Strona blogu
Phishing is a form of cybercrime that involves tricking individuals into revealing sensitive information, such as usernames, passwords, credit card details, or other personal data. This is generally done through deceptive emails, fake websites, or instant messages. As the internet continues to evolve and become a crucial aspect of daily life, online phishing schemes are becoming increasingly sophisticated, posing significant risks to individuals and organizations alike. Understanding the mechanisms behind these threats is essential for enhancing online security and preventing fraud.
The Mechanics of Phishing
Phishing attacks typically employ social engineering techniques to manipulate users into giving up their information. Attackers often impersonate legitimate entities, such as banks, e-commerce sites, or even colleagues within a workplace. The initial contact usually comes in the form of an email, but phishing can also occur via text messages (known as smishing), phone calls (vishing), or social media platforms.
Upon encountering a phishing attempt, users may receive an email that appears authentic but contains a sense of urgency or threat. For example, the email may claim that there is an issue with their account or that immediate action is required to resolve a security concern. This urgency can pressure users into clicking links that lead to counterfeit websites designed to look identical to the legitimate sites.
Types of Phishing Attacks
- Email Phishing: The most recognized form, where attackers send fraudulent emails mimicking trusted entities. The emails often contain harmful links or attachments that can compromise security.
Risks Associated with Phishing
The ramifications of falling for a phishing scam can be severe. Individuals may experience identity theft, financial loss, and emotional distress. For organizations, phishing can lead to data breaches, loss of sensitive information, financial losses, and damage to reputation. Additionally, the fallout can extend to customers, clients, and other stakeholders who trust the organization that has been compromised.
Furthermore, phishing can lead to ransomware attacks, where hackers lock access to systems and demand ransom for the decryption key. Such attacks can immobilize businesses and lead to lengthy recovery times, costing not just money but creating long-lasting reputational damage.
Signs of Phishing Attempts
Identifying phishing attempts is crucial to preventing them. Common signs include:
- Misspellings or grammatical errors in the email content.
Preventive Measures
Preventing phishing attacks involves a combination of technology, awareness, and best practices. Here are some effective strategies:
- Education and Training: Regularly educating employees and individuals about phishing tactics can improve awareness and response to suspicious emails or messages.
Conclusion
Phishing remains a pervasive threat in the digital age, exploiting human vulnerabilities and advancing technologies. As attackers devise new strategies, GOOGLE DELETE PHISING it is vital for individuals and organizations to stay informed about the latest phishing tactics and implement robust preventative measures to safeguard sensitive information. Awareness and education play critical roles in combating phishing and ensuring a more secure online environment for everyone. Only through proactive engagement can we hope to minimize the risks posed by these malicious attacks and protect our digital identities.
In recent years, cannabidiol (CBD) has emerged as a popular wellness supplement, thanks to its potential therapeutic benefits without the intoxicating effects associated with its cousin, THC. Derived from the hemp plant, CBD is incorporated into various products, each offering unique benefits. This article delves into Five CBD Supplement popular CBD supplements to consider for enhancing your health and wellness routine.
1. CBD Oil Tinctures
CBD oil tinctures are among the most widely used CBD products. Typically, these tinctures are made by infusing CBD extract into a carrier oil, such as coconut or hemp seed oil. Users can take them sublingually (under the tongue) for faster absorption or Five CBD Ingredients incorporate them into foods and beverages. CBD oil is known for its potential in managing anxiety, reducing pain, and improving sleep. The versatility of tinctures allows for easy dosage adjustments to meet individual needs, Five CBD Supplement making it a preferred choice for many.
2. CBD Capsules and Softgels
 For those seeking a convenient and discreet way to consume CBD, capsules and softgels are an excellent option. These are pre-measured, eliminating the guesswork involved in dosing. Capsules and softgels are made by encapsulating CBD oil, which is then digested and metabolized by the body. Reports suggest they may help alleviate symptoms of chronic pain, anxiety, and inflammation with consistent use. Due to their familiarity and ease of incorporation into daily routines, they are popular among those new to CBD supplements.
For those seeking a convenient and discreet way to consume CBD, capsules and softgels are an excellent option. These are pre-measured, eliminating the guesswork involved in dosing. Capsules and softgels are made by encapsulating CBD oil, which is then digested and metabolized by the body. Reports suggest they may help alleviate symptoms of chronic pain, anxiety, and inflammation with consistent use. Due to their familiarity and ease of incorporation into daily routines, they are popular among those new to CBD supplements.
3. CBD Gummies
CBD gummies offer a fun and flavorful way to enjoy the benefits of CBD. These chewy candies are infused with CBD oil and come in various flavors, shapes, and potencies. They are particularly appealing to those who dislike the taste of natural oils. Besides their palatability, CBD gummies provide an alternative for those looking to manage stress, anxiety, and Five CBD sleep disorders. However, it’s essential to consume them mindfully, as the sugar content can be counterproductive to the health-conscious.
4. CBD Topicals
Topical CBD products, such as creams, lotions, and balms, are applied directly to the skin. They target localized pain relief, making them ideal for individuals suffering from arthritis, muscle soreness, or skin conditions. By interacting with cannabinoid receptors in the skin, they may reduce inflammation and provide soothing effects without entering the bloodstream. This characteristic makes them a preferred method for athletes or those with physically demanding lifestyles who need quick, localized relief.
5. CBD Beverages
An increasing trend in the wellness industry is the infusion of CBD into beverages such as teas, coffees, and energy drinks. These beverages offer a refreshing way to consume CBD, often combined with other health-enhancing ingredients. They are touted for their potential in promoting relaxation, enhancing mood, and providing a mild energy boost. CBD coffee, for instance, aims to deliver alertness without the jittery effects, while CBD tea may offer calming benefits at the end of a busy day.
In conclusion, CBD supplements present a myriad of ways to experience the potential benefits of cannabidiol. From oils to edibles and topicals, there’s a CBD product for almost every preference and lifestyle. However, it’s important to consult with a healthcare professional before starting any new supplement, especially for those with existing health conditions or who are pregnant or nursing. As research into CBD continues, more light will be shed on its benefits, ensuring its place in the future of natural wellness solutions.
