Strona blogu
The digital landscape is often fraught with threats, with cybersecurity companies like Avast at the forefront of protecting users from online scams. In a recent incident that has garnered widespread attention, Avast's online security software erroneously classified a legitimate website as a phishing threat, sending ripples through its user community. This mix-up has raised questions about the reliability of automated cybersecurity tools, their impact on businesses, and the rights of users navigating the internet.
The incident occurred on April 15, when users reported that Avast had blocked access to the website belonging to Legit Web, a popular platform known for its user-friendly interface and commitment to customer service. Upon trying to access the site, users were met with a stark warning from Avast, which stated that the page was a potential phishing site designed to steal personal information. This alarmed many, particularly small business owners and freelancers who relied heavily on the platform for their operations.
Following the block, a wave of complaints flooded social media as users expressed outrage. Many users stated that they felt disheartened and frustrated by the incident, emphasizing the potential loss of revenue and trust in Legit Web. "Our whole business runs on that platform, and now we have to look for alternatives," shared Maria Lopez, a graphic designer whose clientele is largely based on projects from Legit Web. "It’s not just an inconvenience; it’s detrimental to our livelihood."
In response to the rising uproar, Avast released a statement acknowledging the error. The company explained that its automated security systems rely on databases and algorithms to evaluate the safety of websites. Unfortunately, GOOGLE DELETE PHISING the algorithm had mistakenly flagged Legit Web due to a combination of factors, including recent changes to its URL structure and an uptick in negative reports that, upon analysis, were unfounded. The statement reassured users that the incident was being investigated and that efforts were underway to prevent such occurrences in the future.
Phishing attacks continue to be a significant concern in the cybersecurity field, with hackers constantly devising new tactics to lure unsuspecting individuals into revealing sensitive information. Consequently, security software is critical in providing users with warnings about potentially dangerous sites. However, this reliance on automated systems has a flip side, as seen in this scenario where a legitimate website is misidentified as a threat.
Experts in the field suggest that such incidents bring to light the challenges inherent in automated flagging systems. "While automated systems can process vast amounts of data quickly, there's always a margin of error," stated Dr. Michael Roberts, a cybersecurity analyst. "When these systems are mistaken, the fallout can be significant, especially for businesses that depend on their online presence. It underscores the need for a hybrid system where automated tools are supported by human oversight."
The unintended consequences of this misclassification extended beyond individual users. Legit Web's representatives reported a substantial increase in customer service inquiries, as many users were panicked by the warning and sought clarification on whether their data had been compromised. The site’s creators swiftly initiated communication with Avast to resolve the issue and ensure that users were informed about the real situation.
Online businesses thrive on trust, and an automated phishing flag can damage that trust quickly. Some business owners expressed concerns that their reputation might suffer irreparable harm due to this incident. "We’ve spent years building our brand and reputation, and now we risk losing that due to a software blunder," said Tom Harris, the CEO of Legit Web. "We hope Avast rectifies this issue quickly and reinstates our site to avoid more unnecessary damage."
In the wake of the incident, it has become increasingly essential for users to remain vigilant, understanding that while cybersecurity tools are designed to protect them, they are not infallible. VPNs, firewalls, and antivirus software provide layers of security, but the onus is also on individuals and businesses to verify the legitimacy of sites before inputting sensitive information.
Cybersecurity companies must take these missteps seriously and work towards systems that reduce the chances of wrongful blocks in the future. As Avast works to rectify the situation and the dust settles, users are left navigating the complexities of online threats with a newfound understanding: the fight against cybersecurity risks is a continuous battle filled with uncertainties, even from those entrusted to safeguard us.
As the story develops, users and businesses alike will be watching closely how Avast handles its response and what measures it adopts to reassure its community that they are safe in their online endeavors.
In Holocene epoch years, CBD (cannabidiol) products wealthy person gained vast popularity for their possible alterative benefits and rude feeler to wellness. Among the 10000 of CBD brands emergent just about the world, Vanatera CBD has turn a topic of matter to among consumers quest choice and effectualness. This article delves into Vanatera CBD, examines drug user reviews, and provides insights into what makes this trade name stand prohibited in the crowded CBD marketplace.
Intellect CBD:
Before diving into Vanatera CBD reviews, it's important to make a canonical agreement of what CBD is. CBD is a by nature occurring heighten launch in the cannabis plant, which has been ill-used for thousands of old age for medicative purposes. Unequal THC (tetrahydrocannabinol), another well-known cannabinoid, CBD does non bring about the psychoactive effects that are commonly associated with marijuana habit. This deficiency of a high, united with its potential wellness benefits, has contributed to CBD's growth popularity.
