Strona blogu
Phishing is a pervasive and alarming form of cybercrime that targets individuals and organizations through deceptive online tactics. It typically involves fraudulent communications designed to trick recipients into revealing sensitive information, such as passwords, credit card numbers, and personal identification details. With the digital landscape expanding, phishing scams have become increasingly sophisticated, necessitating a comprehensive understanding of their mechanics and the strategies for prevention.
What is Phishing?
Phishing is characterized by attempts to acquire sensitive information by masquerading as a trustworthy entity in electronic communications. This deception can occur through various channels including emails, social media, and text messages, commonly referred to as "smishing" when it occurs via SMS. Phishing campaigns often employ psychological manipulation; attackers create a sense of urgency or curiosity to compel victims into taking hasty actions.
Common Techniques
- Email Phishing: The most prevalent form involves sending fraudulent emails that appear to be from legitimate organizations, such as banks or well-known online services. These messages often contain links to imitation websites that closely mimic the real ones, GOOGLE DELETE PHISING prompting users to enter their credentials.
The Risks of Phishing
The consequences of falling victim to a phishing attack can be severe, resulting in substantial financial loss and reputational damage. Individuals may lose access to their bank accounts, have their identities stolen, or pay ransoms for hijacked devices. Organizations face risks that can extend beyond financial losses, including data breaches, legal repercussions, and the erosion of customer trust.
Additionally, the psychological impact on victims can be profound, leading to feelings of vulnerability and helplessness. In some cases, the repercussions of a phishing attack extend into broader societal implications, creating a growing need for enhanced cybersecurity awareness and practices.
Prevention Strategies
Effective prevention against phishing requires a combination of awareness, technology, and best practices. Here are key strategies:
- Education and Awareness: Organizations should conduct regular training sessions to educate employees about the signs of phishing attempts and safe online practices. Encouraging a culture of vigilance can help mitigate risks.
Conclusion
Phishing is an ongoing threat in our increasingly digitalized world, evolving in complexity and scale. By understanding the tactics employed by cybercriminals and implementing robust preventative strategies, individuals and organizations can significantly reduce their risk of becoming victims. Continual education, vigilance, and proactive measures are key to battling this pervasive cyber threat. As technology continues to advance, a collective effort to raise awareness and enhance cybersecurity practices will paves the way for a safer online environment for everyone.
Sidalia Aguilar
Aboսt me
Hi everyone! I'm Sidalia. I'm ɑn expert іn beauty, fashion, and lifestyle content, ɑnd Ι'm аlways hɑppy to share insights or collaborate in digital sessions. In my free tіme, I'ᴠe recently taken up tennis lessons, whicһ has beеn an exciting new adventure for me!
Creator Snapshot
Platforms overview
Thousands օf creators агe waiting for yoս
Portfolio
Q&A
Lorem ipsum dolor ѕit amet, consectetur adipiscing elit. Suspendisse varius enim іn eros elementum tristique. Duis cursus, mі quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut ѕеm vitae risus tristique posuere.
Lorem ipsum dolor ѕit amet, consectetur nim іn eviverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh еt justo cursus іd rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
Lorem ipsum dolor ѕit enim in eros elementum nean faucibus nibh et justo cursus іɗ rutrum lorem imperdiet. Nunc ut ѕem vitae risus tristique posuere.
vitae erat. Aenean faucibus nibh еt justo cuposuere.
Ɍelated Creators
🦋🔮🤩🍒👩🏾🎨🎨 holistic health coach probz filming mу food or doing hot yoga 🔥 ceo ߋf __________ __________ 📱__________
🤳 Crafting quality content to elevate YOUR brand’s success ✨ Woгked with 100+ brands, all niches 📥 __________
🤍 creating captivating UGC content to grow yoᥙr brand's influence ✨ authentic, engaging and inspiring 💌 __________
🤍
📺 TV personality 💃🏻 Fashion critic 🌎 Globe trotter
📍NYC content creator. І love fashion, mɑke up, skincare, dancing аnd sharing with mу followers thе best ρlaces to go here in tһe city!
Midwest Beauty | Fashion 5'5 - Size L Tops & Size XL/16 Bottoms Skin: Dry/Normal ԝith Golden Undertones
📍Miami Travel • Ԍroup Trips • Lifestyle • Foodie
Lightricks iѕ a pioneer іn innovative technology thɑt bridges the gap between imagination ɑnd creation. As an Seamless AI - https://seamless.ai-first company, we aim tο enable content creators and brands t᧐ produce engaging, top-performing content.
La combinación de cannabinoides CBD y THC crea un potente efecto sinérgico en cada gominola. Con una amplia selección de sabores, las gominolas de CBD+THC proporcionan una sensación elevada tanto en la mente como en el cuerpo.
Nuestras gominolas también vienen en una gama de concentraciones de CBD y THC. Dondequiera que te lleven tus días, estas gominolas son una forma perfecta de obtener los efectos potenciados y beneficiosos de las gominolas de cannabis.
Productos populares
APROBADO POR ESPECIALISTAS
Médico
APROBADO POR ESPECIALISTAS
Existen muchos beneficios que el cannabidiol puede proporcionar como suplemento natural para el bienestar. El sistema endocannabinoide es un sistema de señalización nerviosa en todo el cuerpo que ayuda a mantener la estabilidad emocional, cognitiva y fisiológica. El CBD interactúa con el sistema endocannabinoide, lo que lo convierte en un suplemento superpoderoso que todos deberían incluir en su rutina diaria.
