on glucose and glycemic response. A 20-year study suggests that a compound in full-fat dairy (trans-palmitoleic acid) boosts insulin sensitivity and blood-sugar control, often within five days. Slimming to within 10 pounds of your ideal weight takes such a burden off your pancreas, it can cut your risk of high blood sugar, insulin resistance, and full-blown diabetes five-fold, plus protect against heart disease, Harvard research suggests. That means enjoying a little full-fat dairy each day could cut your risk of blood-sugar problems by 60 percent, the study authors say. And eating a potato every day (as long as you eat the skin - and don’t deep fry it) can help you burn of those extra pounds effortlessly. And drinking 24 oz. daily can help prevent big blood-sugar surges - the sort of thing that can wear out your pancreas and lead to full-blown diabetes, say Swedish researchers.
The minerals and fiber in spuds slow carb absorption, prevent post-meal blood-sugar spikes, and increase your production of appetite-controlling serotonin, helping you shed up to 12 pounds every year if you eat one potato daily, say University of Maine researchers. The credit goes to rose hip compounds (galactolipids) that nourish the liver, helping this organ absorb and quickly burn excess sugar. Rose hip tea is a mild, tangy, fruity brew that’s delicious hot or iced. That includes anything that’s made of glass or ceramic, and plastic containers that have the recycling codes 1, 2, or 5 stamped on them. They have a protein on their surface, which helps the cells to stick to each other, and to walls of blood vessels. The complete blood count test is one of the most basic tests used for medical analysis. It is one of the most effective oils at reducing the risk of heart disease and contains a number of antioxidants that help to reduce inflammation, protect your cells, and decrease blood pressure.3 Choose pure extra-virgin olive oil to get all of the health benefits and sprinkle it on salads, use it in a marinade, or cook meats and vegetables with it.
This gives a basic picture of the health of the individual. Foods that are labeled "sugar-free" or "no sugar added" are commonly eaten to the point of discomfort because people believe that these foods have little effect on their waistline and health. Keep a record of your blood sugar testing results and how you treated low blood sugar levels so that your health care provider can Glucoflush Review the information to help adjust your diabetes treatment plan. Before starting any new dietary program, consult with your healthcare provider to make sure any changes you make to your diet are done safely. Your provider will also take your blood pressure and check the sites where you test your blood sugar and deliver insulin. Platelets are amongst the various substances present in the blood. PLT testing is done to count how many blood platelets there are in our blood. This is very sincere.Wu normal blood sugar levels on ketogenic diet Tongtian frowned slightly, Qin Yu is performance at this moment was are carbs sugar a bit unexpected. The blood itself has structures present within it that enable its normal functioning.
Medical research has led to the understanding of various typical ranges within which these structures or substances must fall. In the second study, which was a randomized controlled crossover trial published as a research letter, 10 men with type 1 diabetes drank vinegar (30 mL vinegar plus 20 mL water) or placebo (50 mL water) 5 minutes before a meal of bread, cheese, turkey ham, orange juice, butter, and a cereal bar. The dose: 2 oz. of full-fat cheese, or one cup of full-fat milk or yogurt daily. Peanuts and Order Glucose Management Gluco Ally peanut butter can be a cost-friendly addition to your daily fueling routine. Insulin can be administered by syringe, pen or pump. Also, the researchers evaluated the participants’ whole-body insulin resistance and insulin secretion. Sugar levels rise in the blood but decrease inside the cells themselves; after all, insulin is not working properly. Certain renal diseases can also lead to a decrease in blood platelets. Extremely low levels of platelets can even lead to spontaneous bleeding, which can be a life-threatening situation.
In an increasingly digital world, phishing attacks have become one of the most prevalent online threats. Among these, the Google online challenge phishing scam has gained notoriety, targeting individuals by masquerading as legitimate Google contests or competitions. Understanding how these scams operate and how to protect oneself from them is crucial for both personal and organizational security.
Phishing is a form of cybercrime where attackers gain access to sensitive information by pretending to be a trustworthy entity. The Google online challenge phishing technique exploits users’ familiarity and trust in Google services. Scammers create convincing replicas of real Google platforms, including emails, websites, or ads that appear to be linked to legitimate competitions or offers. These phishing emails often contain urgent messages that prompt recipients to click on a link, leading them to a fraudulent site where they are asked to enter personal information, such as usernames, passwords, or credit card details.