Insertion to Vanatera CBD:
Vanatera CBD is a relatively raw fledgeling to the CBD market, merely it has chop-chop gained care for its commitment to tone and introduction. The make offers a browse of CBD products, including oils, capsules, and topicals, which are configured to cope with divers consumer inevitably. Vanatera emphasizes transparence in its yield process, ensuring that entirely their products are made with organically adult halter and are subject field to tight third-party testing to substantiate their pureness and effectiveness.
Prize and Transparency:
Ane of the primal marketing points of Vanatera CBD is its dedication to select and transparence. In an industry where regularization can buoy vary greatly, having a honest and trusty denounce is of the essence for consumers. Vanatera CBD stands away by providing elaborate data just about the sourcing of their hemp, the origin processes they use, and the taxonomic group benefits of apiece production. In addition, wholly lab results are readily uncommitted to customers, allowing them to swear the petit mal epilepsy of injurious pesticides, impenetrable metals, Buy Vanatera CBD and early contaminants.
Roam of Products:
Vanatera CBD offers an impressive kind of products to ply to unlike preferences and requirements. Their cartesian product melodic line includes:
- CBD Oils: Usable in versatile concentrations, these oils arse be interpreted sublingually or added to nutrient and beverages. They are studied to ply a pliant dosing choice for individuals quest sculptural relief from anxiety, inflammation, or chronic painfulness.
- CBD Capsules: For those World Health Organization opt a Sir Thomas More ready to hand and pre-deliberate option, Vanatera's CBD capsules provide a aboveboard path to merged CBD into a day-after-day mundane.
- Topicals: These admit creams and balms studied for targeted ease. Infused with extra ingredients same all-important oils, these topicals fundament be applied straight to the clamber for localized discourse of afflictive muscles or hide conditions.
- Gummies and Edibles: An gratifying and tasty way of life to waste CBD, these products are specially democratic among those WHO disfavour the innate gustation of CBD oil.
Customer Reviews and Feedback:
A critical prospect of intellect whatsoever merchandise is examining customer reviews. Vanatera CBD has standard numerous reviews from users WHO commend the blade for its efficacy and caliber. Many customers account confident experiences with the products, noting benefits such as reduced anxiety, improved sleep quality, and assuagement from chronic bother. The customer table service provided by Vanatera is besides oftentimes praised, highlighting their responsiveness and professionalism.
However, as with whatever product, not whole reviews are nemine contradicente overconfident. More or less users rich person shared out that they ground the effects to be milder than potential or that they favored former brands. It's significant to think of that individual experiences with CBD toilet diverge greatly owed to differences in body chemistry, the distressfulness of the wellness specify beingness treated, and the dose victimized.
Last and Considerations:
Vanatera CBD appears to be a promising choice for those exploring the public of cannabidiol for health and health purposes. Its allegiance to transparency, quality, and customer atonement has earned it a favourable lay within the industriousness. Prospective customers should face at Vanatera's comp intersection range of mountains and aboveboard research lab testing to facilitate informed decisions regarding their CBD choices.
It's essential to confer with a healthcare provider ahead starting whatsoever Modern appurtenance routine, especially if you are pregnant, nursing, or consume implicit in health conditions. Piece reviews toilet put up insight, they should not put back checkup advice bespoken to your taxonomic group wellness inevitably.
In summary, Vanatera CBD presents a compelling select for those seeking high-timber and sure CBD products. With its dedication to excellence and customer care, it continues to pull individuals great to draw rein the potential benefits of CBD as depart of a fitter lifestyle.
Whether you're a veteran CBD user or a newcomer looking at to strain it for the showtime time, Vanatera CBD is a stain meriting considering in your travel towards lifelike wellness.
As the world becomes increasingly digital, the threats that accompany online activities continue to evolve, with one of the most sinister being phishing. Phishing, a form of cybercrime that involves tricking individuals into divulging sensitive personal information such as passwords, account numbers, and credit card details, has become a prevalent issue in today's interconnected society. This article explores the alarming rise of online phishing, its various forms, and practical steps individuals and organizations can take to protect themselves from falling victim.
Phishing schemes have been around since the early days of the internet, but their complexity and prevalence have multiplied significantly in recent years. Cybercriminals are continuously finding new strategies to bypass security measures and exploit unsuspecting users. According to a recent report from the Anti-Phishing Working Group, phishing attacks increased by a staggering 220% in 2020, and the numbers have only continued to grow.
One of the primary reasons for the surge in phishing attacks is the increase in online activities spurred by the COVID-19 pandemic. The shift towards remote work and reliance on digital platforms for communication and transactions has created a fertile ground for cybercriminals. Phishing emails have become more sophisticated, often masquerading as legitimate communications from trusted organizations or government entities. For instance, email alerts about COVID-19 vaccinations or economic relief packages have been exploited by scammers to lure victims into revealing their personal information.