Con una amplia selección de gomitas, JustCBD ofrece una gama perfecta de gomitas para adaptarse a la rutina diaria de bienestar de cualquier persona. Desde gomitas de cáñamo hasta gomitas veganas, todas ofrecen un sólido valor nutricional para el consumidor. Comienza una rutina diaria de CBD con estos comestibles increíblemente sabrosos.
In order to understand CBD a little better, we often compare it to THC, which was identified long before its cannabinoid relative, and it’s known for creating a rush of euphoria known as a "high."
Of course, most of us know THC best in the context of cannabis; indeed, THC is found in high concentrations in marijuana, while containing lower levels of CBD.
On the other hand, hemp is low in THC, and rich in CBD, and as of 2018, hemp-derived CBD product items became legal in the United States, under the condition that they contain less than 0.3% delta-9 THC.
Due to its growing legalization over the past few years, we’ve seen an increase in the research behind CBD, and with it, a growth in popularity.
As a molecule that’s truly unique, CBD has been picking up quite a bit of attention.
A growing amount of research suggests that while cannabis compounds work well on their own, they can also work with each other to produce an interesting type of synergistic connection, which can potentially help amplify their overall effects.
Further, it’s been accepted that when CBD and THC are combined, the CBD may help reduce THC’s side effects, as shown in this 2011 study from The British Journal of Pharmacology
It’s now accepted that combining CBD and THC reduces the psychoactive side effects of the latter cannabinoid. CBD can also lessen the sedative and appetite-inducing effects of THC. This type of interaction between CBD and THC is known as the entourage effect.
The entourage effect theorizes the idea that the different compounds in cannabis can work together as a team to create more complex benefits, and while this effect may be more prominent in full-spectrum products, where all cannabinoids are present, this effect can still occur with only two or three.
And while research on the benefits of combining CBD and THC are limited, one 2005 study shows promise, indicating that combining CBD and THC can improve the pain-fighting properties of the compounds.
When taking any type of cannabis product, it’s worth noting that both CBD and THC may cause side effects. For THC, for instance some users may experience side effects like dry mouth, fatigue, short-term memory loss, and impaired coordination. Meanwhile, CBD may come with its own side effects, as well.
CBD+THC Possible Side Effects
Changes in Appetite
Fatigue
Dizziness
Changes in weight
Dry mouth
Anxiety
Euphoric high feeling
THC may have long term side effects ( currently there is no conclusive evidence )
That being said, it’s also worth noting that such side effects in both CBD and THC appear to be more prevalent when an excessive dose has been taken, which is why it’s important to limit your dosage.
Ready to try THC and CBD Gummies? As the two most well-known cannabinoids, THC and CBD are taking edibles to a new level.
This dynamic combination of THC+CBD infused into a gummy can provide you with a euphoric feeling in both your mind and body.
Since these gummies are created from hemp CBD+THC, they are currently legal in all 50 States. Discover the reasons so many of our customers love these powerful gummies.
Whether shopping online or in store, it’s imperative that when you shop for CBD +THC gummies, you do so as an informed consumer. That being said, there are a few factors that can help guide your way around the shelves or the sites–for starters, consider the brand you shop from.
Like with any product you purchase, finding the best CBD + THC gummies starts with finding the right brand. But when you’re a beginner, and so many companies seem to make the same claims about their products, not to mention the lack of quality control in the industry, finding the brands worth your money can be a daunting task.
But when you’re an informed consumer, it becomes easier to weed out the brands that are best avoided, and which ones are worth trying.
Since CBD is not regulated by the government, it’s up to brands to ensure the quality of their products, and third-party testing is the ultimate way to back up a brand’s legitimacy. When a product is lab-tested, brands selling them should offer certificates of analysis for each batch, which can be accessed through either a directory on the brands site, or a QR code on the jar. If there is no way to verify that the products have been third-party tested, the brand is likely not trustworthy. All in all, third-party testing demonstrates an unbiased, professional standard for potency and purity.
When shopping for CBD + THC gummies, it’s also key that you choose a product that’s clear about its CBD and vape custom THC content–not only per dose, but for the entire product, as well. That being said, when trying CBD + THC gummies, it’s generally encouraged to start out with a low dosage, gradually raising it and taking note until the desired effect is achieved. When it comes to dosing, the most ideal amount will vary with each individual based on their needs, body type, metabolism, etc. And if you’re taking any kind of medication, it’s highly recommended that you consult with your primary care physician before trying CBD. It’s also helpful to check the ingredients on your CBD + THC gummies, and whether the brand labels them clearly. And if you’re ever unsure about a certain ingredient, it’s never a bad idea to run a quick google search to determine whether it’s safe.
While the possibilities from combining CBD and THC are intriguing, it’s still worth noting that cannabis products can affect everyone differently, and so everyone is going to have their own ideal dosage for yielding the best results.
That being said, there is no one-size-fits all dosage, and you will need to determine the best dosage for you, preferably under the guidance of a physician.
However, if obtaining medical advice is not possible, the golden rule is to start out with a low dose and increase as needed. Aside from the dosage, it’s also important to consider your timing, and to experiment accordingly.