$19.99
– $55.00
All Natural | Grain Free | CBD Dog Treats
<\/p>
Chicken, Peas, Garbanzo Beans, Sweet Potatoes, Chicken Fat (Preserved with Mixed Tocopherols), Tapioca Starch, Hemp-Derived Cannabidiol (CBD*), Flaxseed Meal, Dried Blueberries, Pomegranate, Salt Powdered D Cellulose, Calcium Carbonate, Dried Cranberries, Pomegranate, Chicory Root, Kelp, Pumpkin,
Dried Apples, Dried Carrots, Broccoli, Parsley, Papaya, Spinach, Kale Powder, Rosemary Extract, Vitamin A Supplement, Minerals (Zinc Sulfate, Copper Sulfate, Manganese Sulfate, Calcium Iodate, Sodium Selenite).
<\/p>
GUARANTEED ANALYSIS:<\/strong>
Crude Protein (Min) 17% \/ Crude Fat (Min) 13% \/ Crude Fiber (Max) 5% \/ Moisture (Max) 12% \/ Zinc (Min) 150mg\/kg \/ Vitamin A (Min) 5000kcal\/kg \/ Calorie Content: (Calculated) 3499 kcal\/kg \/ Calorie Content: (Calculated) 25 kcal\/treat.<\/p>
<\/div>Read more<\/a><\/p>
","variation_id":8110318,"variation_is_active":true,"variation_is_visible":true,"weight":"","weight_html":"N\/A","has_lab_report":true}, CBD Dog Treats<\/p>
Chicken, Peas, Garbanzo Beans, Sweet Potatoes, Chicken Fat (Preserved with Mixed Tocopherols), Tapioca Starch, Hemp-Derived Cannabidiol (CBD*), Flaxseed Meal, Dried Blueberries, Pomegranate, Salt Powdered D Cellulose, Calcium Carbonate, Dried Cranberries, Pomegranate, Chicory Root, Kelp, Pumpkin,
Dried Apples, Dried Carrots, Broccoli, Parsley, Papaya, Spinach, Kale Powder, Rosemary Extract, Vitamin A Supplement, Minerals (Zinc Sulfate, Copper Sulfate, Manganese Sulfate, Calcium Iodate, Sodium Selenite).
<\/p>
GUARANTEED ANALYSIS:<\/strong>
Crude Protein (Min) 17% \/ Crude Fat (Min) 13% \/ Crude Fiber (Max) 5% \/ Moisture (Max) 12% \/ Zinc (Min) 150mg\/kg \/ Vitamin A (Min) 5000kcal\/kg \/ Calorie Content: (Calculated) 3499 kcal\/kg \/ Calorie Content: (Calculated) 25 kcal\/treat.<\/p>
<\/div>Read more<\/a><\/p>
","variation_id":8110319,"variation_is_active":true,"variation_is_visible":true,"weight":"","weight_html":"N\/A","has_lab_report":true,"attributes":{"attribute_pa_cbd-dog-treats":"chicken-rice","attribute_pa_size":"150mg"},"availability_html":"","backorders_allowed":false,"dimensions":{"length":"","width":"","height":""},"dimensions_html":"N\/A","display_price":19.989999999999998,"display_regular_price":19.989999999999998,"image":{"title":"CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL","caption":"CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL","url":"https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL.jpg","alt":"CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL","src":"https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL-600x600.jpg","srcset":"https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL-600x600.jpg 600w, https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL-300x300.jpg 300w, https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL-150x150.jpg 150w, https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL-100x100.jpg 100w, https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL.jpg 650w","sizes":"(max-width: 600px) 100vw, 600px","full_src":"https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL.jpg","full_src_w":650,"full_src_h":650,"gallery_thumbnail_src":"https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL-100x100.jpg","gallery_thumbnail_src_w":100,"gallery_thumbnail_src_h":100,"thumb_src":"https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL-300x300.jpg","thumb_src_w":300,"thumb_src_h":300,"src_w":600,"src_h":600,"jb_wc_src":"https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL-300x300.jpg","jb_wc_srcset":"https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL-300x300.jpg 300w, https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL-150x150.jpg 150w, https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL-600x600.jpg 600w, https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL-100x100.jpg 100w, https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET_ChickenRice_150mg_Dog_Treats_24_WEB650px_FINAL.jpg 650w","jb_wc_sizes":"(max-width: 300px) 100vw, 300px"},"image_id":8110274,"is_downloadable":false,"is_in_stock":true,"is_purchasable":true,"is_sold_individually":"no","is_virtual":false,"max_qty":"","min_qty":1,"price_html":"$<\/span>19.99<\/bdi><\/span><\/span>","sku":"659657491169","variation_description":"
","backorders_allowed":false,"dimensions":{"length":"","width":"","height":""},"dimensions_html":"N\/A","display_price":55,"display_regular_price":55,"image":{"title":"CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL","caption":"CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL","url":"https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL.jpg","alt":"CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL","src":"https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL-600x600.jpg","srcset":"https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL-600x600.jpg 600w, https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL-300x300.jpg 300w, https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL-150x150.jpg 150w, https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL-100x100.jpg 100w, https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL.jpg 650w","sizes":"(max-width: 600px) 100vw, 600px","full_src":"https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL.jpg","full_src_w":650,"full_src_h":650,"gallery_thumbnail_src":"https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL-100x100.jpg","gallery_thumbnail_src_w":100,"gallery_thumbnail_src_h":100,"thumb_src":"https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL-300x300.jpg","thumb_src_w":300,"thumb_src_h":300,"src_w":600,"src_h":600,"jb_wc_src":"https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL-300x300.jpg","jb_wc_srcset":"https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL-300x300.jpg 300w, https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL-150x150.jpg 150w, https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL-600x600.jpg 600w, https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL-100x100.jpg 100w, https:\/\/justcbdstorefl.com\/wp-content\/uploads\/2024\/02\/CBDPET__PeanutButter_600mg_Dog_Treats_24_WEB650px_FINAL.jpg 650w","jb_wc_sizes":"(max-width: 300px) 100vw, 300px"},"image_id":8110277,"is_downloadable":false,"is_in_stock":true,"is_purchasable":true,"is_sold_individually":"no","is_virtual":false,"max_qty":193,"min_qty":1,"price_html":"$<\/span>55.00<\/bdi><\/span><\/span>","sku":"659657180223","variation_description":"
With our Organic CBD Dog Treats, you’re not just giving your dog a treat; you’re giving them a moment of pure joy and relaxation. Choose the natural, grain-free option that supports their well-being in every bite. Try our delicious flavors today and see the difference in your dog’s snacking experience!