One prominent example of this phishing tactic involves unsolicited emails that claim the recipient has won a prize in a Google-sponsored contest. The email may include attractive prizes ranging from cash rewards to popular gadgets, creating a sense of excitement and urgency. Unsuspecting victims, believing they just won a major prize, may hastily enter their personal information on the provided link without scrutinizing the source of the communication. Once entered, this personal data is harvested by the attackers for malicious use.
The design of these fraudulent communications can be highly convincing. Phishers use official logos, colors, and branding elements to create a credible front, making it challenging for average users to differentiate between genuine and fake. In some cases, the email may appear to come from an official GOOGLE DELETE PHISING domain or might use subtle variations in the email address that still look similar to real Google accounts (e.g., google-contest@gmail.com instead of an official google.com email address).
The consequences of falling victim to a phishing scam can be severe. In addition to identity theft and financial loss, victims may find themselves facing account takeover, where attackers can gain access to email accounts, social media, and online banking. Furthermore, the spread of malware is another risk. Links provided in phishing emails may lead to sites that infect users’ devices with harmful software, causing further complications and losses.
Protecting oneself from the Google online challenge phishing scam requires vigilance and a proactive approach. Here are some essential strategies for identifying and avoiding phishing attempts:
- Scrutinize Email Addresses: Always check the sender’s email address, looking for misspellings or unusual domain names. Official communications from Google will come from recognized Google domains.
In conclusion, the threat of Google online challenge phishing is indicative of the broader issues surrounding online security. As cybercriminals become increasingly sophisticated, it is crucial for individuals and organizations to remain vigilant and informed. By understanding the mechanics of these scams and implementing preventive measures, we can help thwart the continuing efforts of phishers and safeguard our online presence. Always remember—when in doubt, it’s best to err on the side of caution and verify before you act.
In the digital age, where information and communication flow seamlessly across platforms, cybersecurity has become a paramount concern for individuals and organizations alike. Among the myriad of threats that plague the internet, phishing stands out as one of the most nefarious tactics employed by cybercriminals. One particularly alarming trend that has emerged in recent times is the phenomenon of Google Online Challenge phishing, a sophisticated strategy that targets users by masquerading as legitimate competitions or opportunities associated with Google. Understanding how this type of phishing works and recognizing its dangers is essential for safeguarding personal and professional digital spaces.
Phishing, by definition, is a malicious attempt to obtain sensitive information from individuals by disguising as a trustworthy entity. The Google Online Challenge phishing scheme capitalizes on the legitimacy and popularity of Google's branding. Cybercriminals create fake competitions or challenges, often featuring attractive prizes such as cash rewards, gadgets, or exclusive access to events. These schemes typically entice participants with promises of high rewards for minimal effort, which effectively lures users into participating without fully vetting the authenticity of the opportunity.
One of the key mechanisms these phishing attempts employ is social engineering. By exploiting psychological triggers like curiosity, greed, and the fear of missing out (FOMO), scammers can manipulate victims into providing their personal information, such as passwords, credit card numbers, or social security numbers. Often, these phishing emails or messages will contain links that direct victims to counterfeit web pages designed to look almost identical to legitimate Google sites. This attention to detail serves to instill trust and encourages victims to enter sensitive information, believing they are participating in a genuine challenge.
To illustrate how insidious this phishing tactic can be, consider a typical scenario: an unsuspecting user receives an email claiming they have been selected as a finalist in a prestigious Google Online Challenge. The email features Google’s logo, official language, and a sense of urgency, urging them to click a link and confirm their identity to claim their prize. Upon clicking the link, they are directed to a near-perfect replica of a Google login page. Here, the user is prompted to enter their credentials, unknowingly handing over access to their Google account to the scammers.
This not only puts the individual’s personal information at risk but can also have broader implications for organizations. If an employee falls victim to such a scheme, it could compromise sensitive company data, client information, and proprietary business strategies, leading to significant financial and reputational damage.