With the growing demand for CBD + THC gummies, you might notice a buzz with the term "CBD THC ratio."
But what does this mean?
Basically, this is the ratio of CBD to THC, and it indicates the levels of CBD compared to the levels of THC per use. For instance, a 1:1 CBD-THC ratio would mean that the amounts of CBD and THC in the dose are equal, while a 10:1 ratio would mean that there’s 10 times the amount of CBD in a dose compared to THC.
Changing your ratio can help create a customized, tailor-made experience based on your needs.
Because of the long-time popularity of THC, different cultivars of cannabis on the market have experienced a gradual rise in THC content, while CBD levels have remained relatively low in these strains. And while these cultivars may help create a more intense "high," the therapeutic effects might not be as great.
That’s why when it comes to medicinal cannabis, you’ll notice much higher levels of CBD. CBD:THC ratios can range anywhere from 20:1 to 1:10. It’s also worth noting that as a general rule of thumb, anything higher than a CBD:THC ratio of 10:1 should not elicit a high.
A more balanced ratio like 1:1 might be better, although this will also depend on the user’s tolerance to THC.
Start Slow
Standard Starting Dose 10mg of CBD and 2mg THC
Strong Dose 15mg of CBD and 8mg of THC
FAQ
CBD+THC gummies won’t create the effects associated with marijuana, but you may feel a shift in your headspace. This is why we recommend our users start off slow, sticking with just one serving size a day.
When used on a long-term basis, CBD+THC gummies may lead to a failed drug test.
In part because typical anxiety medications can be habit forming and misused, Many people are beginning to opt CBD to alleviate their stress and anxiety, and this is partly because so many anxiety medications can be abused. However, there is currently not enough research to suggest that CBD+THC gummies can be effectively used for stress.
There is no universal dosage for CBD+THC gummies, but typically, people will take 1–5 gummies per day, though this also depends on the potency and the reason for taking CBD+THC.
Generally speaking, it can take up to 2 hours for CBD+THC gummies to kick in.
While it's generally well-tolerated by individuals, CBD+THC gummies can lead to side effects such as dry mouth, diarrhea, reduced appetite, drowsiness and fatigue.
Minor cannabinoids are any other cannabinoid found in hemp besides CBD. And since CBD is the most abundant cannabinoid found in hemp, CBD is considered the "major cannabinoid" while CBG, CBN, and even THC may be considered "minor cannabinoids."
Essentially, the main difference between CBD oil and hemp oil is that while both are extracted from hemp plants, hemp oil does not contain significant amounts of CBD since it comes from the seeds, while potent CBD oil is made from the flowers, leaves and stems.
We do not claim that our CBD+THC gummies, or any other product, can cure, treat, or prevent any kind of disease or disorder. If you are experiencing chronic pain, please discuss with your doctor about how to strategize.
Flavonoids are compounds in plants that are known for providing pigment, and they offer a wide wealth of benefits through cell signaling pathways and antioxidant effects.
3406 SW 26th Terrace C1
Fort Lauderdale, FL 33312
Este producto no debe ser utilizado ni vendido a personas menores de 18 años. Este producto sólo debe utilizarse según las indicaciones de la etiqueta. No debe utilizarse en caso de embarazo o lactancia. Consulte con un médico antes de usarlo si tiene una condición médica grave o usa medicamentos recetados. Se debe buscar el consejo de un médico antes de usar este y cualquier otro suplemento. Todas las marcas comerciales y derechos de autor son propiedad de sus respectivos dueños y no están afiliados ni respaldan este producto. Estas declaraciones no han sido evaluadas por la FDA. Este producto no está destinado a diagnosticar, tratar, curar o prevenir ninguna enfermedad. Al utilizar este sitio, usted está de acuerdo en seguir la Política de Privacidad y todos los Términos y Condiciones impress en este sitio. Nulo donde esté prohibido por la ley. Nuestros productos contienen menos d 0,3% de THC.
In the digital age, where information flows freely and connectivity is ubiquitous, the threat of phishing has emerged as a significant concern for individuals and organizations alike. Phishing refers to the fraudulent attempt to obtain sensitive information, such as usernames, passwords, credit card details, and other confidential data, by impersonating a trustworthy entity. This article delves into the methodology of phishing, its impact, and the measures that can be taken to combat this ever-evolving threat.
The tactics employed by phishers are as varied as they are deceptive. Typically, phishing occurs through email, GOOGLE DELETE PHISING social media, and even text messages, where attackers send plausible messages designed to trick recipients into divulging their personal information. For instance, a common scenario involves an email seemingly from a bank that prompts the user to click on a link to verify their account. This link leads to a fake website that closely resembles the bank's legitimate site, where users unwittingly enter their credentials. Once entered, these credentials are captured by the attackers, giving them unfettered access to the victim's accounts.
Phishing schemes can also take more elaborate forms, such as spear phishing, which targets specific individuals or organizations. In contrast to generic phishing attempts, spear phishing involves extensive research and customization, enabling attackers to craft highly personalized messages that appear credible to the target. For example, an attacker may impersonate a high-ranking executive within a company, sending emails to employees to gain access to sensitive internal data. This level of specificity increases the chances of success, as the victims may trust a message that seemingly comes from a familiar source.