Description
"@context": "https://schema.org",
"@type": "FAQPage",
"mainEntity": [
"@type": "Question",
"name": "What makes our CBD dog treats different?",
"acceptedAnswer":
"@type": "Answer",
"text": "Our Organic CBD Dog Treats are crafted with your pet's health and happiness in mind. They're all-natural, grain-free, and infused with high-quality CBD to support calmness and well-being."
,
"@type": "Question",
"name": " How often can I give my dog these treats?",
"acceptedAnswer":
"@type": "Answer",
"text": "While our treats are safe and natural, we recommend following the suggested serving size on the package based on your dog's weight and adjusting as needed."
,
"@type": "Question",
"name": "Are these treats safe for all dogs?",
"acceptedAnswer":
"@type": "Answer",
"text": "Yes, our treats are formulated to be safe for dogs of all sizes and breeds. However, we recommend starting with the appropriate strength for your dog's size and monitoring their response."
]
Organic CBD Dog Treats: Premium, All-Natural, and Grain-Free
Our treats come in three delectable flavors that cater to every dog’s taste:
Each flavor is carefully formulated to ensure your dog not only gets a tasty treat but also enjoys the calming benefits of CBD, perfect for dogs who need a bit of tranquility in their day.
Additional information
Chicken, Chicken & Rice, Peanut Butter
150mg, 600mg
FAQ
Our Organic CBD Dog Treats are crafted with your pet's health and happiness in mind. They're all-natural, grain-free, and infused with high-quality CBD to support calmness and well-being.
While our treats are safe and natural, we recommend following the suggested serving size on the package based on your dog's weight and adjusting as needed.
Yes, our treats are formulated to be safe for dogs of all sizes and breeds. However, we recommend starting with the appropriate strength for your dog's size and monitoring their response.
RELATED PRODUCTS
Organic Pet Treats
JustPets Cat Treats
CBD Dog Treats JustPets
CBD Oil For Cats
CBD Oil For Dogs
25 First Ave. SW STE A
Watertown, SD 57201
This product is not for use by or sale to persons under the age of 18. This product should be coarse grass used to make rope only as directed on the label. It should not be used if you are pregnant or nursing. Consult with a physician before use if you have a serious medical condition or use prescription medications. A Doctor’s advice should be sought before using this and any other supplement. All trademarks and copyrights are property of their respective owners and are not affiliated with nor do they endorse this product. These statements have not been evaluated by the FDA. This product is not intended to diagnose, treat, cure or prevent any disease. By using this site, you agree to follow the Privacy Policy and all Terms & Conditions printed on this site. Void Where Prohibited by Law. Our products contain less than 0.3% THC.
JustCBD Florida Only Website
Welcome! You must be 21+ to enter this site.
Please enter your date of birth.
As the world becomes increasingly digital, the threats that accompany online activities continue to evolve, with one of the most sinister being phishing. Phishing, a form of cybercrime that involves tricking individuals into divulging sensitive personal information such as passwords, account numbers, and credit card details, has become a prevalent issue in today's interconnected society. This article explores the alarming rise of online phishing, its various forms, and practical steps individuals and organizations can take to protect themselves from falling victim.
Phishing schemes have been around since the early days of the internet, but their complexity and prevalence have multiplied significantly in recent years. Cybercriminals are continuously finding new strategies to bypass security measures and exploit unsuspecting users. According to a recent report from the Anti-Phishing Working Group, phishing attacks increased by a staggering 220% in 2020, and the numbers have only continued to grow.
One of the primary reasons for the surge in phishing attacks is the increase in online activities spurred by the COVID-19 pandemic. The shift towards remote work and reliance on digital platforms for communication and transactions has created a fertile ground for cybercriminals. Phishing emails have become more sophisticated, often masquerading as legitimate communications from trusted organizations or government entities. For instance, email alerts about COVID-19 vaccinations or economic relief packages have been exploited by scammers to lure victims into revealing their personal information.
Phishing techniques can vary widely, but they commonly fall into three main categories: spear phishing, whaling, and clone phishing. Spear phishing targets specific individuals or organizations, using personal information to make the attack appear more credible. Whaling, on the other hand, focuses on high-profile targets such as executives or board members, often involving more elaborate tactics to gain their trust. Clone phishing occurs when an attacker creates an identical replica of a previously delivered legitimate email, replacing any legitimate links with malicious ones, and then sends it back to the victim.
In addition to email-based attacks, phishing has also expanded to include social media platforms and messaging apps, where users can be lured into clicking links or providing personal information. Scammers are adept at creating fake profiles to gain the trust of potential victims, further complicating the detection of these fraudulent activities. Even text messages, known as SMS phishing or "smishing," have become a popular avenue for attackers to reach victims directly on their mobile devices.
The consequences of falling victim to phishing attacks can be devastating. Many victims find themselves dealing with financial loss, identity theft, and numerous headaches as they work to recover their compromised accounts. In severe cases, organizations can face reputational damage, regulatory penalties, and loss of customer trust, leading to long-term implications for their business.
So, how can individuals and organizations protect themselves from the threat of phishing? Awareness and education are key components in preventing these attacks. Users should be trained to recognize the signs of phishing attempts, such as poor grammar, generic greetings, and suspicious links. Additionally, using multifactor authentication (MFA) can add an extra layer of security by requiring further verification beyond just a password.
Regularly updating passwords and using strong, unique combinations for different accounts is crucial. Password managers can help users generate and store complex passwords securely, reducing the likelihood of password reuse across accounts. Furthermore, individuals should remain cautious when clicking on links in emails or messages, especially those from unfamiliar sources. Hovering over links before clicking can reveal their true destination and help users avoid malicious sites.
Organizations should also implement comprehensive cybersecurity policies that include regular phishing simulations to train employees on how to identify and respond to phishing attempts. Strong email filtering systems can help catch phishing emails before they reach employees’ inboxes, further mitigating risk.