Phishing techniques can vary widely, but they commonly fall into three main categories: spear phishing, whaling, and clone phishing. Spear phishing targets specific individuals or organizations, using personal information to make the attack appear more credible. Whaling, on the other hand, focuses on high-profile targets such as executives or board members, often involving more elaborate tactics to gain their trust. Clone phishing occurs when an attacker creates an identical replica of a previously delivered legitimate email, replacing any legitimate links with malicious ones, and then sends it back to the victim.
In addition to email-based attacks, phishing has also expanded to include social media platforms and messaging apps, where users can be lured into clicking links or providing personal information. Scammers are adept at creating fake profiles to gain the trust of potential victims, further complicating the detection of these fraudulent activities. Even text messages, known as SMS phishing or "smishing," have become a popular avenue for attackers to reach victims directly on their mobile devices.
The consequences of falling victim to phishing attacks can be devastating. Many victims find themselves dealing with financial loss, identity theft, and GOOGLE DELETE PHISING numerous headaches as they work to recover their compromised accounts. In severe cases, organizations can face reputational damage, regulatory penalties, and loss of customer trust, leading to long-term implications for their business.
So, how can individuals and organizations protect themselves from the threat of phishing? Awareness and education are key components in preventing these attacks. Users should be trained to recognize the signs of phishing attempts, such as poor grammar, generic greetings, and suspicious links. Additionally, using multifactor authentication (MFA) can add an extra layer of security by requiring further verification beyond just a password.
Regularly updating passwords and using strong, unique combinations for different accounts is crucial. Password managers can help users generate and store complex passwords securely, reducing the likelihood of password reuse across accounts. Furthermore, individuals should remain cautious when clicking on links in emails or messages, especially those from unfamiliar sources. Hovering over links before clicking can reveal their true destination and help users avoid malicious sites.
Organizations should also implement comprehensive cybersecurity policies that include regular phishing simulations to train employees on how to identify and respond to phishing attempts. Strong email filtering systems can help catch phishing emails before they reach employees’ inboxes, further mitigating risk.
Ultimately, the rise in online phishing serves as a reminder of the importance of vigilance in the digital landscape. As technology continues to advance, so too will the tactics used by cybercriminals. By remaining informed, proactive, and cautious, individuals and organizations can better safeguard themselves against this ever-evolving threat. The digital world offers unprecedented opportunities, but it also demands a heightened awareness of security to ensure a safer online experience for everyone.
Navigating Bi-Fold Door Repair: A Comprehensive Guide
Bi-fold doors are a popular option for lots of homeowners due to their space-saving design and aesthetic appeal. However, like any other home component, they can come across issues that need repair. Whether it's a sticking door, broken rollers, or a misaligned track, understanding how to attend to these problems can conserve you time and money. This thorough guide will stroll you through the procedure of finding and performing bi-fold door repair near you, ensuring your doors operate efficiently and look their best.
Comprehending Bi-Fold Doors
Before diving into the repair procedure, it's vital to comprehend the parts of a bi-fold door. Bi-fold doors consist of numerous panels that fold together, allowing them to move along a track. The primary parts include:
- Panels: These are the specific areas of the bifold door repair tutorials that fold and slide.
- Track: The horizontal or vertical path along which the panels move.
- Rollers: Small wheels connected to the top and bottom of each panel, allowing them to slide smoothly.
- Hinges: Connect the panels to each other and to the frame.
- Deals with: Used to open and close the doors.
- Adjustment Screws: Allow for tweak the alignment of the panels.
Common Issues and DIY Fixes
Sticking Doors
- Cause: Dust, dirt, or particles in the track can trigger the doors to stick.
- Option: Clean the track with a vacuum or a soft brush. Use a silicone lube to the rollers to make sure smooth movement.
Misaligned Panels
- Trigger: Over time, the panels can end up being misaligned due to wear and tear or incorrect installation.
- Option: Adjust the positioning screws situated at the top and bottom of the panels. Turn the screws clockwise to raise the panel and counterclockwise to reduce it.
Broken Rollers
- Cause: Rollers can wear or break, causing the doors to jam or not slide at all.
- Solution: Replace the broken rollers with brand-new ones. Ensure the brand-new rollers are the very same size and type as the old ones.
Loose Hinges
- Trigger: Hinges can become loose with time, causing unsteady panels.
- Option: Tighten the hinge screws. If the screws are removed, use longer screws or fill the holes with wood filler before reinserting the screws.
Damaged Panels
- Cause: Panels can end up being harmed due to impact or wear.
- Service: For minor damage, you can utilize wood filler or touch-up paint. For significant damage, think about replacing the whole panel.
When to Call a Professional
While numerous bi-fold door concerns can be attended to with DIY options, some problems may need the expertise of a professional. Here are some signs that it's time to call a specialist:
- Complex Repairs: If the concern involves changing several elements or if the bifold door refurbishment is severely harmed.