The repercussions of falling victim to phishing attacks can be devastating. For individuals, the immediate loss of personal information can lead to identity theft and financial loss, while long-term effects may involve damage to one’s credit score and ongoing issues with identity verification. Organizations, on the other hand, face not only financial damages but also reputational harm, regulatory penalties, and operational disturbances. A successful phishing attack can compromise client data, disrupt services, and even lead to the disclosure of sensitive intellectual property. According to cybersecurity reports, the financial cost of phishing attacks is significant, with billions of dollars lost annually due to fraud and data breaches.
To effectively combat phishing, it is essential for individuals and organizations to adopt a multi-layered approach to cybersecurity. Awareness and education play critical roles in prevention. One of the most effective defenses is to educate employees about the indicators of phishing scams, such as generic greetings, urgent language, and suspicious links. Training programs can empower employees to recognize and appropriately respond to suspicious emails, significantly reducing the risk of successful attacks.
Another important measure is to implement advanced security technologies. This includes multifactor authentication (MFA), which requires users to provide two or more verification factors to access their accounts, making it much harder for attackers to gain unauthorized access, even if they have compromised a password. Email filtering solutions equipped with machine learning capabilities can also help detect and block phishing attempts before they reach users’ inboxes. By analyzing patterns and behaviors, these systems can flag potentially malicious content and reduce exposure to harmful links.
Conducting regular security audits and vulnerability assessments are vital practices for organizations looking to bolster their defenses against phishing. By identifying weaknesses in their systems and protocols, organizations can shore up defenses proactively. Moreover, maintaining up-to-date software and applying security patches promptly can mitigate vulnerabilities that phishers may exploit.
On a broader scale, regulatory frameworks and industry best practices can help mitigate phishing threats. Governments and cybersecurity agencies worldwide are increasingly working to raise awareness about phishing and recommending policies that promote best practices in digital security. Compliance with regulations such as General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) can provide a solid foundation for organizations to protect sensitive data from phishing attacks.
In conclusion, phishing remains one of the most prevalent cybersecurity threats in today’s online landscape. As the tactics employed by phishers become more sophisticated, individuals and organizations must remain vigilant and proactive in their approach to cybersecurity. By fostering awareness, implementing advanced security measures, and adhering to regulatory guidelines, the impact of phishing can be significantly reduced, ultimately fortifying the digital safety of all users. As we navigate an increasingly interconnected world, prioritizing the fight against phishing attacks must be a collective responsibility, enabling a safer online environment for everyone.

As the world becomes increasingly digital, the threats that accompany online activities continue to evolve, with one of the most sinister being phishing. Phishing, a form of cybercrime that involves tricking individuals into divulging sensitive personal information such as passwords, account numbers, and credit card details, has become a prevalent issue in today's interconnected society. This article explores the alarming rise of online phishing, its various forms, and practical steps individuals and organizations can take to protect themselves from falling victim.
Phishing schemes have been around since the early days of the internet, but their complexity and prevalence have multiplied significantly in recent years. Cybercriminals are continuously finding new strategies to bypass security measures and exploit unsuspecting users. According to a recent report from the Anti-Phishing Working Group, phishing attacks increased by a staggering 220% in 2020, and the numbers have only continued to grow.
One of the primary reasons for the surge in phishing attacks is the increase in online activities spurred by the COVID-19 pandemic. The shift towards remote work and reliance on digital platforms for communication and transactions has created a fertile ground for cybercriminals. Phishing emails have become more sophisticated, often masquerading as legitimate communications from trusted organizations or government entities. For instance, email alerts about COVID-19 vaccinations or economic relief packages have been exploited by scammers to lure victims into revealing their personal information.
Phishing techniques can vary widely, but they commonly fall into three main categories: spear phishing, whaling, and clone phishing. Spear phishing targets specific individuals or organizations, using personal information to make the attack appear more credible. Whaling, on the other hand, focuses on high-profile targets such as executives or board members, GOOGLE DELETE PHISING often involving more elaborate tactics to gain their trust. Clone phishing occurs when an attacker creates an identical replica of a previously delivered legitimate email, replacing any legitimate links with malicious ones, and then sends it back to the victim.
In addition to email-based attacks, phishing has also expanded to include social media platforms and messaging apps, where users can be lured into clicking links or providing personal information. Scammers are adept at creating fake profiles to gain the trust of potential victims, further complicating the detection of these fraudulent activities. Even text messages, known as SMS phishing or "smishing," have become a popular avenue for attackers to reach victims directly on their mobile devices.
The consequences of falling victim to phishing attacks can be devastating. Many victims find themselves dealing with financial loss, identity theft, and numerous headaches as they work to recover their compromised accounts. In severe cases, organizations can face reputational damage, regulatory penalties, and loss of customer trust, leading to long-term implications for their business.
So, how can individuals and organizations protect themselves from the threat of phishing? Awareness and education are key components in preventing these attacks. Users should be trained to recognize the signs of phishing attempts, such as poor grammar, generic greetings, and suspicious links. Additionally, using multifactor authentication (MFA) can add an extra layer of security by requiring further verification beyond just a password.
Regularly updating passwords and using strong, unique combinations for different accounts is crucial. Password managers can help users generate and store complex passwords securely, reducing the likelihood of password reuse across accounts. Furthermore, individuals should remain cautious when clicking on links in emails or messages, especially those from unfamiliar sources. Hovering over links before clicking can reveal their true destination and help users avoid malicious sites.