Ultimately, the rise in online phishing serves as a reminder of the importance of vigilance in the digital landscape. As technology continues to advance, so too will the tactics used by cybercriminals. By remaining informed, proactive, and GOOGLE DELETE PHISING cautious, individuals and organizations can better safeguard themselves against this ever-evolving threat. The digital world offers unprecedented opportunities, but it also demands a heightened awareness of security to ensure a safer online experience for everyone.
In the growing world of CBD products, Five CBD has emerged as a notable brand, aiming to deliver high-quality, full-spectrum CBD products. This report reviews their offerings, effectiveness, quality, and customer satisfaction based on available data and customer feedback.
Product Range and Ingredients
Five CBD offers a comprehensive range of products including CBD oils, gummies, capsules, and chocolates. Their products stand out due to their full-spectrum nature, which means they contain a wide range of cannabinoids, Order Five CBD terpenes, and flavonoids, in addition to CBD. This is believed to enhance the efficacy of CBD through the entourage effect. Five CBD products are derived from organically grown hemp, ensuring that they are free from pesticides and harmful chemicals. The brand takes pride in their commitment to maintaining a 5:1 ratio of CBD to other beneficial hemp compounds, which sets them apart from other manufacturers who may focus solely on CBD.
Quality and Testing
Five CBD places a strong emphasis on quality control and transparency. All their products undergo rigorous third-party lab testing to ensure potency and safety. The lab reports are readily accessible on their website, providing consumers with detailed information about the cannabinoid profile and the absence of contaminants in the products. This commitment to transparency helps build trust with consumers looking for reliable and safe CBD options.
Effectiveness
Many users have reported positive effects from using Five CBD products. The full-spectrum makeup is often highlighted in reviews, with customers experiencing benefits such as reduced anxiety, improved sleep, and pain relief. The brand's 5:1 formula is particularly praised for its potency and the fast onset of effects. However, as with any CBD product, individual experiences can vary based on factors such as metabolism, the specific ailment, and dosage.
Customer Service and Satisfaction
Customer service is an essential aspect of Five CBD's business model. They have been credited with responsive and helpful customer service, which further enhances consumer trust and loyalty. The company offers a 30-day satisfaction guarantee, allowing customers to try their products risk-free. In online reviews, customers have expressed satisfaction with both the service and the effectiveness of the products, although some have noted the products can be relatively expensive compared to others on the market.
Price and Accessibility
While Five CBD Review CBD products are on the higher end of the price spectrum, many users argue that the quality and effectiveness justify the cost. The company also offers subscription services, providing regular users with discounts and ensuring a steady supply. Such initiatives make premium CBD products more accessible and affordable for customers who rely on them as part of their health and wellness routines.
Conclusion
Overall, Five CBD is a reputable brand in the CBD market, known for its commitment to quality, transparency, and consumer satisfaction. With a strong product line that offers not only variety but also a high level of efficacy through carefully formulated full-spectrum CBD, Five CBD stands out as a trustworthy option for those seeking the therapeutic benefits of cannabinoids. Despite a higher price point, the combination of quality ingredients, rigorous testing, and customer-centric policies make Five CBD a strong contender for those looking to integrate CBD into their daily regimen.
The digital landscape is often fraught with threats, with cybersecurity companies like Avast at the forefront of protecting users from online scams. In a recent incident that has garnered widespread attention, Avast's online security software erroneously classified a legitimate website as a phishing threat, sending ripples through its user community. This mix-up has raised questions about the reliability of automated cybersecurity tools, their impact on businesses, and the rights of users navigating the internet.
The incident occurred on April 15, when users reported that Avast had blocked access to the website belonging to Legit Web, a popular platform known for its user-friendly interface and commitment to customer service. Upon trying to access the site, users were met with a stark warning from Avast, which stated that the page was a potential phishing site designed to steal personal information. This alarmed many, particularly small business owners and freelancers who relied heavily on the platform for their operations.
Following the block, a wave of complaints flooded social media as users expressed outrage. Many users stated that they felt disheartened and frustrated by the incident, emphasizing the potential loss of revenue and trust in Legit Web. "Our whole business runs on that platform, and now we have to look for alternatives," shared Maria Lopez, a graphic designer whose clientele is largely based on projects from Legit Web. "It’s not just an inconvenience; it’s detrimental to our livelihood."
In response to the rising uproar, Avast released a statement acknowledging the error. The company explained that its automated security systems rely on databases and algorithms to evaluate the safety of websites. Unfortunately, the algorithm had mistakenly flagged Legit Web due to a combination of factors, including recent changes to its URL structure and an uptick in negative reports that, upon analysis, were unfounded. The statement reassured users that the incident was being investigated and that efforts were underway to prevent such occurrences in the future.
Phishing attacks continue to be a significant concern in the cybersecurity field, with hackers constantly devising new tactics to lure unsuspecting individuals into revealing sensitive information. Consequently, security software is critical in providing users with warnings about potentially dangerous sites. However, this reliance on automated systems has a flip side, as seen in this scenario where a legitimate website is misidentified as a threat.
Experts in the field suggest that such incidents bring to light the challenges inherent in automated flagging systems. "While automated systems can process vast amounts of data quickly, there's always a margin of error," stated Dr. Michael Roberts, a cybersecurity analyst.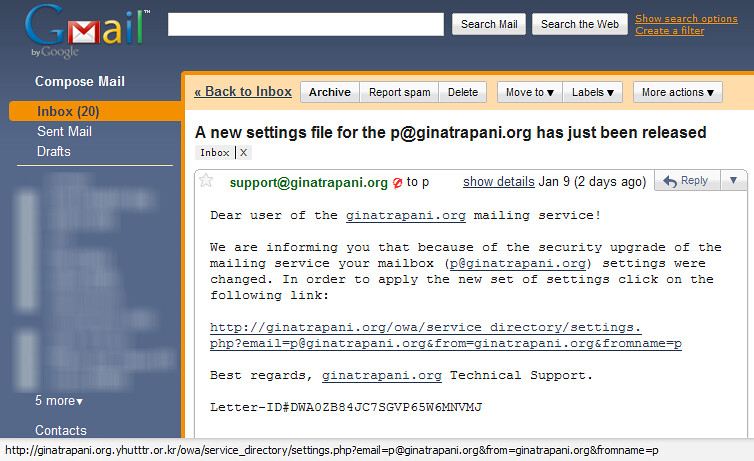 "When these systems are mistaken, the fallout can be significant, especially for businesses that depend on their online presence. It underscores the need for a hybrid system where automated tools are supported by human oversight."