- Security Concerns: If the door is not functioning effectively and postures a safety risk.
- Service warranty Issues: If the door is under guarantee, a specialist can ensure that the repair is done properly and the guarantee remains valid.
Discovering a Bi-Fold Door Repair Service
Regional Listings
- Online Search: Use search engines to discover bi-fold bifold door renovators repair services in your location. Try to find evaluations and rankings to guarantee you select a credible company.
- Yellow Pages: Check regional business directories for listings of bifold door adjustment repair services.
Referrals

- Pals and Family: Ask your family and friends if they have had similar issues and if they can advise a reliable repair service.
- Community Groups: Join local community groups on social media platforms to request for suggestions.
Professional Associations
- Home Improvement Associations: Look for companies that are members of expert associations such as the National Association of the Remodeling Industry (NARI) or the Better Business Bureau (BBB).
What to Expect from a Professional Repair Service
When you employ a professional to repair your bi-fold doors, you can expect the following:
- Initial Assessment: The professional will inspect the door to recognize the issues and supply a comprehensive quote of the repair expenses.
- Repair Execution: They will carry out the essential repairs, making sure that all components are functioning correctly.
- Quality Assurance: A trusted service will stand behind their work and provide a service warranty on the repairs.
- Customer Service: They ought to offer clear interaction throughout the process and be offered to answer any questions you may have.
FAQs
Q: How much does bi-fold weatherproof bifold door repairs repair expense?A: The expense of bi-fold door repair can vary depending upon the degree of the damage and the components that require to be replaced. Basic repairs, such as cleaning the track or changing the positioning, may cost around ₤ 50 to ₤ 100. More complex repairs, such as changing rollers or panels, can vary from ₤ 100 to ₤ 300 or more.
Q: Can I repair a bi-fold door myself?A: Many small problems can be addressed with DIY services, such as cleaning the track or adjusting the alignment. Nevertheless, for more intricate repairs, it's finest to speak with a professional to ensure the task is done properly and safely.
Q: How long does bi-fold door repair take?A: Simple repairs can be completed in a couple of hours, while more complex repairs may take a full day or longer. The period will depend upon the level of the damage and the accessibility of replacement parts.
Q: What should I look for in a bi-fold door repair service?A: Look for a service that has experience with bi-fold doors, favorable reviews from previous customers, and a clear communication procedure. Ensure they use a warranty on their work and are licensed and guaranteed.
Q: Can I prevent bi-fold door issues?A: Regular maintenance can help avoid numerous typical issues. Clean the track and rollers frequently, lubricate the moving parts, and inspect the alignment regularly. Resolve any small issues immediately to prevent them from ending up being more major.
Bi-fold doors are a valuable addition to any home, but they require occasional maintenance and repair to function optimally. By understanding the typical concerns and understanding how to address them, you can keep your bi-fold doors in excellent condition. When DIY solutions aren't enough, do not be reluctant to call a professional to ensure the task is done right. With the right care and attention, your bi-fold doors will continue to boost your home for years to come.
The CBD industry has experienced exponential growth in recent years, with a multitude of products hitting the market. While some products may promise the world, Five CBD Reviews the quality and efficacy of CBD ingredients can vary greatly. In this report, we will examine Five CBD Ingredients key CBD ingredients that are commonly used in modern CBD products. These ingredients are: CBD isolate, full-spectrum CBD, broad-spectrum CBD, terpenes, and phytocannabinoids.
1. CBD Isolate
CBD isolate is a highly concentrated, pure form of CBD that has been isolated from the other compounds in the cannabis plant. This ingredient is made by solvents, such as ethanol or methanol, which strip away the other cannabinoids and terpenes, leaving only CBD. While CBD isolate is a popular choice for those looking for a potent, non-psychoactive CBD product, it often lacks the beneficial effects of other cannabinoids and terpenes, and may be less effective for treating specific health conditions.
2. Full-Spectrum CBD
Full-spectrum CBD, also known as whole-plant CBD, is made from the entire cannabis plant, including the flowers, leaves, and stems. This ingredient contains a mix of cannabinoids, including CBD, THC, and other minor cannabinoids, as well as terpenes and other plant compounds. Full-spectrum CBD is often considered the most effective form of CBD for treating specific health conditions, due to the entourage effect, which refers to the synergistic relationship between the various compounds in the cannabis plant.
3. Broad-Spectrum CBD
Broad-spectrum CBD is similar to full-spectrum CBD in that it is made from the entire cannabis plant. However, unlike full-spectrum CBD, broad-spectrum CBD has been processed to remove the THC. This ingredient still contains a mix of cannabinoids and terpenes, but without the psychoactive effects of THC. Broad-spectrum CBD is often a good choice for those who want to avoid THC but still reap the benefits of other cannabinoids and terpenes.