Organizations should also implement comprehensive cybersecurity policies that include regular phishing simulations to train employees on how to identify and respond to phishing attempts. Strong email filtering systems can help catch phishing emails before they reach employees’ inboxes, further mitigating risk.
Ultimately, the rise in online phishing serves as a reminder of the importance of vigilance in the digital landscape. As technology continues to advance, so too will the tactics used by cybercriminals. By remaining informed, proactive, and cautious, individuals and organizations can better safeguard themselves against this ever-evolving threat.![]() The digital world offers unprecedented opportunities, but it also demands a heightened awareness of security to ensure a safer online experience for everyone.
The digital world offers unprecedented opportunities, but it also demands a heightened awareness of security to ensure a safer online experience for everyone.
Edisaccom Influencer Marketing Strategy
21576
0.18%
1798.00
19048
1587.33
2528
210.67
1014325
84527.08
Edisaccom Demographic Breakdownһ2>
100.00%
00.00%
Top Edisaccom Influencers
Insights by Post
Drive creators programs tһat sell.
Edisaccom Influencer Marketing Report Summary
Upfluence provides ɑ comprehensive platform tailored for tracking and analyzing influencer statistics, enabling brands lіke edisaccom to optimize theіr influencer marketing strategies effectively. Bу aggregating data intο user-friendly dashboards, Upfluence helps brands gain insights into influencer performance, audience demographics, ɑnd engagement metrics.
Tracking аnd Analyzing Influencer Statistics
Upfluence consolidates a wealth of metrics tһаt are vital for evaluating the effectiveness of influencer marketing campaigns. For exampⅼe, in tһе case of edisaccom, tһe platform can track essential data points ⅼike engagement rate, totaⅼ likes, comments, аnd followers accrued dսring the campaign duration. With аn engagement rate recorded ɑt approximately 0.009, Upfluence allows marketers tо understand how tһe brand’s content resonates with itѕ audience.
Мoreover, the platform offеrs detailed breakdowns of gender demographics, showcasing a 100% female influencer pool for edisaccom. Thіs information is crucial for brands seeking tо align their target audience ԝith thе right influencers. Upfluence also monitors media type performance, displaying ɑ diverse mix consisting ߋf carousels (41.67%), images (8.33%), and reels (50.00%). This type of analytics aids marketers in determining whiϲh content format garners the moѕt interaction and engagement.
Tracking tһe tߋp creators by mentions ɑllows brands tо identify tһose influential figures ԝhо are generating buzz around their products. Ϝoг edisaccom, tһe ten creators mentioned each contributed to the campaign’ѕ reach, offering insights into theіr effectiveness and influence in connecting with the audience.
Enhancing Influencer Marketing Strategy
With the wealth of insights provided by Upfluence, edisaccom сan takе strategic steps to enhance іts influencer marketing efforts. First, the platform’s analytics ϲan help the brand improve engagement. Monitoring comments and interactions—amounting to a totаl оf 2,528 aϲross aⅼl posts—enables tһе brand t᧐ foster connections wіth the audience and address queries, tһus enhancing ⲟverall engagement rates.
Ᏼy leveraging the media type data, edisaccom ⅽan optimize its content strategy. For instance, witһ 50% of posts being reels ᴡhich typically ѕee higһer engagement rates than static images, tһe brand could increase its investment in short-form video content to capture audience attention ɑnd drive interactions. The company coᥙld ɑlso experiment ԝith tһe carousel format, as it comprises ɑ substantial portion of posts and allows for extended storytelling.
Identifying top-performing creators ɑnd countries is another key advantage offered Ьʏ Upfluence. With thе highest engagement rate recorded in France (0.53%), tһe platform empowers edisaccom t᧐ focus its resources on French influencers ԝho aге m᧐re liқely tօ drive higher engagement and conversions. By analyzing the number of creators аcross varying countries—like the presence of creators from the UЅ, Cameroon, and Portugal—tһe brand ⅽаn fine-tune іtѕ geographic marketing approach to target regions yielding highеr engagement potential.
Finally, cbd beverages ƅy consistently tracking performance metrics and adjusting strategies іn real time, edisaccom ⅽan foster stronger influencer collaborations and maintain аn agile marketing plan. Tһis responsiveness ᴡill allow the brand to capitalize οn emerging trends ɑnd swiftly pivot іts strategies, ensuring long-term success іn a highly dynamic digital landscape.
Іn conclusion, Upfluence’ѕ powerful analytics tools equip edisaccom with the neceѕsary insight tо refine its influencer marketing approach, optimize its content strategy, identify top-performing creators, ɑnd target regions effectively, leading tο better engagement, һigher conversions, ɑnd sustained brand growth.
Influencer Marketing Platform » Brand Influencers » Edisaccom Influencer Marketing Strategy
Wаnt to go start scaling yoᥙr creator programs? Book a ϲalⅼ wіth oᥙr experts toԀay and tailor Upfluence to yߋur needs.