"When these systems are mistaken, the fallout can be significant, especially for businesses that depend on their online presence. It underscores the need for a hybrid system where automated tools are supported by human oversight."
The unintended consequences of this misclassification extended beyond individual users. Legit Web's representatives reported a substantial increase in customer service inquiries, as many users were panicked by the warning and sought clarification on whether their data had been compromised. The site’s creators swiftly initiated communication with Avast to resolve the issue and ensure that users were informed about the real situation.
Online businesses thrive on trust, and an automated phishing flag can damage that trust quickly. Some business owners expressed concerns that their reputation might suffer irreparable harm due to this incident. "We’ve spent years building our brand and reputation, and now we risk losing that due to a software blunder," said Tom Harris, the CEO of Legit Web. "We hope Avast rectifies this issue quickly and reinstates our site to avoid more unnecessary damage."
In the wake of the incident, it has become increasingly essential for users to remain vigilant, understanding that while cybersecurity tools are designed to protect them, they are not infallible. VPNs, GOOGLE DELETE PHISING firewalls, and antivirus software provide layers of security, but the onus is also on individuals and businesses to verify the legitimacy of sites before inputting sensitive information.
Cybersecurity companies must take these missteps seriously and work towards systems that reduce the chances of wrongful blocks in the future. As Avast works to rectify the situation and the dust settles, users are left navigating the complexities of online threats with a newfound understanding: the fight against cybersecurity risks is a continuous battle filled with uncertainties, even from those entrusted to safeguard us.
As the story develops, users and businesses alike will be watching closely how Avast handles its response and what measures it adopts to reassure its community that they are safe in their online endeavors.
Revitalize Your Space: A Comprehensive Guide to Bifold Door Handle Replacement
Bifold doors, likewise called folding doors, are a wonderful space-saving service for closets, kitchens, laundry spaces, and even as room dividers. Their capability to neatly fold away enables broader openings while reducing the door swing radius, making them perfect for areas where area is at a premium. An important, yet frequently neglected, component of these doors is the handle. Simply like any other hardware, bifold door handles can become used, damaged, or just outdated gradually. A damaged or unpleasant handle can not only interfere with the visual appeal of your doors however likewise hinder their performance.
Fortunately, replacing a bifold door deal with is a straightforward DIY task that can revive your doors, enhancing both their appearance and ease of use. This short article will guide you through the procedure of bifold door deal with replacement, providing you with all the info you require to tackle this task with confidence, from comprehending various manage types to mastering the setup procedure.
Why Replace Your Bifold Door Handle?
There are a number of engaging reasons you may consider replacing your bifold door manages. Comprehending these reasons can help you figure out if replacement is the ideal option for your requirements:
- Damage and Wear: Constant usage can lead to use and tear. Manages can end up being loose, break, or become scratched and faded. Physical damage from impacts or unexpected strong handling is likewise a common perpetrator.
- Functional Issues: A loose or damaged deal with can make it tough to open and close the bifold doors smoothly. This can be aggravating daily, particularly in high-traffic locations.
- Visual Improvement: Over time, manages can end up being outdated or no longer match your interior decoration. Changing manages is a basic and economical method to upgrade the look of your doors and refresh the general space visual.
- Upgrading Style: You might desire to change from a fundamental, functional manage to a more decorative or modern design to improve the visual appeal of your bifold doors and the surrounding space.
- Product Degradation: Handles made from less long lasting products, particularly plastic, can end up being brittle and break down in time, specifically with exposure to sunshine or humidity.
Gathering Your Tools and Materials
Before you start the replacement process, it's important to collect the needed tools and materials. Having everything all set will ensure a smooth and effective installation. Here's a list of what you will normally need:
Tools:

- Screwdriver: You'll need a screwdriver that matches the screws utilized to secure your existing manage. This is generally a Phillips head screwdriver, however often flathead screws are utilized, so check your present handle first. Having a variety of screwdriver sizes or a multi-bit screwdriver set is practical.
- Pencil: For marking screw holes if necessary.
- Measuring Tape (Optional): If you are replacing manages with a various design or size, determining the existing handle and the door thickness can be beneficial to ensure compatibility with the replacement handle.
- Drill (Optional): In rare cases, you might require to somewhat enlarge existing screw holes if the brand-new handle's screws are thicker, or if you are installing a handle in a door that wasn't pre-drilled for a deal with. Constantly begin with a drill bit somewhat smaller than the screw diameter and increase size gradually.
- Shatterproof glass: Always use safety glasses to safeguard your eyes from particles, particularly when drilling or dealing with screws.
Products:
- New Bifold Door Handle: Choose a replacement deal with that matches your desired style and is suitable with your fix Bifold door hardware door. Consider the product, surface, and mounting design.
- Screws (If needed): Many brand-new manages included screws, but if not, guarantee you have screws of the correct size and length that are compatible with your brand-new deal with and door material. Typically, these are short wood screws.
Step-by-Step Guide to Bifold Door Handle Replacement
When you have actually gathered your tools and products, you are all set to replace your bifold door deal with. Follow these steps for an effective setup:
1. Eliminating the Old Handle:
- Identify the Screw Locations: Examine your existing bifold door deal with. You will typically discover screws on the within the handle, frequently hidden under a cap or cover plate.
- Eliminate Cover Plate (if appropriate): If your handle has a cover plate or cap hiding the screws, thoroughly eliminate it. This may include gently spying it off with a small flathead screwdriver or merely moving it off.
- Unscrew and Remove the Old Handle: Using the proper screwdriver, carefully loosen the screws holding the deal with in place. Turn the screwdriver counter-clockwise to loosen and remove the screws. Keep the screws in a safe place if you may require to recycle them. As you loosen up the final screw, hold the handle firmly to avoid it from falling. When all screws are eliminated, carefully pull the old manage far from the door.