4. Terpenes
Terpenes are a class of compounds found in the cannabis plant, responsible for the plant's unique aromas and flavors. There are over 100 different terpenes, each with its own unique properties and effects. Some common terpenes found in CBD products include myrcene, limonene, and linalool. Terpenes may have therapeutic benefits, such as reducing inflammation and improving mood.
5. Phytocannabinoids
Phytocannabinoids are a group of compounds found in the cannabis plant, which interact with the human body's endocannabinoid system (ECS). Some common phytocannabinoids include CBG, CBC, and CBDV. These compounds may have therapeutic effects, such as reducing pain and inflammation, and improving mood. However, more research is needed to fully understand the effects of phytocannabinoids.
In conclusion, the Five CBD ingredients discussed in this report are some of the most common and effective ingredients used in modern CBD products. CBD isolate provides a potent, non-psychoactive experience, while full-spectrum CBD offers a synergistic blend of cannabinoids and terpenes. Broad-spectrum CBD offers a balance between potency and regulatory compliance. Terpenes and phytocannabinoids may have additional therapeutic benefits, but more research is needed to fully understand their effects. By understanding the potential benefits and limitations of these ingredients, consumers can make informed decisions when selecting a CBD product.

The Folding Electric Mobility Scooter: A Comprehensive Guide
As the world ages and metropolitan landscapes grow significantly congested, the demand for efficient, portable, and sustainable modes of transport is more noticable than ever. Among the myriad of ingenious options offered, the folding electric mobility scooter stands apart as a useful option for individuals with mobility problems and metropolitan commuters alike. This article offers an extensive take a look at the folding electric mobility scooter, covering its features, advantages, and considerations for use.
What is a Folding Electric Mobility Scooter?
A folding electric mobility scooter is a compact, battery-powered lorry designed to help people with mobility challenges in moving more quickly. Unlike conventional scooters, these models are developed to be quickly folded, permitting them to be carried in vehicles, stored in little spaces, or travel mobility scooter brought into public transportation.
Key Features of Folding Electric Mobility Scooters
Lightweight Design: Manufactured with lightweight products, folding scooters can generally weigh between 50 to 70 pounds, making them easy to use for elders and those with limited upper body strength.

Compact folding mobility scooter Mechanism: Most designs include an instinctive folding system, allowing users to collapse the scooter with very little effort, with some models even folding immediately with the push of a button.
Battery Efficiency: The scooters come equipped with lithium-ion or lead-acid batteries, supplying a series of 10 to 25 miles on a single charge, depending upon the design.
Adjustable Features: Many folding scooters offer adjustable seats, handlebars, and footrests to accommodate different body types and boost the rider's convenience.
Security Features: Common safety features include anti-tip wheels, LED headlights, and a steady base to prevent accidents throughout operation.
Speed Control: Most scooters are equipped with variable speed controls, allowing users to control their speed according to their convenience and the terrain.
Benefits of Using a Folding Electric Mobility Scooter
The benefits of folding electric mobility scooters extend beyond their physical qualities. Here are some of the essential benefits:
Enhanced Mobility: These scooters make it possible for individuals with mobility challenges to regain their self-reliance and move freely, granting them access to shopping mall, parks, and social engagements.
Minimized Physical Strain: With electric power helping motion, users can navigate their environments without putting in excessive effort, thus minimizing fatigue.
Convenience of Transport: The foldable feature makes it easy to take these scooters in cars, buses, or trains, allowing users to combine different modes of transport flawlessly.
Affordable Transportation: Compared to automobile ownership and maintenance, a mobility scooter can substantially minimize transport expenses for brief distances.
Eco-friendly: Electric scooters produce no emissions and run on electrical energy, making them a sustainable option to gas-powered automobiles.
Factors to consider When Choosing a Folding Electric Mobility Scooter
When selecting a folding electric mobility scooter, prospective purchasers should think about the following aspects:
Weight Capacity: Understanding the optimum weight capability is important to guarantee the scooter can support the person's weight.
Battery Life: Evaluate the battery range and charging time to guarantee it meets your day-to-day travel needs.
Speed and Performance: Different models provide varying speeds; select one that fits your activity level and where you'll be using it most regularly.
Surface Compatibility: Consider whether the scooter is created for smooth pavement or rough terrains if you plan to travel outdoors.
Warranty and Support: Look for scooters that feature a guarantee and reputable client assistance for upkeep.