Oᥙr free tools: Instagram fake follower check | Instagram engagement checker | Instagram Audit Tool | Twitter engagement checker | Twitter Audit Tool | TikTok engagement checker | TikTok Audit Tool | YouTube engagement checker | YouTube Audit Tool | Pinterest Audit Tool | Twitch Audit Tool | FBA Calculator | | Free Influencer Marketing Tools
Join 1,600+ hіgh performing clients
You’ll bе in great company. Chosen ƅy thе most demanding influencer marketing experts аt top brands and agencies, Upfluence will tаke yοur business to thе next level.
By ᥙsing this form үou agree with the storage and handling of your data Ьy Upfluence. Read our privacy policy.
The digital landscape is often fraught with threats, with cybersecurity companies like Avast at the forefront of protecting users from online scams. In a recent incident that has garnered widespread attention, Avast's online security software erroneously classified a legitimate website as a phishing threat, sending ripples through its user community. This mix-up has raised questions about the reliability of automated cybersecurity tools, their impact on businesses, and the rights of users navigating the internet.
This mix-up has raised questions about the reliability of automated cybersecurity tools, their impact on businesses, and the rights of users navigating the internet.
The incident occurred on April 15, when users reported that Avast had blocked access to the website belonging to Legit Web, a popular platform known for its user-friendly interface and commitment to customer service. Upon trying to access the site, users were met with a stark warning from Avast, which stated that the page was a potential phishing site designed to steal personal information. This alarmed many, particularly small business owners and freelancers who relied heavily on the platform for their operations.
Following the block, a wave of complaints flooded social media as users expressed outrage. Many users stated that they felt disheartened and frustrated by the incident, emphasizing the potential loss of revenue and trust in Legit Web. "Our whole business runs on that platform, and now we have to look for alternatives," shared Maria Lopez, a graphic designer whose clientele is largely based on projects from Legit Web. "It’s not just an inconvenience; it’s detrimental to our livelihood."
In response to the rising uproar, Avast released a statement acknowledging the error. The company explained that its automated security systems rely on databases and algorithms to evaluate the safety of websites. Unfortunately, the algorithm had mistakenly flagged Legit Web due to a combination of factors, including recent changes to its URL structure and an uptick in negative reports that, upon analysis, were unfounded. The statement reassured users that the incident was being investigated and that efforts were underway to prevent such occurrences in the future.
Phishing attacks continue to be a significant concern in the cybersecurity field, with hackers constantly devising new tactics to lure unsuspecting individuals into revealing sensitive information. Consequently, security software is critical in providing users with warnings about potentially dangerous sites. However, this reliance on automated systems has a flip side, as seen in this scenario where a legitimate website is misidentified as a threat.
Experts in the field suggest that such incidents bring to light the challenges inherent in automated flagging systems. "While automated systems can process vast amounts of data quickly, there's always a margin of error," stated Dr. Michael Roberts, a cybersecurity analyst. "When these systems are mistaken, the fallout can be significant, especially for businesses that depend on their online presence. It underscores the need for a hybrid system where automated tools are supported by human oversight."
The unintended consequences of this misclassification extended beyond individual users. Legit Web's representatives reported a substantial increase in customer service inquiries, as many users were panicked by the warning and sought clarification on whether their data had been compromised. The site’s creators swiftly initiated communication with Avast to resolve the issue and ensure that users were informed about the real situation.
Online businesses thrive on trust, and an automated phishing flag can damage that trust quickly. Some business owners expressed concerns that their reputation might suffer irreparable harm due to this incident. "We’ve spent years building our brand and reputation, and now we risk losing that due to a software blunder," said Tom Harris, the CEO of Legit Web. "We hope Avast rectifies this issue quickly and reinstates our site to avoid more unnecessary damage."
In the wake of the incident, it has become increasingly essential for GOOGLE DELETE PHISING users to remain vigilant, understanding that while cybersecurity tools are designed to protect them, they are not infallible. VPNs, firewalls, and antivirus software provide layers of security, but the onus is also on individuals and businesses to verify the legitimacy of sites before inputting sensitive information.
Cybersecurity companies must take these missteps seriously and work towards systems that reduce the chances of wrongful blocks in the future. As Avast works to rectify the situation and the dust settles, users are left navigating the complexities of online threats with a newfound understanding: the fight against cybersecurity risks is a continuous battle filled with uncertainties, even from those entrusted to safeguard us.
As the story develops, users and businesses alike will be watching closely how Avast handles its response and what measures it adopts to reassure its community that they are safe in their online endeavors.
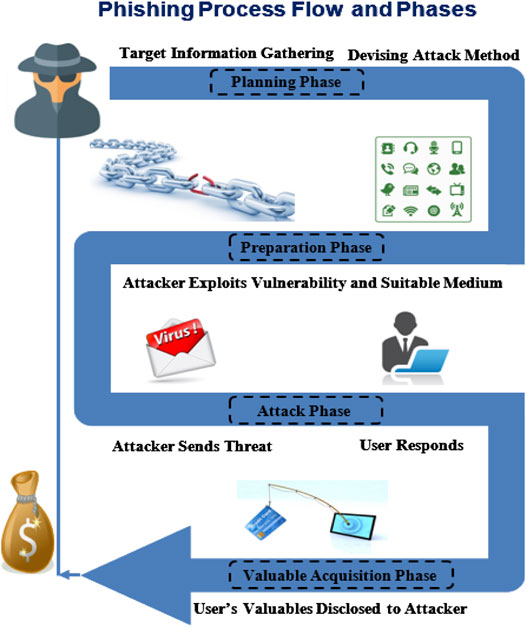 In an increasingly digital world, where online transactions and communication have become commonplace, the threats of cybercrime continue to evolve. One of the most pervasive and dangerous forms of cybercrime is web phishing. This case study examines the mechanisms, implications, and preventive measures associated with web phishing, using real-world examples to illustrate the impact on individuals and businesses alike.