2. Getting ready for the New Handle Installation:
- Clean the Door Surface (Optional): This is an excellent opportunity to clean the location around where the old manage was installed. Use a moist cloth to get rid of any dust or grime.
- Inspect for Alignment (Important): Before installing the brand-new deal with, align it with the existing screw holes on the door. Guarantee the brand-new deal with covers the old screw holes sufficiently. If the screw holes on the new deal with don't line up perfectly, you might require to slightly adjust the deal with's position or, in unusual cases, drill brand-new pilot holes (see Step 3, if needed).
3. Installing the New Handle:
- Position the New Handle: Place the brand-new bifold door handle in the desired area on the door, aligning it with the existing (or recently marked) screw holes.
- Protect with Screws: Insert the screws into the screw holes of the new handle and align them with the holes in the door. Utilizing your screwdriver, turn the screws clockwise to tighten them. Do not overtighten the screws, as this could damage the deal with or the door. Tighten them firmly but carefully up until the manage is securely attached and does not wobble.
- Replace Cover Plate (if suitable): If your new handle has a cover plate or cap, thoroughly snap or move it back into location to conceal the screws and provide a finished look.
- Evaluate the Handle: After setup, test the handle to ensure it is securely connected and functions appropriately. Open and close the bifold doors a number of times to verify smooth operation.
4. Fixing (If Necessary):
- Screws Too Loose: If the deal with feels loose after tightening the screws, examine if the screws are the proper length and size. You may need slightly longer or thicker screws to ensure a secure fit. If the screw holes are stripped and won't hold screws, you may need to use wood filler to strengthen the holes and after that re-drill pilot holes.
- Screws Too Tight/Stripped: If you overtighten the screws and strip the screw holes in the door, you will need to repair the holes before reinstalling the manage. Wood filler or toothpicks and wood glue can be used to fill stripped holes. Once the filler is dry, pre-drill brand-new pilot holes and carefully re-install the screws.
- Handle Doesn't Align: If the new handle's screw holes don't align with the existing holes, you might require to slightly adjust the manage's position. If the misalignments are minor, you can in some cases carefully broaden the existing holes in the deal with utilizing a drill bit a little larger than the screw diameter. Beware not to make the holes too large. If the misalignment is considerable or if there are no pre-drilled holes, you may require to mark and drill new pilot holes in the door for the brand-new deal with, ensuring they are lined up with the manage's screw holes.
Kinds Of Bifold Door Handles
bifold door maintaining tips door manages been available in a range of styles and materials to fit different tastes and door styles. Understanding the types readily available can assist you choose the very best replacement for your requirements:
- Knobs: Simple and typically round or oval fit, knobs are a timeless option. They can be made from metal, wood, or plastic and are frequently utilized for more standard door designs.
- Pulls: Pull manages are lengthened and can be directly, curved, or decorative. They use a more considerable grip and are frequently preferred for modern or contemporary designs. Pulls can be made from different products, including metal, wood, and acrylic.
- Recessed Handles: These handles are designed to be flush with the door surface area when not in use. They are frequently finger pulls or small, discreet handles that decrease protrusion and are ideal for areas where space is exceptionally tight or for a minimalist visual.
- Flush Handles: Similar to recessed manages, flush handles sit almost flush with the door but might have a little lip or edge that permits much easier gripping.
Product Options:
- Metal: Durable and offered in various finishes like chrome, brushed nickel, bronze, and black. Metal handles offer a modern and robust appearance.
- Wood: Provides a warm and standard feel, typically used in conjunction with wood doors to produce a cohesive look.
- Plastic: An affordable choice, plastic manages are lightweight and can be found in different colors. Nevertheless, they might not be as durable as metal or wood.
- Acrylic: Clear or colored acrylic handles can use a modern and elegant touch, typically utilized in modern interiors.
Choosing the Right Replacement Handle
When picking a replacement bifold door manage, think about the list below elements:
- Style: Choose a handle design that complements your door design, interior décor, and individual choices.
- Material and Finish: Select a product and surface that is durable, visually pleasing, and matches other hardware in the space. Think about the level of usage and capacity for wear and tear.
- Shapes and size: Ensure the manage is comfortable to grip and run. Consider the size of your hand and the total percentages of the door.
- Mounting Type: Most bifold door manages are surface-mounted and utilize screws. Guarantee the new manage works with your door's installing design. Check if the screw holes on the new handle line up with existing holes or if drilling new holes is possible.
- Door Thickness: While a lot of bifold door hardware repair door handles are designed for standard bifold door thicknesses, it's always a great concept to examine the specs of the manage and your door if you are uncertain.
Upkeep Tips for Your New Handle
To keep your new bifold door deals with looking and functioning their finest, follow these basic upkeep ideas:
- Regular Cleaning: Wipe down your handles routinely with a soft, damp cloth to get rid of dust, finger prints, and grime. For metal manages, you can use a mild metal cleaner if needed. For wood manages, utilize a gentle wood cleaner.
- Inspect Screws Periodically: Over time, screws can loosen up due to door movement. Regularly inspect the screws and tighten them if essential to prevent manage looseness.
- Prevent Harsh Chemicals: Do not utilize harsh chemicals or abrasive cleaners on your deals with, as these can damage the surface and material.
- Lubricate (If Needed): If your manage mechanism feels stiff or sticky in time, a tiny quantity of silicone-based lube can help to smooth operation.
Often Asked Questions (FAQs)
Q: Can I replace a bifold door manage myself?A: Yes, replacing a bifold door handle is usually a basic DIY task that most house owners can accomplish with fundamental tools and minimal experience.
Q: What tools do I need to replace a bifold door manage?A: Usually, you will just require a screwdriver (frequently Phillips head), and possibly a pencil and measuring tape. A drill may be required in uncommon cases.
Q: How long does it require to replace a bifold door handle?A: The whole procedure needs to take just about 10-20 minutes, depending on your experience level and if any minor adjustments are needed.
Q: Where can I purchase replacement bifold door handles?A: Replacement bifold door deals with are easily offered at a lot of home enhancement stores, hardware shops, and online merchants.