Preventing the spread of GOOGLE DELETE PHISING Online Challenge phishing requires both technical and behavioral measures. First and foremost, education and awareness are crucial. Users should be educated about the signs of phishing attempts, such as misspellings, unusual sender addresses, and suspicious links. Organizations should implement regular training sessions to keep employees informed of the latest phishing tactics and encourage vigilance when navigating online communications.
Moreover, employing technical security measures can bolster defenses against phishing. Multi-factor authentication (MFA) adds an additional layer of security, making it more difficult for hackers to gain unauthorized access even if they have obtained login credentials. Email filters and anti-phishing software can help detect and block phishing attempts before they reach users' inboxes.
In addition, users should take advantage of Google’s security features, like the built-in phishing protection tools in Gmail, which scan messages for potentially harmful links and warn users of suspicious activity. Regularly updating passwords and using unique passwords for different platforms can also minimize the risks associated with account compromises.
Furthermore, it is vital for tech giants like Google to continually enhance their cybersecurity measures and collaborate with law enforcement to identify and apprehend cybercriminals behind these phishing schemes. Prompt reporting of phishing attempts can help in curtailing their proliferation.
In conclusion, the emergence of Google Online Challenge phishing underscores the ever-evolving nature of cyber threats. As digital interactions grow in complexity and frequency, so too does the ingenuity of cybercriminals attempting to exploit them. Vigilance, education, and robust security measures are paramount in navigating this perilous landscape. By remaining aware of the tactics employed by scammers and taking proactive steps to protect personal and organizational information, individuals can contribute to a safer online environment. The battle against phishing may be ongoing, but with collective effort and awareness, we can mitigate the damage inflicted by these malicious schemes.
In the digital age, the importance of cybersecurity cannot be overstated. Phishing scams pose a significant threat to individuals and businesses alike. To combat this menace, the Federal Trade Commission (FTC) has created an interactive and educational tool known as the OnGuard Online Phishing Scams Game. This game not only entertains but also equips users with the knowledge and skills necessary to identify and avoid phishing scams. In this article, we will explore the game's purpose, how it operates, and the significance of understanding phishing in today's world.
The Purpose of OnGuard Online
OnGuard Online is an initiative led by the FTC to provide resources for individuals looking to protect themselves from various online threats. The site offers practical tips, resources, and interactive solutions designed to educate users about cybersecurity. One of the standout features of the website is the Phishing Scams Game, which allows players to learn about phishing scams through an engaging and relatable medium.
What is Phishing?
Phishing is a form of cybercrime where attackers deceive individuals into providing sensitive information such as usernames, passwords, credit card numbers, and other personal details. This is often achieved through seemingly legitimate emails or GOOGLE DELETE PHISING messages that mimic trustworthy sources. By clicking on malicious links or providing information, victims unwittingly reveal their data to criminals, leading to identity theft and financial losses.
How the Game Works
The OnGuard Online Phishing Scams Game leverages interactive storytelling to educate players. The game presents various scenarios where players must identify whether a message is a phishing attempt or a legitimate communication. As they proceed, players are given subtle hints and information regarding the nature of phishing scams.
- Scenario-Based Learning: Each level introduces a new scenario, such as an email from a bank asking for verification or a message claiming the user has won a prize. Players must analyze these communications critically to determine their authenticity.
Benefits of Playing
The OnGuard Online Phishing Scams Game offers numerous benefits for individuals of all ages. Here are a few compelling reasons to engage with this educational tool:
- Enhancing Critical Thinking: The game encourages players to think critically about the messages they receive online. This enhanced awareness can translate into better decision-making when navigating the internet.
The Importance of Awareness
In conclusion, the FTC's OnGuard Online Phishing Scams Game serves as an essential tool in the ongoing fight against cybercrime. By familiarizing users with the tactics employed by scammers and equipping them with knowledge to identify phishing attempts, the game plays a crucial role in enhancing cybersecurity awareness. As phishing scams continue to evolve, ongoing education and awareness will remain vital in protecting personal and financial information. The lessons learned from this game not only prepare individuals to defend against phishing but also contribute to a more secure internet for everyone.