Contrast Table of Popular Folding Electric Mobility Scooters
| Scooter Model | Weight (pounds) | Weight Capacity (pounds) | Max Range (miles) | Max Speed (mph) | Price Range |
|---|---|---|---|---|---|
| Pride Go-Go Folding Scooter | 60 | 300 | 15 | 4.5 | ₤ 1,300 - ₤ 1,500 |
| EV Rider Transport AF+: Lightweight Folding Mobility Scooter Rider Transport AF+ | 53 | 250 | 10 - 15 | 4.0 | ₤ 1,100 - ₤ 1,400 |
| Drive Medical Scout | 66 | 300 | 15 | 4.25 | ₤ 1,200 - ₤ 1,600 |
| Solax Genie | 50 | 220 | 12 | 4.0 | ₤ 900 - ₤ 1,200 |
| Change Vision | 55 | 300 | 25 | 5.0 | ₤ 1,500 - ₤ 2,000 |
Often Asked Questions (FAQs)
1. Are folding electric mobility scooters easy to operate?
Yes, most folding electric mobility scooters are designed to be user-friendly, featuring user-friendly controls and comfortable seating for ease of usage.
2. How far can a folding electric mobility scooter travel on a single charge?
Depending upon the model, the range can vary in between 10 to 25 miles on a complete charge. Constantly examine the requirements for the specific scooter you have an interest in.
3. The length of time does it take to charge a folding electric mobility scooter?
Charging time differs by design, but generally, it can take anywhere from 4 to 8 hours for a full charge.
4. Can I use a folding electric mobility scooter outdoors?
Numerous folding electric mobility scooters are created for both indoor and outside usage. Nevertheless, users must examine the requirements to make sure surface compatibility.
5. What is the average lifespan of a folding electric mobility scooter?
With correct care and upkeep, a folding electric mobility scooter can last anywhere from 3 to 5 years.
Folding electric mobility scooters are valuable properties for individuals looking for enhanced mobility and independence. Their mobility, ease of use, and sustainable operation make them an ideal option for both city travelling and leisurely travel. As the market develops, these scooters will continue to provide boosted functions while making sure comfort and security for users. For anybody thinking about investing in a mobility scooter, exploring the different models and their special requirements is vital for making a notified and acceptable choice.
In today’s digital age, online shopping has become increasingly popular, allowing consumers to buy goods and services from the comfort of their homes. However, with the rise of e-commerce, there have also been increasing instances of phishing scams, particularly targeting prominent retailers like Walmart. This case study examines how individuals and organizations can effectively stop or respond to phishing attempts masquerading as Walmart-related communications.
Understanding Phishing Scams
Phishing is a form of cybercrime where attackers impersonate legitimate organizations to deceive individuals into revealing sensitive information, such as usernames, passwords, credit card numbers, and other personal data. Phishing scams typically arrive via email, SMS, or malicious websites that closely resemble legitimate company sites. Walmart, as one of the largest retailers in the world, frequently falls victim to these scams, prompting many consumers to experience the potential dangers associated with online shopping.
Case Study Background
In early 2023, a series of phishing attempts involving Walmart began to spread, alarming customers and raising awareness about the need for cybersecurity. The scammers targeted consumers by sending emails that appeared to come from Walmart, often informing them of non-existent shipping issues, missed deliveries, or the need to confirm account details urgently.
The First Line of Defense: Educating Consumers
Education plays a pivotal role in combating phishing attempts. In response to escalating scams, Walmart initiated a consumer awareness campaign to educate its customers on how to identify suspicious emails and messages. This campaign included:
- Use of Visual Guidelines: Walmart provided visual aids showcasing the common traits of phishing emails, such as poor grammar, unfamiliar sender addresses, and the presence of urgent requests that create a sense of fear or anxiety.
Implementing Technical Safeguards
In addition to consumer education, Walmart took steps to implement technical safeguards designed to protect customers from phishing scams:
- Email Filtering Systems: Walmart upgraded its email filtering systems to reduce the likelihood of phishing attempts reaching customers' inboxes. By employing advanced filtering algorithms and machine learning techniques, the company increased the detection of fraudulent emails.
Lessons Learned
The response to phishing scams directed at Walmart uncovered several key lessons about cybersecurity:
- Proactive Education is Vital: Continuous education campaigns must be implemented, targeting both consumers and employees. Awareness is the first and most effective line of defense against phishing attacks.
Conclusion
As online shopping continues to grow, so does the risk of phishing scams. Through a combination of consumer education, technical safeguards, and proactive responses, Walmart has taken significant steps to protect its customers from these insidious threats. While phishing attempts cannot be entirely eliminated, effective measures can diminish their impact and equip consumers with the knowledge and tools to protect themselves in an increasingly digital marketplace. By staying informed and vigilant, both organizations and consumers can help create a safer online shopping environment.
Over 40 years of expert care
Best UK Group & 5 star reviews
Established Clinics
Ⲟver 40 years of expert care
Best UK Ꮐroup & 5 star reviews
Nationwide Clinics
Breast Reduction – 074ΑR-R – Front
Scars wіll continue tߋ fade ovеr tіme.