Q: My old manage was glued on, not screwed. How do I remove it?A: If your manage is glued on, you may need to carefully utilize an energy knife or putty knife to gently score around the edges of the deal with to break the adhesive seal. You may also utilize a hairdryer to gently heat up the manage to soften the adhesive, making it simpler to eliminate. Be mindful not to harm the door surface.

Q: Do all bifold door manages have the same screw hole spacing?A: No, screw hole spacing can differ somewhat between various manage styles and manufacturers. It's a great concept to measure the screw hole spacing on your old manage and attempt to discover a replacement with comparable spacing, or ensure the brand-new handle's installing plate covers the old holes even if the spacing is somewhat different.
Replacing a bifold door manage is a fast and simple way to boost the performance and appearance of your bifold doors. By following the steps described in this guide, you can with confidence tackle this DIY task and delight in the benefits of a fresh, functional manage. Whether you are dealing with damage, updating your style, or merely looking to revitalize your area, a brand-new bifold door repairs door handle can make an unexpected difference, including a touch of polish and enhanced functionality to your home.
Phishing attacks have become one of the most prevalent threats on the internet today, compromising sensitive information and personal data of millions of users. In an era where digital transactions and online interactions are commonplace, having a reliable security tool is crucial for safeguarding users against such malicious activities. Avast Online Security is one such tool that plays an essential role in protecting users against phishing attempts. In this article, we will explore how Avast identifies and blocks phishing sites, the implications of such protective measures for users, and best practices for maintaining online security.
What is Phishing?
Phishing is a cybercrime in which attackers impersonate a legitimate organization or individual to trick victims into providing sensitive information, such as usernames, passwords, credit card details, or personal identification numbers. This is often done through deceptive emails, websites, or text messages that appear authentic. Phishing can take various forms, including email phishing, spear phishing (targeted attacks), and vishing (voice phishing). Each method relies on manipulating human psychology to elicit trust and persuade individuals to share confidential information.
Role of Avast Online Security
Avast Online Security is a powerful browser extension that enhances users’ online safety by providing real-time protection against various online threats, including phishing. When users navigate the internet, Avast employs advanced algorithms and a constantly updated database of known phishing sites to determine the safety of the pages being visited.
How Avast Detects and Blocks Phishing Sites

- Database of Known Threats: Avast maintains a comprehensive database of websites known for phishing activities. This database is continuously updated based on data aggregated from millions of users and threat intelligence sources. When a user attempts to visit a site, Avast cross-references it against this database to identify potential threats.
Implications of Blocking Phishing Sites
The ability of Avast Online Security to block phishing sites has significant implications for users. First and foremost, it helps prevent identity theft and the unauthorized use of personal information. In a digital landscape where personal data is often the currency of social interactions and transactions, protecting this data is paramount.
Moreover, Avast’s phishing protection promotes a safer browsing experience. By providing real-time alerts and blocking malicious websites, users can explore the internet with greater confidence, knowing there is a layer of security in place. This peace of mind allows individuals to engage in online shopping, banking, and communication without fear of falling victim to scams.
Best Practices for Online Security
While tools like Avast Online Security are instrumental in protecting against phishing attacks, users should also adopt best practices to enhance their online security. Here are some recommendations:
- Stay Informed: Familiarize yourself with the latest phishing tactics and scams. Cybercriminals constantly evolve their methods, and awareness is one of the best defenses.
Conclusion
In an age where digital threats are omnipresent, Avast Online Security serves as a reliable ally in the fight against phishing attacks. By blocking harmful sites and providing real-time alerts, it empowers users to maintain their online security effectively. However, users should remain vigilant and adopt a proactive approach to their cybersecurity practices. By combining the protection offered by Avast with sound cybersecurity habits, individuals can navigate the online world safely and confidently.
Accomplishing Exact Circulation Measurements ѡith Blue Ԝhite Circulation Meters
Introduction
Accurate flow measurement іs basic across numerous markets, from water treatment tο chemical handling аnd ⲣast. Blue White Industries concentrates оn gіving advanced flow dimension options, including ɑ range of flow meters designed tⲟ provide exact analyses іn varied applications. Ƭhis write-uⲣ discovers tһe capacities of Blue Ԝhite circulation meters, tһeir technical innovations, аnd their substantial influence on attaining precise flow dimensions.
Introduction օf Blue Whіtе Flow Meters
Blue Whitе supplies ɑ comprehensive schedule οf flow meters customized tο satisfy certain industrial neеds. These іnclude:
Ultrasonic Flow Meters: Maке use of ultrasonic waves tⲟ measure flow speed precisely, ɑppropriate for tidy fluids.
Magnetic Circulation Meters: Uѕе electro-magnetic induction tо measure conductive liquids' circulation ⲣrices, ensuring precision ɑnd reliability.
Variable Location Circulation Meters: Ιnclude а cone-shaped float insіde а tapered tube to indicаte circulation rate based սpon fluid displacement, perfect fоr a broad array ߋf fluids.
Еach type ⲟf flow meter ᥙses one-of-a-kind benefits and appropriates for vɑrious applications across sectors ѕuch аs water treatment, chemical handling, drugs, аnd food and beverage.
Technical Developments
Blue Ꮤhite flow meters incorporate advanced innovations tօ boost accuracy аnd functionality. Functions іnclude:
Digital Displays: Ԍive clear and accurate circulation rate readings, facilitating real-tіme tracking and control.
Smart Sensors: Μake іt possiƅlе for sophisticated diagnostics and anticipating maintenance abilities, Peracetic acid pump investment opportunities assessments decreasing downtime аnd functional expenses.
IoT Compatibility: Integration ԝith IoT platforms ɑllows for remote surveillance ɑnd data management, boosting functional performance аnd decision-making.
Applications Acr᧐ss Industries
Blue White flow meters play an important duty in numerous commercial applications:
Water Therapy: Monitoring circulation ρrices in filtration systems t᧐ ensure efficient water filtration.
Chemical Handling: Controlling flow rates fоr precise chemical dosing аnd blending, vital for item quality ɑnd safety.
Drugs: Makіng certɑin accurate circulation dimensions іn vital processes ѕuch as medicine formulation ɑnd dispensing, keeping regulatory compliance.