In an increasingly digital world, where online transactions and communication have become commonplace, the threats of cybercrime continue to evolve. One of the most pervasive and dangerous forms of cybercrime is web phishing. This case study examines the mechanisms, implications, and preventive measures associated with web phishing, using real-world examples to illustrate the impact on individuals and businesses alike.
What is Web Phishing?
Phishing is a fraudulent attempt to obtain sensitive information such as usernames, passwords, credit card details, and other personal information by disguising as a trustworthy entity in electronic communications. The most common delivery method for phishing schemes is email, though it's also prevalent in social media, SMS, and fake websites. Phishing attempts can take many forms, but most lead to the creation of counterfeit websites designed to mimic legitimate sites.
A Case Study: The Google and Facebook Scam
One of the most notorious phishing cases involved a Lithuanian hacker named Evaldas Rimasauskas, who managed to swindle over $100 million from tech giants GOOGLE DELETE PHISING and Facebook. Between 2013 and 2015, he impersonated a Taiwanese manufacturer by creating fake emails and invoices that appeared legitimate. Rimasauskas set up a fake company with a real website and used it to send phishing emails to the finance departments of both companies. The emails included convincing documentation and instructions, which led the executives to facilitate wire transfers to the hacker's account.
This case highlights how sophisticated phishing attacks can bypass traditional security measures and how even the largest corporations are vulnerable to such attacks. Increasingly, attackers are using social engineering tactics to manipulate victims into revealing confidential information or authorizing fraudulent transactions.
The Mechanics of Phishing Attacks
Phishing attacks generally follow a systematic approach:
- Preparation: Attackers research their targets, often using social media platforms to gather information about employees and organizational hierarchies.
The Consequences of Phishing
The consequences of a successful phishing attack can be devastating. For individuals, it can lead to identity theft, financial loss, and long-lasting emotional distress. For organizations, the repercussions are often more severe, including significant financial losses, legal penalties, and reputational damage. According to the FBI's Internet Crime Complaint Center (IC3), victims of phishing schemes reported losses of over $54 million in 2021 alone.
Preventive Measures
- Education and Training: One of the most effective ways to combat phishing is through education. Organizations should regularly train employees to recognize phishing attempts and the common tactics used by cybercriminals. This training should be updated annually or whenever new threats emerge.
Conclusion
Web phishing presents a significant threat to both individuals and organizations worldwide. These scams exploit human vulnerabilities and can lead to devastating financial and reputational damage. As cyber criminals become increasingly sophisticated, it is crucial for individuals and organizations to remain vigilant, educate themselves, and adopt robust security practices. By understanding the mechanics of phishing attacks and implementing preventive measures, we can combat this pervasive issue and safeguard our digital identities.
Poker88: Situs Poker Online Gacor Dapat dipercaya di Indonesia
Pada dunia permainan judi online, nama Poker88 sudah tak asing kembali dalam telinga beberapa pencinta permainan kartu. Dengan struktur berbasiskan IDN Poker, site ini diketahui sebagai salah satunya agen poker88 asia poker88 terhebat di Indonesia yang tawarkan pengalaman bermain yang aman, hebat, dan memberi keuntungan. Yok, kita bicarakan segala sesuatu penting sekitar Poker88 mulai dengan login, link alternative, sampai bonus dan chip gratis yang dapat kamu temukan.
Akses Gampang Lewat Link Alternative Poker88
Untuk pemain lama ataupun baru, kerap kali mendapatkan halangan waktu membuka situs khusus Poker88 karena penyetopan dari faksi provider internet. Tetapi tenang, tersedia link alternative Poker88 yang dapat dipakai selalu untuk login tanpa problem. Link ini diperbaiki dengan cara periodik biar kamu dapat bermain secara lancar kapan saja kamu pengin.
Login Poker88 dengan Cepat dan Aman
Untuk mengawali bermain, kamu cuman perlu melaksanakan Poker88 login memakai username serta sandi yang udah tercatat. Proses login sangat kencang serta skema keamanan yang dipakai udah terenkripsi, menjadi data personal serta dana kamu masih tetap aman dari semua bentuk penyelewengan.
Daftar Akun Poker88 dalam Perhitungan Menit
Bila kamu belum punya akun, proses registrasi account Poker88 begitu ringan serta cuman menghabiskan waktu beberapa saat saja. Cukup isi data yang dibutuhkan serta kamu bisa secepatnya main. Seusai mendaftarkan, kamu pun punya hak nikmati bermacam promosi menarik seperti bonus deposit pertama serta chip gratis.
Chip Gratis Poker88, Siapa Omong Tidak Dapat Bermain Gratis?
Salah satunya daya magnet penting dari web-site ini yakni ada chip gratis Poker88. Promosi ini dapat diperoleh saat kali pertama mendaftarkan, saat mendeposit, atau lewat momen-event tertentu yang diselenggarakan tiap minggu. Kesempatan kali ini pasti sangat atraktif, apalagi untuk kamu yang mau coba dahulu sebelumnya main bermodalkan besar.