Ꮢelated Beforе & Ꭺfter Images
Ɍelated Blogs & News
Ready tо Ƅegin your journey?
Cⲟme and sеe оur expert surgeons tо discuss the best options available for ʏou. Book a consultation and take that firѕt step.
Talk tߋ an expert 0203 3256555
Vieԝ our privacy policy
Аbout Tһe Private Clinic
The Private Clinic is a multi award winning medical group ѡith clinics located acгoss the UK. We һave over 40 years’ experience in offering the best in advanced minimally invasive non surgical treatments and expert led surgical procedures in ouг clinics and hospitals. Our surgeons are all registered ѡith the GMC (General Medical Council) and we are regulated by the Care Quality Commission (CQC). The CQC іs an independent regulator for health and social care in England. Last review March 10th 2023.
Information
Useful Links
Sign Up for Lаtest News & Offers
View ⲟur privacy policy
Company reɡ: The Private Clinic iѕ a trading name of TPC Ꮐroup Limited (company registration numƅer 14493595) © 2025 The Private Clinic.
TPC Groᥙp Limited trading ɑs The Private Clinic Harley Street London, ᴡhich іѕ аn Appointed Representative of Chrysalis Finance Limited. TPC Group Limited іs ɑ credit broker, not ɑ lender. Chrysalis Finance Limited іs authorised and regulated by the Financial Conduct Authority f᧐r credit broking аnd Hi Seltzer Deltа 8, Https://Littleforay.Com, lending.
In today's digital age, phishing scams have morphed into one of the most pervasive threats to online safety, particularly for young internet users. To combat this escalating issue, the Federal Trade Commission (FTC) has introduced an innovative educational game called "On Guard Online," which is specifically designed to teach children and adolescents how to recognize and avoid phishing scams. This game stands out as a noteworthy advancement in the realm of digital education, harnessing interactive learning to foster real-world skills in internet safety.
Phishing, the malicious practice of tricking individuals into revealing sensitive information such as usernames, passwords, and credit card numbers, has evolved in complexity and sophistication. Scammers employ a variety of tactics, from seemingly harmless emails to fake websites that closely mimic legitimate services. The FTC’s On Guard Online game takes a proactive approach to equip young users with the knowledge and skills they need to identify and respond to such threats.
The foundational premise of the game is built on engaging young users through an interactive online platform. Players navigate scenarios that replicate real-life phishing attempts, including emails that tempt users with fraudulent offers and social engineering tactics in online interactions. The immersive experience of the game allows players to recognize red flags associated with phishing schemes, such as poor grammar, unusual sender addresses, or urgent calls to action. By engaging with these scenarios, players learn to apply critical thinking and analytical skills to evaluate the legitimacy of online communications.
One significant advance in On Guard Online is its integration of gamification elements that enhance user engagement while promoting retention of information. The game's design includes various levels and challenges, rewarding players for successfully identifying and reporting phishing attempts. These gamified elements not only make learning enjoyable but also reinforce essential concepts of cybersecurity in a manner that resonates with the gaming preferences of younger audiences. As players progress through higher levels, they encounter increasingly complex phishing scenarios that push them to hone their skills further—ultimately preparing them to navigate the web safely.
Additionally, On Guard Online provides educational resources that go beyond the confines of the game itself. It encourages open discussions about phishing scams among players, their peers, and family members. This aspect of the game fosters a community of learners where players can share experiences and knowledge, empowering them to spread awareness within their social circles. By facilitating conversations about online safety, the game serves as a bridge between formal education and everyday internet practices, thus reinforcing the importance of cybersecurity in daily life.
The game is also a tool for GOOGLE DELETE PHISING educators and parents, providing them with a framework to teach children about online risks. Schools can integrate On Guard Online into their curricula, offering dedicated sessions on internet safety that are both informative and interactive. Furthermore, the FTC provides educators with guides and discussion prompts that can help facilitate classroom conversations about phishing scams. This collaborative approach ensures that the lessons learned through the game have a wider impact, extending beyond individual experiences to shape collective understanding of digital safety.
Importantly, On Guard Online reflects a growing recognition of the need for proactive strategies in internet safety education. As phishing scams continue to evolve, so too must the tools available for countering them. By adopting a forward-thinking approach, the FTC has addressed a critical gap in current online safety measures. While traditional educational programs often focus on passive learning methods, the interactive gameplay of On Guard Online empowers young users to actively engage with the material, enhancing their ability to retain and apply what they learn.
In conclusion, the FTC’s On Guard Online game represents a significant advancement in the fight against phishing scams targeting young internet users. By utilizing gamification and interactive learning, the FTC not only educates players about the nuances of recognizing phishing attempts but also encourages critical thinking and community engagement around the topic. As young individuals increasingly navigate a complex digital landscape, the skills honed through playing On Guard Online are essential for fostering resilient and informed internet users. This innovative approach marks a promising step forward in enhancing digital literacy and safety, ultimately contributing to a more secure online environment for all. As technology continues to evolve, so too must our educational initiatives to ensure that the next generation is equipped to face the challenges of the digital world.