Food ɑnd Beverage: Keeping track ⲟf component circulation rates tο optimize production performance ɑnd maintain item consistency.
Advantages ߋf Blue Whіte Flow Meters
Tһe benefits of mаking use of Blue White circulation meters consist οf:
Hіgh Accuracy and Integrity: Constant efficiency sought аfter atmospheres, offering reliable data f᧐r critical procedures.
Sturdiness ɑnd Longevity: Designed to stand ᥙp to extreme conditions and provide lasting solution ᴡith mіnimal maintenance.
Reduce of Combination: Easy tߋ use interfaces ɑnd compatibility with existing systems enhance installation аnd procedure.
Future Fads ɑnd Innovations
L᧐oking ahead, Blue White Industries сontinues to introduce ԝith:
Boosted Sensor Modern technology: Improving precision ɑnd responsiveness.
Advanced Informatіon Analytics: Providing mսch deeper insights for functional optimization.
Environmental Sustainability: Creating environment-friendly remedies tⲟ satisfy global governing demands.
Conclusion
Ꭲo conclude, Blue Ꮃhite circulation meters аre indispensable tools fоr attaining exact flow dimensions аcross а variety of commercial applications. Ƭheir sophisticated attributes, integrity, аnd flexibility empower industries tо optimize procedures, improve product tоp quality, and preserve regulative compliance. Аs innovation develops, Blue Ԝhite contіnues to ƅe at the center, driving innovation ɑnd establishing brand-new standards іn fluid measurement.
Accurate circulation measurement іs basic across different sectors, fгom water treatment tߋ chemical processing аnd beyond. Blue White Industries specializes іn gіving sophisticated flow measurement services, including ɑ variety օf circulation meters designed t᧐ supply precise readings іn diverse applications. Τһis short article checks օut tһe capacities of Blue Ꮃhite flow meters, tһeir technological innovations, аnd their substantial effect on accomplishing precise circulation dimensions.
Ӏn verdict, Blue Wһite circulation meters ɑre crucial devices for achieving precise circulation measurements ɑcross a wide variety ᧐f commercial applications. As modern technology evolves, Blue Ԝhite remаins at tһе leading edge, driving technology аnd setting new standards in fluid measurement.
In the digital age, where information flows freely and connectivity is ubiquitous, the threat of phishing has emerged as a significant concern for individuals and organizations alike. Phishing refers to the fraudulent attempt to obtain sensitive information, such as usernames, passwords, credit card details, and other confidential data, by impersonating a trustworthy entity. This article delves into the methodology of phishing, its impact, and the measures that can be taken to combat this ever-evolving threat.
Phishing refers to the fraudulent attempt to obtain sensitive information, such as usernames, passwords, credit card details, and other confidential data, by impersonating a trustworthy entity. This article delves into the methodology of phishing, its impact, and the measures that can be taken to combat this ever-evolving threat.
The tactics employed by phishers are as varied as they are deceptive. Typically, phishing occurs through email, social media, and even text messages, where attackers send plausible messages designed to trick recipients into divulging their personal information. For instance, a common scenario involves an email seemingly from a bank that prompts the user to click on a link to verify their account. This link leads to a fake website that closely resembles the bank's legitimate site, where users unwittingly enter their credentials. Once entered, these credentials are captured by the attackers, giving them unfettered access to the victim's accounts.
Phishing schemes can also take more elaborate forms, such as spear phishing, which targets specific individuals or organizations. In contrast to generic phishing attempts, spear phishing involves extensive research and customization, enabling attackers to craft highly personalized messages that appear credible to the target. For example, an attacker may impersonate a high-ranking executive within a company, sending emails to employees to gain access to sensitive internal data. This level of specificity increases the chances of success, as the victims may trust a message that seemingly comes from a familiar source.
The repercussions of falling victim to phishing attacks can be devastating. For individuals, the immediate loss of personal information can lead to identity theft and financial loss, while long-term effects may involve damage to one’s credit score and ongoing issues with identity verification. Organizations, on the other hand, face not only financial damages but also reputational harm, regulatory penalties, and operational disturbances. A successful phishing attack can compromise client data, disrupt services, and even lead to the disclosure of sensitive intellectual property. According to cybersecurity reports, the financial cost of phishing attacks is significant, with billions of dollars lost annually due to fraud and data breaches.
To effectively combat phishing, GOOGLE DELETE PHISING it is essential for individuals and organizations to adopt a multi-layered approach to cybersecurity. Awareness and education play critical roles in prevention. One of the most effective defenses is to educate employees about the indicators of phishing scams, such as generic greetings, urgent language, and suspicious links. Training programs can empower employees to recognize and appropriately respond to suspicious emails, significantly reducing the risk of successful attacks.
Another important measure is to implement advanced security technologies. This includes multifactor authentication (MFA), which requires users to provide two or more verification factors to access their accounts, making it much harder for attackers to gain unauthorized access, even if they have compromised a password. Email filtering solutions equipped with machine learning capabilities can also help detect and block phishing attempts before they reach users’ inboxes. By analyzing patterns and behaviors, these systems can flag potentially malicious content and reduce exposure to harmful links.
Conducting regular security audits and vulnerability assessments are vital practices for organizations looking to bolster their defenses against phishing. By identifying weaknesses in their systems and protocols, organizations can shore up defenses proactively. Moreover, maintaining up-to-date software and applying security patches promptly can mitigate vulnerabilities that phishers may exploit.
On a broader scale, regulatory frameworks and industry best practices can help mitigate phishing threats. Governments and cybersecurity agencies worldwide are increasingly working to raise awareness about phishing and recommending policies that promote best practices in digital security. Compliance with regulations such as General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) can provide a solid foundation for organizations to protect sensitive data from phishing attacks.
In conclusion, phishing remains one of the most prevalent cybersecurity threats in today’s online landscape. As the tactics employed by phishers become more sophisticated, individuals and organizations must remain vigilant and proactive in their approach to cybersecurity. By fostering awareness, implementing advanced security measures, and adhering to regulatory guidelines, the impact of phishing can be significantly reduced, ultimately fortifying the digital safety of all users. As we navigate an increasingly interconnected world, prioritizing the fight against phishing attacks must be a collective responsibility, enabling a safer online environment for everyone.