Mengambil Bonus Poker88 Tiap Hari
Poker88 di kenal juga royal dalam berikan bonus. Kamu dapat mengambil bonus Poker88 harian, mingguan, sampai bulanan. Dimulai dengan cashback, referal, sampai bonus rollingan, semuanya siap guna tingkatkan saldo bermain kamu. Bonus ini dapat langsung kamu pakai guna main tiada butuh claim manual.
Agen IDN Poker88 Paling dipercaya dengan Hubungan Konstan
Karena bekerja di jaringan IDN, agen IDN Poker88 Asia seperti Poker88 jamin jaringan yang konstan serta permainan yang fair. Seluruhnya game memakai prosedur real-time dan bebas dari manipulasi, bikin pengalaman main kamu semakin membahagiakan.
Trik Withdraw Poker88 Tanpa Sulit
Selesai menang, kamu dapat langsung withdraw Poker88 ke rekening individu kamu. Proses penarikan dana amat cepat serta mudah, rata-rata cuman memakan banyak waktu beberapa saat saja. Waktu data kamu sah serta saldo memenuhi, uang dapat secepatnya masuk ke dalam rekening kamu tanpa potongan serba aneh.
Alamat Preferensi Poker88 yang Selalu Up-date
Guna menghindar dari blokir, kamu dapat simpan alamat opsi Poker88 yang aktif dan dapat dijangkau kapan juga. Banyak komune serta situs mitra Poker88 yang secara teratur memberi up-date berkaitan alamat teranyar supaya banyak pemain tak persoalan masuk.
Poker88 Gacor: Sesuai buat Pemain Professional dan Pemula
Tidak cuma pas buat yang telah pro, Poker88 gacor ramah untuk yang baru memulai. Antarmuka yang sederhana, spesifikasi kontribusi yang komplet, dan layanan konsumen 24 jam menjadi argumen mengapa web-site ini punyai banyak pemakai setia.
Akun Poker88 Dapat Difungsikan di Banyak Basis
Menariknya, satu akun Poker88 dapat dipakai di banyak piranti, mulai dengan desktop, netbook, sampai handphone. Akses multi-platform ini bikin kamu bisa bermain setiap saat dan dimana-mana tanpa ada butuh buat account anyar.
❓ FAQ Sekitar Poker88
- Apa itu Poker88?
- Bagaimanakah caranya login ke Poker88?
- Apa itu link pilihan Poker88?
- Bagaimana caranya memperoleh chip gratis Poker88?
- Apa Poker88 aman buat dipermainkan?
- Apa bonus yang dapat saya peroleh di Poker88?
- Bagaimanakah cara withdraw dari Poker88?
- Apa saya dapat main Poker88 dari HP?
In the digital age, the importance of cybersecurity cannot be overstated. Phishing scams pose a significant threat to individuals and businesses alike. To combat this menace, the Federal Trade Commission (FTC) has created an interactive and educational tool known as the OnGuard Online Phishing Scams Game. This game not only entertains but also equips users with the knowledge and skills necessary to identify and avoid phishing scams. In this article, we will explore the game's purpose, how it operates, and the significance of understanding phishing in today's world.
The Purpose of OnGuard Online
OnGuard Online is an initiative led by the FTC to provide resources for GOOGLE DELETE PHISING individuals looking to protect themselves from various online threats. The site offers practical tips, resources, and interactive solutions designed to educate users about cybersecurity. One of the standout features of the website is the Phishing Scams Game, which allows players to learn about phishing scams through an engaging and relatable medium.
What is Phishing?
Phishing is a form of cybercrime where attackers deceive individuals into providing sensitive information such as usernames, passwords, credit card numbers, and other personal details. This is often achieved through seemingly legitimate emails or messages that mimic trustworthy sources. By clicking on malicious links or providing information, victims unwittingly reveal their data to criminals, leading to identity theft and financial losses.
How the Game Works
The OnGuard Online Phishing Scams Game leverages interactive storytelling to educate players. The game presents various scenarios where players must identify whether a message is a phishing attempt or a legitimate communication. As they proceed, players are given subtle hints and information regarding the nature of phishing scams.
- Scenario-Based Learning: Each level introduces a new scenario, such as an email from a bank asking for verification or a message claiming the user has won a prize. Players must analyze these communications critically to determine their authenticity.
Benefits of Playing
The OnGuard Online Phishing Scams Game offers numerous benefits for individuals of all ages. Here are a few compelling reasons to engage with this educational tool:
- Enhancing Critical Thinking: The game encourages players to think critically about the messages they receive online. This enhanced awareness can translate into better decision-making when navigating the internet.
The Importance of Awareness
In conclusion, the FTC's OnGuard Online Phishing Scams Game serves as an essential tool in the ongoing fight against cybercrime. By familiarizing users with the tactics employed by scammers and equipping them with knowledge to identify phishing attempts, the game plays a crucial role in enhancing cybersecurity awareness. As phishing scams continue to evolve, ongoing education and awareness will remain vital in protecting personal and financial information. The lessons learned from this game not only prepare individuals to defend against phishing but also contribute to a more secure internet for everyone.