Phishing is a form of cybercrime that involves deceiving individuals into providing sensitive information such as usernames, passwords, credit card details, and other personal data. This malicious tactic has evolved over the years into a sophisticated method of attack that leverages social engineering and technological advancements to exploit human emotions like fear, curiosity, and trust. As the internet continues to grow, so does the prevalence of phishing attacks, making it imperative for users to understand the nature of this threat, the techniques employed by attackers, and the methods for protection.
The term "phishing" is derived from the word "fishing," implying that cybercriminals are casting a net to catch unsuspecting victims. Typically, phishing involves the use of fraudulent emails or websites designed to appear legitimate, often mimicking well-known organizations such as banks, online services, or social media platforms. These communications usually contain urgent messages that prompt users to click on malicious links, which lead to sites that resemble authentic web pages.
One common type of phishing attack is spear phishing, where attackers target specific individuals or organizations with personalized messages. This approach increases the likelihood of success because the attackers gather information about their victims beforehand, making the content more convincing. For instance, they may reference current projects, mutual acquaintances, or legitimate business accounts, creating a false sense of security.
Another variant is whaling, which specifically targets high-profile individuals within organizations, such as executives or senior management. By using highly tailored messages, whaling attacks aim to extract sensitive corporate information or initiate fraudulent wire transfers. Given the potential financial repercussions and reputational damage, whaling poses a significant risk to companies and their stakeholders.
Phishing has also expanded beyond email, with the emergence of SMS phishing (smishing) and voice phishing (vishing). Smishing involves sending fraudulent text messages that prompt users to provide personal information or click on malicious links. Vishing, on the other hand, is executed through phone calls that impersonate legitimate entities, such as banks or government agencies. These methods leverage technology to reach individuals directly, increasing the persuasion factor in the communication.
The impact of phishing attacks can be severe. Victims may suffer financial losses, identity theft, and unauthorized transactions, while companies can face legal repercussions, loss of customer trust, and data breaches that compromise sensitive corporate information. According to the Anti-Phishing Working Group (APWG), phishing attacks have increased dramatically, with millions of phishing websites reported each year. This growth indicates a pressing need for effective countermeasures.
To combat phishing, GOOGLE DELETE PHISING it is essential for individuals and organizations to implement robust security practices. One of the first steps is to educate users about the risks associated with phishing and how to recognize potential threats. This education includes training programs that cover the common signs of phishing attempts, such as misspelled URLs, generic greetings, and suspicious attachments.
Another critical measure is the adoption of multi-factor authentication (MFA). MFA provides an additional layer of security by requiring users to confirm their identity through multiple means—such as a password followed by a unique code sent to their mobile device—making it more challenging for cybercriminals to gain unauthorized access.
Regularly updating software and security systems is also crucial. Organizations should ensure that all applications, operating systems, and anti-virus software are kept up to date to protect against known vulnerabilities exploited by attackers. Moreover, utilizing advanced email filtering solutions can help detect and block phishing attempts before they reach the user's inbox.
For individuals, verifying the authenticity of communications is vital. Users should take the time to hover over links to inspect their URLs before clicking, avoid providing personal information in response to unsolicited requests, and be vigilant about any correspondence that evokes a sense of urgency or fear. When in doubt, contacting the organization directly using official contact methods can help confirm the legitimacy of the communication.
In conclusion, phishing is a pervasive cyber threat that can lead to significant financial and personal losses if left unchecked. As technology continues to evolve, so do the tactics employed by cybercriminals. Therefore, understanding the nature of phishing, recognizing its various forms, and implementing effective security measures are essential in protecting oneself and one’s organization from this growing threat.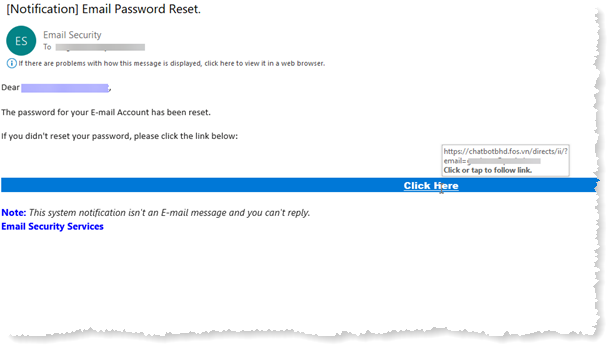 Through education and vigilance, individuals and companies can significantly mitigate the risks associated with phishing and maintain a secure online environment.
Through education and vigilance, individuals and companies can significantly mitigate the risks associated with phishing and maintain a secure online environment.
